TSA Secure Flight RIA
Attachment 12 TSA Secure Flight RIA.docx
Requirement for Airlines and Operators to Collect and Transmit Designated Information for Passengers and Crew Arriving Into the United States
TSA Secure Flight RIA
OMB: 0920-1354
REGULATORY EVALUATION
FINAL RULE
SECURE FLIGHT
(49 CFR 1560)
Regulatory and Economic Analysis
Transportation Sector Network Management
Transportation Security Administration
Department of Homeland Security
October 17, 2008
CONTENTS
Part 1: E.O. 12866 Regulatory Evaluation 9
Section 1: Executive Summary 9
1.1.1 A-4 Accounting Statement 9
1.1.2 Overview of the Analysis 11
Section 2: Terms and Definitions 20
Section 3: Background and Summary of the Rule 23
1.3.1 Background of the Rule 23
1.3.2 Historical PNR Testing Determined Data Collection Requirements 24
1.3.3 Summary of the Final Rule 26
Section 4: Establishing a Baseline: Passenger Air Transportation Today 33
1.4.2 The Airline Reservation Process 46
1.4.3 Watch List Matching Today 53
1.5.2 Improved Security and Additional Access for Non-traveling Individuals 56
1.5.3 Reduced False Positives 57
1.5.4 Airlines Relieved of Watch List Responsibilities 58
1.5.5 More Accurate Matching 59
1.5.6 Increased Watch List Security 60
1.5.7 Consolidated Regulatory Policy 60
1.5.8 Boarding Pass Authentication 60
1.6.2 Airline Reprogramming and Implementation Costs 68
1.6.3 Airline Data Collection Costs 79
1.6.6 Opportunity Costs to Travelers 108
Section 7: Sensitivity Analysis 123
Section 1.7.1 Airline Reservation Time Estimates 123
Section 1.7.2 Domestic Reservations 124
Section 1.7.3 Changes in the Distribution of Reservation Methods 124
Section 1.7.4 Sensitivity Analysis Summary 126
Section 8: Comparison of Costs and Benefits of Regulatory Alternatives 128
Section 1.8.1 Qualitative Alternatives 129
Section 1.8.2 Quantitative Alternatives 131
Section 1.8.3 Comparison of Preferred Alternative Against Timing Variations 137
Part 2: Final Regulatory Flexibility Analysis (FRFA) 164
Section 1: Reasons for and Objectives of the Final Rule 164
2.1.1 Reason for the Final Rule 143
2.1.2 Objective of the Final Rule 143
Section 2: Affected Small Business Population and Estimated Impact of Compliance 144
2.2.1 Aircraft Operator Small Business Population 144
2.2.2 Estimated Impact to Aircraft Operator Small Businesses 146
2.2.3 Travel Agency Small Business Population 150
2.2.4 Estimated Impact to Travel Agency Small Businesses 152
Section 3: Significant Alternatives Considered 154
Section 4: Identification of Duplicative or Overlapping Federal Rules 154
Section 5: Final Determination of No Significant Impact 155
List of Tables
Total and Average Costs (Millions) 12
Changes in Secure Flight Cost Estimates from NPRM Cost Estimates 14
Table 1.4.1.a Covered Carrier Forecasted Enplanements 32
Table 1.4.1.b Large Carrier Revenue Classifications 33
Table 1.4.1.c Count of Secure Flight Domestic Aircraft Operators by BTS Class 33
Table 1.4.1.d Airline vs. GDS/host ARS Reprogramming Effort 36
Table 1.4.1.e Major Secure Flight Implementation Groupings 37
Table 1.4.1.f Secure Flight Large* Domestic Carriers Reporting to APIS 39
Table 1.4.1.g International Enplanement Shares 40
Table 1.4.1.h Projected Secure Flight Covered International Passengers (Millions) 42
Table 1.4.2.a Percent of Roundtrip Itineraries 46
Table 1.4.2.b Covered Carrier Forecasted Domestic Reservations (Millions) 47
Table 1.4.2.c Forecasted Group 4 Reservations 50
Table 1.4.2.d Covered Carrier Forecasted International Reservations (Millions) 51
Table 1.6.1.a Total Secure Flight Costs, Millions of 2005 $ 65
Table 1.6.1.b Total Secure Flight Costs, Discounted 7% and 3% 66
Table 1.6.2.a Initial and Recurring Unit Costs, Domestic Marketing Carriers 70
Table 1.6.2.b Total Initial and Recurring Marketing Carrier Costs, Domestic High Scenario 70
Table 1.6.2.c Total Initial and Recurring Marketing Carrier Costs, Domestic Low Scenario 70
Table 1.6.2.d Total Domestic Reprogramming and Implementation Costs (millions of 2005 $) 71
Table 1.6.2.e Total Initial and Recurring Carrier Costs, Foreign High Scenario 74
Table 1.6.2.f Total Initial and Recurring Carrier Costs, Foreign Low Scenario 75
Table 1.6.2.g Potential Secure Flight Message Fees (millions of 2005 $) 76
Table 1.6.2.h Total Foreign Reprogramming and Implementation Costs (millions of 2005 $) 76
Table 1.6.3.a Cost of Data Collection for Airline Reservation Call Centers, Domestic Passengers 78
Table 1.6.3.c Cost of Data Collection for Airline Reservation Call Centers, Overflights 82
Table 1.6.4.a Travel Agency Data Collection Costs, Domestic Passengers 84
Table 1.6.4.b Travel Agency Data Collection Costs, International Passengers 86
Table 1.6.4.c Travel Agency Data Collection Costs, Overflight Passengers 87
Table 1.6.4.e Total Costs of Training for Travel Agencies (millions) 88
Table 1.6.4.f Total Costs of Reprogramming Travel Agency Electronic Profiles (millions) 89
Table 1.6.5.a TSA Direct Costs to Operate and Maintain Secure Flight (millions of 2005 $) 93
Table 1.6.5.b Calculation of Inventory Needed 95
Table 1.6.5.c Barcode Scanning Inventory Costs 96
Table 1.6.5.d Cost to Synchronize Scanners 96
Table 1.6.5.e Cost to Scan Barcodes with Synchronized Scanners, Primary Scenario (Millions) 97
Table 1.6.5.f Cost of Real Time Communication (millions) 98
Table 1.6.5.g Cost to Scan Barcodes Against Secure Flight Database in Real Time (Millions) 98
Table 1.6.5.h Total Costs to Verify Boarding Pass Information 99
Table 1.6.5.i Total Direct Costs to TSA 99
Table 1.6.5.j Estimated TSC Costs 101
Table 1.6.5.k Estimated Total Federal Government Costs (millions of 2005 $) 101
Table 1.6.6.a Domestic Passenger Reservation Opportunity Costs (Primary Scenario) 103
Table 1.6.6.b Domestic Passenger Reservation Opportunity Costs (Low Scenario) 104
Table 1.6.6.c Passenger Reservation Opportunity Costs, Domestic Passengers (High Scenario) 104
Table 1.6.6.d Total Domestic Passenger Opportunity Costs, Groups 1 - 3 105
Table 1.6.6.e Total Domestic Passenger Opportunity Costs, Group 4 106
Table 1.6.6.f Total Domestic Passenger Opportunity Costs 106
Table 1.6.6.g Passenger Reservation Opportunity Costs, International Passengers (Primary) 109
Table 1.6.6.h Passenger Reservation Opportunity Costs, International Passengers (Low Scenario) 110
Table 1.6.6.i Passenger Reservation Opportunity Costs, International Passengers (High Scenario) 110
Table 1.6.6.j Passenger Reservation Opportunity Costs, Over-Flights (Primary Scenario) 111
Table 1.6.6.k Small Foreign Carrier Passenger Opportunity Costs 112
Table 1.6.6.l Total Marginal Opportunity Cost for Passengers (millions) 112
Table 1.6.6.m Passenger Opportunity Costs of Secure Flight Complexity Risks 113
Table 1.7.4.a Summary of Sensitivity Analysis Results (Millions of $) 117
Table 1.8.1.a Qualitative Comparison of Regulatory Alternatives 121
Table 1.8.2.a Quantitative Comparison of Regulatory Alternatives 127
Table 1.8.3.a Qualitative Comparison of Regulatory Timing Alternatives 138
Table 1.8.3.b Quantitative Comparison* of Regulatory Timing Alternatives 140
Table 2.2.1.a Secure Flight Small Business Air Carriers (2005 Data) 146
Table 2.2.2.a Estimated Small Business Impact, Carrier Groups 2 and 3 148
Table 2.2.2.b Illustrative Small Business Impact, Carrier Group 4 150
Table 2.2.3.a Distribution of Travel Agencies (NAICS 561510) by Revenue, 2003 151
Table 2.2.3.b Number of Travel Agencies by Size Category 152
Table 2.2.3.c Share of Travel Agent Sales by Size Category 152
Table 2.2.4.a Airline Reservations Threshold for Small Business Travel Agencies 154
Changes to Federal regulations must undergo several economic analyses. First, Executive Order 12866, Regulatory Planning and Review (58 FR 51735, October 4, 1993), directs each Federal agency to propose or adopt a regulation only upon a reasoned determination that the benefits of the intended regulation justify its costs. Second, the Regulatory Flexibility Act of 1980 (5 U.S.C. 601 et seq., as amended by the Small Business Regulatory Enforcement Fairness Act (SBREFA) of 1996) requires agencies to analyze the economic impact of regulatory changes on small entities. Third, the Trade Agreements Act (19 U.S.C. § 2531-2533) prohibits agencies from setting standards that create unnecessary obstacles to the foreign commerce of the United States. In developing U.S. standards, this Trade Act requires agencies to consider international standards and where appropriate, as the basis of U.S. standards. Fourth, the Unfunded Mandates Reform Act of 1995 (2 U.S.C. 1531-1538) requires agencies to prepare a written assessment of the costs, benefits, and other effects of proposed or final rules that include a Federal mandate likely to result in the expenditure by State, local, or tribal governments, in the aggregate, or by the private sector, of $100 million or more annually (adjusted for inflation).
With respect to these analyses, TSA concluded the following:
TSA has determined that this is an economically significant rule within the definition of Executive Order (EO) 12866, as estimated annual costs or benefits exceed $100 million in any year.
The Final Regulatory Flexibility Analysis (FRFA) shows that there is not likely a significant impact on a substantial number of small entities.
Although the rule in general is unlikely to cause any adverse impact on international trade, there may be potential unfavorable responses to the overflight provisions of the rule.
The regulatory evaluation provides the required written assessment of Unfunded Mandates. The rule is not likely to result in the expenditure by State, local, or tribal governments, in the aggregate, of $100 million or more annually (adjusted for inflation). However, the estimated impact on the private sector does exceed the inflation adjusted Unfunded Mandates threshold. The E.O. 12866 analysis provided below also serves as the analysis required under UMRA.
Part 1: E.O. 12866 Regulatory Evaluation
1.1.1 A-4 Accounting Statement
TSA has determined that this is an economically significant rule within the definition of Executive Order (EO) 12866, as estimated annual costs or benefits exceed $100 million in any year. As required by OMB Circular A-4 (available at http://www.whitehouse.gov/omb/circulars/index.html), TSA has prepared an accounting statement showing the classification of expenditures associated with the operation, testing, and initial implementation of Secure Flight.
OMB A-4 ACCOUNTING STATEMENT
(Numbers in $ millions, 2005 constant)
OMB #: Agency/Program Office: Transportation Security Administration
Rule Title: Secure Flight Date: March 31, 2008
RIN#: 1652-AA45
Category |
Primary Estimate |
Minimum Estimate |
Maximum Estimate |
Source Citation (RIA, preamble, etc.) |
BENEFITS |
||||
Monetized Benefits |
None |
N/A |
N/A |
RIA |
Annualized quantified, but unmonetized, benefits |
None |
N/A |
N/A |
RIA |
Unquantified Benefits |
The following will occur after TSA assumes the watch list matching function from covered aircraft operators:
|
RIA |
||
COSTS |
||||
Annualized monetized costs (discount rate in parenthesis) |
$327.7 (7%) |
$290.3 (7%) |
$383.5 (7%) |
RIA |
$326.8 (3%) |
$289.6 (3%) |
$382.7 (3%) |
||
$326.2 (0%) |
$289.2 (0%) |
$382.2 (0%) |
||
Annualized quantified, but unmonetized, costs |
0 (7%) 0 (3%) 0 (0%) |
0 (7%) 0 (3%) 0 (0%) |
0 (7%) 0 (3%) 0 (0%) |
RIA |
Qualitative (unquantified) costs |
|
RIA |
||
TRANSFERS |
||||
Annualized monetized transfers: “on budget” |
None |
None |
None |
RIA |
Annualized monetized transfers: “off-budget” |
None |
None |
None |
RIA |
MISCELLANEOUS ANALYSES |
||||
Effects on State, local, and/or tribal governments |
None |
RIA |
||
Effects on small businesses |
The Final Regulatory Flexibility Analysis (FRFA) shows that there is not likely a significant impact on a substantial number of small entities |
RIA |
||
Effects on wages |
None |
None |
||
Effects on growth |
None |
None |
||
1.1.2 Overview of the Analysis
Summary of Rule
Section 4012(a) of the Intelligence Reform and Terrorism Prevention Act requires the Department of Homeland Security (DHS) and the Transportation Security Administration (TSA) to assume from aircraft operators the function of conducting pre-flight comparisons of airline passenger information to Federal Government watch lists. TSA is currently developing Secure Flight to implement this Congressional mandate. This final rule allows TSA to begin implementation of Secure Flight, under which TSA will receive passenger and certain non-traveler information, conduct watch list matching, and transmit gate and boarding pass printing instructions back to aircraft operators indicating whether individuals should be cleared to enter the sterile area, marked as selectees, or prohibited from receiving a boarding or gate pass. Under the final rule, TSA will fully assume the domestic watch list matching function from aircraft operators after conducting operational testing with each aircraft operator during a first implementation phase. Following this initial domestic implementation phase, TSA will assume from the U.S. Customs and Border Protection (CBP) the responsibility for comparing passenger information to government watch lists for certain domestic and foreign aircraft operators flying to, from, and over the United States.
Under this final rule, TSA requires covered aircraft operators to request and transmit to TSA each passenger’s full name, date of birth, gender, and, if available, Redress Number, Known Traveler Number, and passport information. Covered aircraft operators will request and transmit to TSA an identical set of data elements from non-traveling individuals seeking authorization to enter an airport sterile area (such as to escort a minor or passenger with disabilities). While the rule requires covered aircraft operators to request these data elements, provision by passengers and non-traveling individuals of all elements but full name, date of birth and gender will remain voluntary.
Additionally, covered aircraft operators must transmit to TSA certain non-personally identifiable information such as itinerary information and record locator numbers. The following chart details the information that TSA requires covered aircraft operators to request from passengers and certain non-traveling individuals, the information that those individuals are required to provide, and the information covered aircraft operators must transmit to TSA if available. In the case of non-traveling individuals, airlines will send the airport code for the sterile area the individual seeks to enter.
Information Collection Requirements for Secure Flight
Data Elements |
Covered Aircraft Operators Must Request from Passengers and Certain Non-Travelers |
Passengers and Certain Non-Travelers Must Provide at Time of Reservation |
Covered Aircraft Operators Must Transmit to TSA if Available |
Full Name |
X |
X |
X |
Date of Birth |
X |
X |
X |
Gender |
X |
X |
X |
Redress Number or Known Traveler Number |
X |
|
X |
Passport Information1 |
|
|
X |
Itinerary Information2 |
|
|
X |
Reservation Control Number |
|
|
X |
Record Sequence Number |
|
|
X |
Record Type |
|
|
X |
Passenger Update Indicator |
|
|
X |
Traveler Reference Number |
|
|
X |
TSA will compare each passenger’s and non-traveler’s data to the Federal Government’s consolidated watch lists and return a gate or boarding pass printing instruction to covered aircraft operators. If TSA is unable to differentiate an individual from a person on the Terrorist Screening Center’s (TSC) Selectee or No Fly lists, covered aircraft operators must require the individual to present an unexpired government-issued photo ID with the individual’s full name and date of birth. The aircraft operator will submit to TSA additional identifying data from that identification in order to complete the watch list matching process. In the event TSA cannot distinguish the individual from the person on the Selectee or No Fly Lists, TSA will direct the aircraft operator to deny the individual boarding and entry into the sterile area.
To ensure the integrity of the boarding pass printing results and to prevent use of fraudulent boarding passes, TSA will also provide instructions for placing separate bar codes on the boarding passes in the future in accordance with TSA instructions.3 The Secure Flight system will automatically generate a unique code for each watch list result returned to covered aircraft operators. Aircraft operators will be required to print this code separately from any other bar or optical code currently printed on a boarding or gate pass. Personnel at security checkpoints will use this code to verify the authenticity of the boarding pass. Depending upon its final implementation, security personnel may also use the code to verify that the ID presented at the checkpoint matches the information submitted to the Secure Flight system for that boarding or gate pass.
Finally, the rule requires covered aircraft operators to take reasonable steps to make available a privacy notice to individuals on a website or self-service kiosk informing them why the information described above is being collected, how it will be used, and that provision of the requested information is voluntary.
Costs
All costs in the following summary are discounted present value costs using a 7% discount rate over 10 years unless noted as an annual cost. The table below provides totals in constant 2005 dollars as well as totals discounted at 7% and 3%. Cost tables in Section 6 of the regulatory evaluation present year-by-year costs in constant 2005 dollars. Both in this summary and the economic evaluation, descriptive language conveys the consequences of the regulation. Although the regulatory evaluation attempts to mirror the terms and wording of the regulation, no attempt is made to precisely replicate the regulatory language and readers are cautioned that the actual regulatory text, not the text of the evaluation, is binding.
Given the global nature of commercial aviation and the prevalence of airline partnerships, TSA was unable to divide the incidence of the estimated costs between the domestic and foreign economies. Thus, the table below presents the aggregate costs attributable to the Secure Flight final rule. TSA has divided its discussion within each of the cost sections in the regulatory evaluation between domestic and international operations, reflecting the scope and phasing of the rule. However, this distinction between costs accruing to domestic and international operations should not be confused with costs to the domestic and foreign economies.
Total and Average Costs (Millions) |
|||||
Cost Category |
Average Annual Costs, undiscounted |
Average Annual Costs, discounted 3% |
Average Annual Costs, discounted 7% |
10 Year Total Costs, discounted 3% |
10 Year Total Costs, discounted 7% |
(Low – High) |
(Low – High) |
(Low – High) |
(Low – High) |
(Low – High) |
|
Air Carrier Reprogramming Costs |
$36.2 - $63.5 |
$38.6 - $66.3 |
$41.8 - $70.0 |
$329.5 - $565.3 |
$293.8 - $491.8 |
Airline Collection Costs |
$10.5 - $15.7 |
$10.4 - $15.5 |
$10.3 - $15.3 |
$88.6 - $132.4 |
$72.2 - $107.8 |
Travel Agency Costs |
$26.1 - $39.4 |
$26.0 - $39.3 |
$26.0 - $39.3 |
$221.9 - $278.8 |
$182.4 - $276.1 |
Federal Costs |
$137.0 - $167.5 |
$135.9 - $166.2 |
$134.4 - $164.5 |
$1,159.3 - $1,418.0 |
$943.9 - $1,155.7 |
Outlay Subtotal Costs |
$209.8 - $286.1 |
$210.9 - $287.3 |
$212.5 - $289.2 |
$1,799.3 - $2,451.0 |
$1,492.4 - $2,031.3 |
Passenger Opportunity Costs |
$79.4 - $96.2 |
$78.7 - $95.3 |
$77.8 - $94.3 |
$671.3 - $813.1 |
$546.5 - $662.0 |
Total Costs |
$289.2 - $382.2 |
$289.6 - $382.7 |
$290.3 - $383.5 |
$2,470.5 - $3,264.1 |
$2,038.9 - $2,693.3 |
TSA estimated a range of possible costs to reflect uncertainty in TSA’s assumptions about the additional time the rule adds to the airline reservation process. The summary table above presents the minimum and maximum of this range. TSA did not have sufficient information from industry, however, to determine a likely cost distribution; therefore, the minimum and maximum should be taken as extremes, with the actual cost falling somewhere in between.
TSA estimated the cost impacts of this rulemaking will total from $2.039 billion to $2.693 billion over 10 years, discounted at 7%. At the 7% discount rate, air carriers will incur total costs of $366.0 million to $599.6 million, and travel agents will incur costs of $182.4 to $276.1 million. TSA projected Federal Government costs will be from $943.9 million to $1.156 billion. The total cost of outlays by all parties, discounted at 7%, will be from $1.492 billion to $2.031 billion. Additionally, the opportunity costs to individuals (value of time), discounted at 7%, will be between $546.5 and $662.0 million. The following paragraphs discuss these costs.
Air carriers will incur costs to comply with requirements of this rulemaking. Over the 10-year period from 2008 to 2017, TSA estimated air carriers will incur average annual costs of $41.8 to $70.0 million, discounted at 7%, to reprogram their computer systems to accommodate the additional data fields required by the rule and achieve two-way connectivity with TSA and the recurring costs to operate and maintain system modifications. Because the rule requires air carriers to request additional information from passengers, additional time will be required for airline call centers to complete reservations. TSA estimated these costs will be between $10.3 and $15.3 million per year. Together, the air carriers’ discounted average annual costs will range from $52.1 to $85.3 million.
The rule does not directly regulate travel agents. However, the rule requires aircraft operators to ensure that travel agencies request the additional passenger information. Therefore, travel agents, like covered aircraft operators, have to spend additional time to complete airline reservations. TSA estimated the average annual cost to travel agents, discounted at 7%, will range from $26.0 to $39.3 million.
The Federal Government incurs several costs as a result of the rule. These costs include network infrastructure to enable communication between TSA and covered aircraft operator data systems, hardware and software procurement, operations and maintenance, and general support for implementation. The government further incurs costs to complete adjudication of name similarities or watch list matches and also for redress activities. Finally, the government incurs costs to implement a system at checkpoints to verify the codes issued by the Secure Flight system and printed on boarding and gate passes. The government’s estimated average annual cost, discounted at 7%, will be from $134.4 million ($137.0 million, undiscounted) to $164.5 million ($167.5 million, undiscounted).
The final rule also impacts individuals. Time is a valuable economic resource, like labor, capital, and other factors of production, which may be utilized for work or relaxation. The loss of time imposes an opportunity cost on individuals. TSA attempted to quantify opportunity costs to individuals based on the incremental additional time required to make a reservation. TSA estimated the average annual cost to individuals, discounted at 7%, will range from $77.8 ($79.4 million, undiscounted) to $94.3 million ($96.2 million, undiscounted).
Due to program refinements and information provided in public comments, these cost estimates differ in some respects from those reported in the Secure Flight NPRM. The table below identifies these cost differences and their origins, by the entity bearing the cost.
Changes in Secure Flight Cost Estimates from NPRM Cost Estimates |
||||
Cost Component |
Undiscounted 10 Year Total Costs ($millions) |
|
||
NPRM |
Final Rule |
Difference |
Notes |
|
Reprogramming Costs to Carriers |
$318.5 |
$498.8 |
$180.3 |
In response to public comments, carrier reprogramming costs for Secure Flight were increased |
Airline Data Collection Costs |
$104.8 |
$130.7 |
$25.9 |
In response to public comments, average data collection time for obtaining Secure Flight data elements during telephone reservations was increased from 20 seconds to 25 seconds |
Travel Agency Reprog / Training Costs |
n/a |
$16.7 |
$16.7 |
In response to public comments, first year costs for travel agent training and reprogramming costs for larger travel agencies were included. |
Travel Agency Data Collection Costs |
$249.0 |
$310.7 |
$61.7 |
In response to public comments, average data collection time for obtaining Secure Flight data elements during telephone reservations was increased from 20 seconds to 25 seconds |
Federal Costs |
$1,670.3 |
$1,427.5 |
($242.8) |
Program costs revised based on redesign of process flow at resolution service centers; costs change principally in Implementation, Operations Planning and Service Center cost areas |
Total Cash Outlay |
$2,342.6 |
$2,384.4 |
$41.8 |
|
Passenger Opportunity Costs |
$787.3 |
$877.9 |
$90.5 |
In response to public comments, average time to provide Secure Flight data elements during telephone reservations was increased from 20 seconds to 25 seconds; added complexity risk |
Total Program Costs |
$3,129.9 |
$3,262.3 |
$132.4 |
|
Benefits
Benefits of the rule will occur in two phases: the first during operational testing and the second post-implementation. During operational testing, Secure Flight will screen passengers in parallel with the airlines. Primary responsibility for watch list matching will remain with covered aircraft operators during this period, but Secure Flight may notify aircraft operators if its watch list matching technology enables it to detect a potential match the aircraft operator may have missed. Therefore, during the operational testing phase, benefits may include increased aviation security resulting from the detection of threats not identified by covered carriers participating in the testing.
Most of the rule’s benefits occur post-implementation. Secure Flight standardizes the watch list matching process across domestic and foreign commercial airlines. Resulting benefits will include more accurate, timely, and comprehensive screening, and a reduction in false positives. This occurs because Secure Flight has access to more initial data with which to distinguish passengers from records in the watch lists than is currently available to airlines. Further, the airlines will be relieved of watch list matching responsibilities, and TSA will be relieved of distributing the watch lists. Together, these factors contribute to the overall objective of focusing resources on passengers identified as potential threats to aviation security.
This benefit is further augmented by the requirement that covered airlines must print on boarding passes a code generated by the Secure Flight system that is unique for each watch list result returned. Depending on the final implementation method, this requirement will at a minimum allow checkpoint personnel to verify that a boarding or gate pass has been processed by the Secure Flight system. This will prevent individuals from passing through the checkpoint with a boarding or gate pass that has not originated in an airline system.
By transferring responsibility for watch list matching of international passengers from CBP to TSA, the final rule consolidates passenger prescreening operations within the Department of Homeland Security (DHS), thereby reducing redundancies between similar programs and facilitating better governance. The rule enables CBP to focus its resources on its mission of protecting U.S. borders while permitting TSA to apply its expertise in watch list matching consistently across all commercial air traffic within and overflying the United States. DHS expects that reducing overlap between these agencies’ missions will improve national security through more efficient and targeted use of national resources.
Other benefits include increased security due to the watch list matching of non-traveling individuals who request access to a sterile area. Also, TSA anticipates it may allow airports to authorize non-traveling individuals to enter the airport sterile area. As a result, the final rule establishes requirements related to airports’ transmission of data from non-traveling individuals to Secure Flight for watch list matching. These requirements only apply to airports that request and receive authorization from TSA to grant non-traveling individuals access to the airport sterile area.
Once TSA assumes primary responsibility for watch list matching, airlines will be relieved of their passenger watch list matching responsibilities. For the purpose of the estimates in this analysis, TSA assumed that domestic implementation will be completed in the first year of the rule and international implementation will be completed in the second year. However, the actual date the carriers will be completely relieved is unknown and is contingent on several factors, such as the impact of budgetary constraints and the results of operational testing. Prior to full implementation, operational testing will have to demonstrate that Secure Flight does not produce a large number of false positives, processes all matching requests in an efficient and accurate manner, and interfaces with a redress system for passengers who believe they have been incorrectly delayed or denied boarding as a result of Secure Flight matching. Elimination of their watch list matching responsibilities enables airlines to reallocate to other tasks some of their operational resources currently dedicated to comparing passenger information to the watch lists and will offset some costs imposed by the regulation. Due to the vast difference in resources used by each airline for watch list matching and uncertainty regarding the actual date each will be relieved of watch list duties, TSA was unable to quantify these cost savings.
Further, while TSA conducted significant testing using previously collected passenger name record (PNR) data, no testing has been completed using all of the passenger information required by this final rule. The operational testing phase provides TSA the opportunity to work with the airlines and other stakeholders to refine Secure Flight to achieve optimal results while the airlines continue to have primary responsibility for watch list matching. Thus, the testing phase also allows TSA to collect baseline data necessary for quantification of potential benefits of Secure Flight.
TSA has also included a “break-even” analysis which indicates the tradeoffs between program cost and program benefits (in the form of impact on baseline risk of a significant aviation-related terror attack) that would be required for Secure Flight to be a cost beneficial undertaking.
Section 2: Terms and Definitions
Terms and definitions important to understanding the following analysis are provided here for the reader’s convenience. Definitions are not repeated in the text.
Aircraft Operator Implementation Plan (AOIP) - A written procedure describing how and when a covered aircraft operator transmits passenger and flight information and non-traveler information to TSA, as well as other related matters.
Airport code – The official code, designated by the International Air Transport Association (IATA), for an airport.
Covered Aircraft Operator - Each aircraft operator required to carry out a full security program under 49 CFR 1544.101(a) (domestic operators) or a security program under 49 CFR 1546.101(a) or (b) (foreign operators).
Covered Airport Operator - Each airport operator that seeks to authorize non-traveling individuals to enter a sterile area for a purpose permitted by TSA. “Airport operator” is defined in § 1540.5 as a person that operates an airport serving an aircraft operator or a foreign air carrier required to have a security program under 49 CFR parts 1544 or 1546.
Covered Flight - Flights for which TSA will conduct passenger watch list matching under this rule. This rule covers any operation of a U.S. aircraft operator that is subject to or operated under a full program under 49 CFR 1544.101(a). This includes flights operated by such aircraft operators anywhere in the world. “Covered flight” also means any operation of a foreign air carrier subject to or operated under a security program under 49 CFR 1546.101(a) or (b) arriving in, departing from, or overflying the United States. Covered flight does not include any flight for which TSA has determined that the U.S. Government is conducting passenger matching comparable to the matching conducted pursuant to this part.
Date of Birth – The day, month, and year of an individual’s birth.
Enplanement – A statistic recording the number of passengers transported aboard a single aircraft between two points. For example, a passenger flying from Des Moines to Washington, D.C. who transfers in St. Louis to a plane with a different flight number is counted as two enplanements. If the stop in St. Louis is only a stopover and the passenger continues to Washington aboard the same flight number, this is counted as only one enplanement.
False Positive - An individual whose information is incorrectly matched with the information of an individual on the consolidated government watch list.
Full Name – An individual’s full name as it appears on an acceptable form of government-issued photo identification with date of birth held by the individual that the individual will present at check-in, if requested.
Global Distribution System (GDS) – For the purposes of this analysis, the term GDS is used to refer to a network of computer systems serving as an interface between travel agency booking systems and airline reservation systems. As part of this service, GDS providers also manage the reservation systems of subscribing airlines.
Host Airline Reservation System (ARS) – For the purposes of this analysis, the term ARS is used to refer to a computer system that provides reservation services for an airline. This system may be owned and maintained directly by an airline or it may refer to a third-party system providing such services for several airlines. An ARS differs from a GDS in that it does not interface with travel agent systems.
Itinerary information – The information reflecting a passenger’s or non-traveling individual’s itinerary specified in the covered aircraft operator’s AOIP. For non traveling individuals, itinerary information is the airport code for the sterile area to which the non-travler seeks access. For passengers, itinerary information includes the following: (1) departure airport code, (2) aircraft operators, (3) departure date, (4) departure time, (5) arrival date, (6) scheduled arrival time, (7) arrival airport code, (8) flight number, (9) operating carrier, if available.
Known Traveler Number – A unique number assigned to individuals for whom the Federal Government has conducted a threat assessment and determined do not pose a security threat.
Marketing Carrier – An aircraft operator accepting reservations directly from the public, sometimes on behalf of other airlines either owned by or under contract with the marketing carrier to transport passengers to destinations not served by the marketing airline.
Non-traveling individual – An individual to whom a covered aircraft operator or covered airport operator seeks to issue an authorization to enter the sterile area of an airport in order to escort a minor or a passenger with disabilities or for some other purpose permitted by TSA. This term does not include employees or agents of airport or aircraft operators or other individuals whose access to a sterile area is governed by another TSA regulation or security directive.
Overflying the continental United States (US) – An aircraft departing from an airport or location outside the US and transiting the airspace of the continental US en route to another airport or location outside the US. Airspace of the continental US includes the airspace over the lower 48 states of the US, not including Alaska or Hawaii, and the airspace overlying the territorial waters between the US coast of the lower 48 states and 12 nautical miles from the continental US coast. Overflying the continental US does not apply to: (1) flights that transit the airspace of the continental US between two airports or locations in the same country, where that country is Canada or Mexico; or (2) any other category of flights that the Assistant Secretary of Homeland Security (Transportation Security Administration) designates in a notice in the Federal Register.
Passenger Name Record (PNR) – A record maintained by or for an aircraft operator that contains detailed information about an individual’s travel on a particular flight, including information provided by the passenger when making the flight reservation. Though the content of PNRs varies among airlines, PNRs may include, among other information: (1) passenger name; (2) reservation date; (3) travel agency or agent; (4) travel itinerary information; (5) form of payment; (6) flight number; and (7) seating location.
Passport Information – The following information from an individual’s passport: (1) passport number; (2) country of issuance; (3) expiration date; (4) gender; and, (5) full name.
Redress Number – The number assigned by TSA to an individual through the redress process provided in 49 CFR § 1560, subpart C.
Secure Flight Passenger Data (SFPD) – Information for a passenger or a non-traveling individual that a covered aircraft operator or a covered airport operator transmits to TSA, to the extent available, for the purpose of watch list matching.
Self-service kiosk – A kiosk operated by a covered aircraft operator that is capable of accepting a passenger reservation or a request for authorization to enter a sterile area from a non-traveling individual.
Sterile Area – An area of an airport, defined in 49 CFR 1540.5, with access limited to persons who have undergone security screening by TSA.
Terrorist Screening Center (TSC) – The entity responsible for maintaining the consolidated Federal Government terrorist watch lists and providing for the appropriate and lawful use of terrorist information in screening processes. The TSC is under the jurisdiction of the Federal Bureau of Investigation (FBI) and was established by the Attorney General in support of Homeland Security Presidential Directive 6 (HSPD-6), dated September 16, 2003.
Terrorist Screening Database (TSDB) – The Federal Government’s consolidated terrorist watch list. The TSDB is maintained by the Terrorist Screening Center (TSC).
Verifying Identity Document – An unexpired passport issued by a foreign government or an unexpired document issued by a US Federal, State, or tribal government that includes the following information for the individual: (1) full name, (2) date of birth, and (3) photograph.
Watch List – The No Fly and Selectee List components of the Terrorist Screening Database maintained by the Terrorist Screening Center. For certain flights, the “watch list” may include the larger set of watch lists maintained by the Federal Government as warranted by security considerations.
Section 3: Background and Summary of the Rule
In its July 2004 report on the terrorist attacks of September 11, 2001, the National Commission on Terrorist Attacks Upon the United States (9/11 Commission) recommended that the Federal Government assume from aircraft operators the function of comparing passengers against the No Fly and Selectee Lists:
“…improved use of “no-fly” and “automatic selectee” lists should not be delayed while the argument about a successor to CAPPS continues. This screening function should be performed by TSA. . . .” (The 9/11 Commission Report, 393).
As part of this recommendation, the 9/11 Commission also stated that “[a]ir carriers should be required to supply the information needed to test and implement this new system.”
Congress included these recommendations of the 9/11 Commission under Section 4012(a)(1) of the Intelligence Reform and Terrorism Prevention Act (IRTPA) of 2004. The IRTPA requires TSA to develop “an advanced passenger prescreening system” to assume from domestic air carriers the function of conducting pre-flight comparisons of airline passenger information to the consolidated Federal Government watch lists. The final rule thus allows TSA to begin implementation of a watch list matching system known as Secure Flight in accordance with the IRTPA mandate. Before assuming the watch list matching function from an aircraft operator, TSA will conduct operational testing in order to assess Secure Flight’s ability to receive passenger and non-traveler information, conduct watch list matching, and transmit gate and boarding pass printing instructions back to aircraft operators indicating whether individuals should be cleared to enter the sterile area, marked as selectees, or prohibited from receiving a boarding or gate pass.
It is important to note that before Secure Flight becomes fully operational, it first has to satisfy seven requirements under the IRTPA. Of those, three are critical to understanding the following analysis:
Ensure that the system will not produce a large number of passengers incorrectly chosen for extra screening (false positives);
Establish a redress procedure to enable airline passengers who believe they have been erroneously delayed or prohibited from boarding a flight as a result of the matching system to appeal the determination and correct any personal information contained in the system; and,
Ensure that there are no specific privacy concerns with the technological architecture of the system.
1.3.2 Historical PNR Testing Determined Data Collection Requirements
In November 2004, TSA ordered domestic airlines operating under a full security program (49 CFR 1544.101(a)) to submit to TSA all historical PNRs relating to passenger travel in June 2004. Although 66 airlines submitted PNRs, only 27 did so in an electronic format usable for testing. From November 2004 to April 2005, TSA used those historical records to conduct controlled tests of Secure Flight’s ability to match names contained in airline PNRs against the consolidated government watch lists. The primary purpose of these tests was to evaluate whether the information already present in PNRs was sufficient for Secure Flight to accurately compare names against the Federal watch lists. If not, further tests were to determine the minimum additional data fields TSA would need to collect in order to minimize the number of false positive matches selected by the system.
Tests conducted using a representative sample of historical PNRs from contributing airlines demonstrated that Secure Flight could extract enough information to perform name-based watch list matching. This is the type of matching currently performed by most commercial airlines. Comparison of the data recorded in the PNRs, however, revealed considerable diversity in both the amount of information collected by reservation agents on behalf of airlines and the way this information was stored in the PNRs. For example, some airlines required only a passenger’s first initial and full last name in order to place a reservation. In other cases, one carrier’s airline reservation system (ARS) would store a passenger’s first and middle names in separate fields in the PNR while another would concatenate them into a single field.
To better understand the impact of these varying formats and information content on matching, TSA analysts conducted matching tests with PNRs from each airline. The results indicated an apparent correlation between the quality of the PNR data and the number of records selected by the system as potential matches to the watch lists. Consequently, TSA determined a standardized format for collecting passenger names is necessary in order to ensure consistent and accurate watch list matching across all airlines.
As a result, the final rule requires airlines to request from passengers their full names, dates of birth and gender; and to send this information to TSA in UN/EDIFACT or XML format, or an alternative format approved by TSA. TSA sought to minimize the cost of this requirement by consulting with the airlines and choosing a data format already accepted by and prevalent within the industry.
Tests using the historical PNR information also focused on Secure Flight’s ability to minimize the number of false positives, as mandated by the IRTPA. Narrowing the pool of passengers requiring human review allows TSA to focus its resources on catching possible terrorists while reducing inconvenience for travelers. By directing airlines to request from passengers one or two common data elements at the time of reservation, TSA anticipates it can significantly reduce the number of passengers delayed at the ticket counter due to a possible watch list match.
Based on the tests conducted using historical PNR information and TSA’s experience in conducting security threat assessments on other populations, TSA determined that date of birth, passport information, and gender are the data elements in addition to an individual’s full name that are most useful for performing automated matching. Consequently, TSA determined that collecting this information at the beginning of the reservation process allows Secure Flight to eliminate many false positives without human review. Since relatively few Americans travel with passports when flying domestically, TSA is not requiring airlines to request passport information during the reservation process. If a passenger has provided this data, however, as in the case of a passenger flying internationally as part of his or her itinerary, airlines will be required to transmit the passport information to TSA.
TSA also conducted initial testing of the use of commercial data to “test the Government’s ability to verify the identities of passengers using commercial data and to improve the efficacy of watch list comparisons by making passenger information more complete and accurate using commercial data.”4 These tests did not yield conclusive results, and TSA determined it will not use commercial data in the program.
The testing completed to date has enabled TSA to compare the effects of varying passenger data quality and to make determinations about what data elements are most effective in conducting watch list matching. These tests did not enable TSA to quantify post-implementation selectee rates for this analysis, however. For example, the testing of historical PNR data did not try to approximate an operational environment where TSA was dynamically receiving and sending live passenger data. Moreover, as discussed above, these tests were conducted using data from 27 of the 66 airlines that submitted passenger data to TSA; the remaining data were submitted in unusable formats. TSA intends to establish match rates during operational testing with aircraft operators. TSA will utilize the first phase to create benchmark data upon which to compare match rates in the future.
1.3.3 Summary of the Final Rule
The rule covers all flights conducted by covered U.S. aircraft operators, and all flights conducted by a covered foreign air carrier arriving in, departing from, or overflying the United States. However, for the purposes of implementation, these flights have been divided into two categories or phases.
The first phase of Secure Flight focuses on assuming the watch list matching function for covered U.S. aircraft operators with respect to all flights that depart from and arrive in points within the United States.
The second phase of Secure Flight focuses on assuming the watch list matching function for flights of covered U.S. aircraft operators with respect to all flights that depart from and/or arrive in points outside the United States, as well as flights operated by covered foreign air carriers that depart from or arrive in points within the United States or that overfly the United States.
Dividing deployment into these phases not only provides for a more manageable implementation but also recognizes the differences associated with addressing international flights. On the one hand, since CBP is requiring covered air carriers operating international flights to collect and transmit passenger information to CBP for watch list matching prior to the departure of an international flight under its 2007 APIS pre-departure final rule, TSA will assume the watch list matching function for covered international flights from CBP, not from the air carriers. On the other hand, with this rule, TSA also extends passenger watch list matching to all flights of covered foreign air carriers that overfly the United States.
The implementation process will begin with TSA sending to each covered aircraft operator a proposed Aircraft Operator Implementation Plan (AOIP) for that covered aircraft operator. After receiving the proposed AOIP from TSA, the covered aircraft operator will have 30 days to submit written comments on the proposed AOIP. After the covered aircraft operator reviews the proposed AOIP and submits its comments, TSA will review the comments and finalize the AOIP making any necessary changes. TSA will then issue the finalized AOIP to the covered aircraft operator. The AOIP will be effective not less than 30 days after notice is given, unless the covered aircraft operator petitions TSA for reconsideration of the AOIP. In no case will an AOIP become effective prior to the effective date of the Final Rule. Upon notification by TSA of the AOIP, the covered aircraft operator may petition for reconsideration of the AOIP no later than 15 days before its effective date. A timely reconsideration petition will stay the effective date of the AOIP. TSA will amend, affirm or withdraw the AOIP within 30 days of receipt of the petition for reconsideration. TSA’s disposition of a petition for reconsideration is a final administrative determination that may be appealed to federal court.
The covered aircraft operator’s AOIP will set forth these specific dates in which the covered aircraft operator must begin collecting and transmitting each of the required data elements. Establishing the implementation schedule within the AOIP framework allows for some flexibility with implementation dates, taking into consideration both TSA security needs and the covered aircraft operators’ technological capabilities.
The first SFPD element that must be implemented is likely to be a passenger’s full name. Because covered aircraft operators and third party agents currently collect the name as part of their business practice, TSA expects that they will have little difficulty collecting and transmitting full name within 120 days of publication of this Final Rule in the Federal Register.
Covered aircraft operators will implement the other SFPD elements such as gender and date of birth in subsequent months in accordance with the AOIP. This approach will allow covered aircraft operators to make their technological changes gradually. However, covered aircraft operators may choose to make all their system changes for the Secure Flight program at the same time provided that the covered aircraft operators is capable of collecting and transmitting the full name within 120 days of publication of the Final Rule in the Federal Register. TSA anticipates that covered aircraft operators will be capable of collecting and transmitting all of the SFPD elements within nine months of Final Rule publication in the Federal Register because many covered aircraft operators have already made changes to comply with CBP’s APIS Pre-Departure data submission requirements.
If implemented by TSA, aircraft operators will be able to enter a passenger’s Known Traveler Number in lieu of a Redress Number, eliminating the need for a separate data field. Covered airlines are required to request these same data elements from non-traveling individuals seeking access to an airport sterile area. The rule does not require air carriers to retroactively request the full name, date of birth, gender, or Redress Number from passengers who have made reservations on covered flights prior to the rule’s compliance date.
In order to address privacy concerns and provide notice about the Secure Flight program in a manner not excessively complex or overly burdensome to airlines, travel agents, and passengers, covered airlines are required to make available a privacy notice prior to collecting information from an individual on a website or self-service kiosk. TSA will also post a privacy notice on its own website to which airlines can link their sites if they choose. This notice informs potential passengers that the airline will transmit passenger information to the Federal Government and use this data to conduct watch list matching.
Provision of full name, date of birth and gender by passengers and non-traveling individuals is mandatory under the final rule, while provision of the other requested information (Redress Number, Known Traveler Number and Passport information) will be voluntary. If an individual chooses not to provide the requested information, however, TSA may have insufficient information to distinguish him or her from a person on a watch list. Accordingly, the individual may experience delays, be subject to additional screening, or be denied transport or authorization to enter a sterile area.
In accordance with their AOIP, all covered airlines will begin collecting and transmitting the SFPD. The SFPD includes the full name; date of birth; gender; and, if available, Redress Number or Known Traveler Number (if implemented) from individuals seeking to make a reservation on a covered flight.
Once the first aircraft operators begin sending passenger and non-traveler information to TSA, TSA will conduct operational testing of its ability to connect with aircraft operators and the TSC, receive passenger and non-traveler information, conduct watch list matching, and transmit gate and boarding pass printing instructions back to the aircraft operators. During the operational testing phase, airlines will continue to make determinations as to Selectee and No Fly status, except in instances where TSA identifies a match to the Terrorist Screening Database (TSDB) that an aircraft operator has not identified. This may occur because TSA will be using different watch list matching technology than the airlines.
Once TSA publishes the Federal Register notice announcing implementation of the Secure Flight program, TSA begins assuming responsibility for the watch list matching function from aircraft operators on a carrier-by-carrier basis. Although TSA will then have primary responsibility for watch list matching, the aircraft operator will temporarily continue to compare passenger information to the watch lists so that there will be a period of overlap with the watch list matching performed by the Federal Government under Secure Flight. The precise timeline of this transition is dependent upon the results of operational testing.
Beginning not more than 72 hours prior to each flight’s departure, airlines will transmit to TSA certain passenger information, as available, for passengers scheduled to board that flight. Airlines will transmit to TSA information from passengers who make reservations within this 72 hour window as soon as the airline processes the reservation. The information packet, called the Secure Flight Passenger Data (SFPD), includes for matching purposes each passenger’s full name, date of birth, and gender; and if provided or available during the reservation process TSA Redress Number and/or Known Traveler Number. If available, the SFPD will further include a passenger’s passport information (passport number, country of issuance, expiration date, gender, and full name). To provide the Secure Flight system with message routing and prioritization information, the SFPD will also contain itinerary information.
Although TSA requires covered aircraft operators to collect and transmit SFPD, TSA is not mandating how covered aircraft operators must store or extract passengers’ SFPD. Covered aircraft operators may choose to extract SFPDs from their reservation system or develop a separate system. Based on interviews with covered airlines, TSA has assumed for the purposes of this analysis that airlines will choose to use their reservation systems to collect and transmit SFPD.
The Secure Flight automated system will compare the submitted passenger information to the government watch lists and return to the airline a boarding pass printing instruction of “cleared,” “selectee,” or “boarding pass inhibited” for each passenger. In certain cases, which TSA will identify to aircraft operators through their AOIPs, changes to a passenger’s itinerary will require the airline to resubmit the revised SFPD to Secure Flight in order to receive an updated boarding pass printing instruction. Further, when the TSC updates the watch lists, the Secure Flight automated system will match all SFPDs indicating passenger travel within the next 72 hours against the updated watch list and will issue updated boarding pass printing instructions for any passengers whose watch list matching result have changed. This live matching process will continue until the scheduled arrival of the last flight in a SFPD.
If the Secure Flight automated system determines an individual is a match to the Selectee list, a TSA matching analyst will review the SFPD to determine if the passenger appears to be the individual on the list. If necessary the analyst will check other classified and unclassified governmental terrorist, law enforcement and intelligence databases, including databases maintained by the Department of Homeland Security, Department of Defense, National Counterterrorism Center, and the Federal Bureau of Investigation, in order to distinguish an individual from a person on a watch list. This careful review process should reduce the number of false positives identified by the automated watch list process. If TSA is unable to determine from the information provided in the full SFPD whether an individual is a match to the Selectee List prior to the individual’s arrival at the airport or online check-in, it will be necessary for the individual to provide additional information at the airport. The individual will be required to check in at the airport with a ticket agent or other airline representative5 and provide an unexpired government-issued identification (federal, state, local, or tribal, or a foreign government-issued passport) that contains both a photo of the individual and the individual’s date of birth. Examples of such documents are an unexpired driver’s license or a passport.
Once the individual has provided the ticket agent with an acceptable form of identification, the agent will communicate to TSA information from the individual’s form of identification and any additional identifying information, such as a physical description, that TSA may require to complete the watch list matching process. TSA matching analysts will complete the watch list matching process, in coordination with the TSC, and will provide the agent with boarding pass printing instructions for that individual in real-time. Individuals who believe they have been wrongly or unfairly subjected to enhanced screening are encouraged to seek redress through the Department of Homeland Security Traveler Redress Inquiry Program (DHS TRIP) described in the rule. Individuals who go through the DHS TRIP will receive a Redress Number that they can provide during future reservations.
If the Secure Flight automated system returns a result of “boarding pass inhibited” for a passenger, a TSA matching analyst reviews the SFPD to determine if the passenger appears to be the individual on the list. If necessary, the analyst checks other classified and unclassified governmental terrorist, law enforcement, and intelligence databases, including databases maintained by the Department of Homeland Security, Department of Defense, National Counterterrorism Center, and Federal Bureau of Investigation, in order to distinguish an individual from a person on a watch list. This careful review should reduce the number of false positives identified by the automated watch list process.
If the TSA matching analyst identifies a possible match between a passenger and an individual identified on the No Fly list, TSA will send the SFPD to TSC and request confirmation of the match. If TSC determines the individual is not a match to the No Fly list, TSA will send an updated instruction to the aircraft operator, indicating that the individual has been “cleared.” If TSC confirms a match to the No Fly list, the “boarding pass inhibited” instruction previously sent to the aircraft operator will continue to govern.
TSC may notify law enforcement officials separately to initiate an operational response, if appropriate, when a match to a known or suspected terrorist on the TSDB is confirmed. TSA also may notify law enforcement personnel responsible for airport security to facilitate a law enforcement response to an individual identified in the Selectee or No Fly Lists. Further inquiry by law enforcement may, for example, help resolve a situation of mistaken identity by confirming or negating the determination made in the matching process that an individual should be denied boarding or entry to a sterile area.
If TSA is unable to determine from the information provided in the full SFPD whether an individual is a match to the TSC’s No Fly List prior to the individual’s arrival at the airport or online check-in, it will be necessary for the individual to provide additional information at the airport. The individual is required to check in at the airport with a ticket agent or other airline representative6 or a self-serve kiosk that is capable of determining that the identification is a valid verifying identity document (VID), authenticating the VID, and reading and transmitting passenger information from the VID. The individual must provide to the ticket agent or airline representative or at the self-serve kiosk an unexpired government-issued identification (federal, state, local, or tribal, or a foreign government-issued passport) that contains both a photo of the individual and the individual’s date of birth. Examples of such documents are an unexpired driver’s license or a passport.
Once the individual has provided the ticket agent with an acceptable form of identification, the agent communicates to TSA information from the individual’s form of identification and any additional identifying information, such as a physical description, that TSA may require to complete the watch list matching process. TSA matching analysts complete the watch list matching process, in coordination with the TSC, and will provide the agent with boarding pass printing instructions for that individual in real-time.
TSA is developing the protocols and standards for placing a bar code on boarding passes and will require covered aircraft operators to place the code on their boarding passes. When TSA updates the Consolidated User Guide with the protocols and standards for the code, covered aircraft operators must implement this requirement in accordance with their AOIP. While the timing of the introduction of the bar code is uncertain, TSA has included an estimate of these costs in the this analysis. Implementation will require covered aircraft operators to print a code on each boarding or gate pass issued to a passenger or non-traveling individual for whom Secure Flight has returned a boarding or gate pass printing instruction. Once the bar code requirement is implemented, the Secure Flight system will automatically generate a unique code for each printing instruction returned to covered aircraft operators. Aircraft operators will be required to print this code separately from any other bar or optical code currently printed on a boarding or gate pass. Personnel at security checkpoints will use this code to verify the authenticity of the boarding pass. Depending upon the final implementation method, security personnel may also use the code to verify that an ID presented at the checkpoint matches the information that was submitted to the Secure Flight system.
Extension of the Secure Flight Program to Additional Aircraft Operators. Through a future rulemaking, TSA plans to propose to extend the Secure Flight program to cover watch list matching for other categories of aircraft operators that currently carry out the watch list matching function for passengers on flights. These include aircraft operators covered by CBP’s APIS regulations that may not be covered by this rule.
Identification Requirements. In order to increase the security benefit of the Secure Flight program, TSA is also considering strengthening the identification requirements at the security screening checkpoint. For example, TSA may consider requiring individuals to present a document similar to a verifying identity document to be able to proceed through the checkpoint. Strengthening the requirement that an individual provide evidence at the security screening checkpoint that he or she is the person to whom the boarding pass or other authorization was issued provides additional assurance that the individual has not used an assumed identity when making a reservation in order to defeat the watch list matching process.
Section 4: Establishing a Baseline: Passenger Air Transportation Today
Domestic Aircraft Operators
This rule affects all aircraft operators conducting flight operations under a full security program per 49 CFR 1544.101(a). In general, these aircraft operators are the major passenger airlines that offer scheduled and public charter flights from commercial airports. Specifically, the covered carriers are those performing scheduled service or public charter passenger operations either with an aircraft having a passenger seating configuration of 61 or more seats or having 60 or fewer seats if the aircraft enplanes from or deplanes into a sterile area. At the time of writing, 66 aircraft operators met the criteria for being a covered domestic carrier under the Secure Flight final rule. According to the Department of Transportation’s Bureau of Transportation Statistics’ (BTS) T-100 Domestic Market data, the covered aircraft operators accounted for 635,606,671 enplanements in fiscal year 2005, 99.7% of total domestic enplanements for that year. Thus, these carriers represent the bulk of domestic air passenger transportation.
The aerospace forecast published annually by the Federal Aviation Administration’s Office of Aviation Policy and Plans projects continued growth of domestic commercial aviation over the next ten years.7 TSA applied the FAA forecast growth rate to the covered carriers’ 2005 enplanements to determine future year enplanements. Table 1.4.1.a presents the forecast for domestic enplanements for the ten years covered by this analysis.
Table 1.4.1.a Covered Carrier Forecasted Enplanements |
|
Program Year |
Millions of Domestic Enplanements |
1 |
677.5 |
2 |
698.3 |
3 |
720.3 |
4 |
742.8 |
5 |
766.6 |
6 |
791.0 |
7 |
816.7 |
8 |
843.2 |
9 |
871.0 |
10 |
900.2 |
Source: FAA forecast (see note 2). TSA substituted covered aircraft operators’ total FY2005 enplanements for FAA’s FY2005 estimate and applied FAA’s forecasted growth rate to this total.
BTS divides domestic air carriers into six classifications: major, national, large regional, medium regional, small, and commuter. Classification is determined initially by the type of operating certificate a carrier holds and then, in the case of large certificated carriers, by revenue. It is important to note that these classifications are based on types of operating certificates and do not represent a scaling of operations. For example, there are considerable similarities in the number of passengers enplaned by regional, commuter, and small certificated carriers. Similarly, operating revenues of commuter airlines are frequently comparable to those of large and medium regionals.8 Nevertheless, while not indicative of the scale of an airline’s operations, these classifications are useful in understanding the nature of an airline’s operations.
Majors, nationals, large and medium regionals all hold a large certificated air carrier certificate under 49 U.S.C. 41102, as amended. These carriers operate aircraft designed to have a maximum passenger seating capacity of more than 60 seats or a maximum payload capacity of more than 18,000 pounds or conduct operations where one or both terminals of a flight stage are outside the 50 states of the United States, the District of Columbia, the Commonwealth of Puerto Rico and the U.S. Virgin Islands.9 Large certificated carriers are required to submit certain operating information to the DOT, including operating revenues and other financial data. BTS uses the operating revenue ranges in Table 1.4.1.b below to divide large certificated carriers into the four carrier groups. The classifications in this analysis were current as of June 15, 2006.
Table 1.4.1.b Large Carrier Revenue Classifications |
|
Carrier Group |
Annual Operating Revenue |
Major |
More than $1,000,000,000 |
National |
$100,000,001 - $1,000,000,000 |
Large Regional |
$20,000,001 - $100,000,000 |
Medium Regional |
Less than $20,000,000 |
Source: BTS10
Small certificated carriers hold a certificate issued under section 401 of the Federal Aviation Act of 1958, as amended, and operate aircraft designed to have a maximum seating capacity of 60 seats or fewer or a maximum payload of 18,000 pounds or less. Commuter carriers are defined as carrying passengers for hire or compensation using small aircraft (30 seats or smaller) under Federal Aviation Regulations (FAR) Part 135 and performing at least 5 scheduled roundtrips per week.11
Table 1.4.1.c shows the number of aircraft operators subject to the requirements of the Secure Flight interim final rule for each BTS grouping:
Table 1.4.1.c Count of Secure Flight Domestic Aircraft Operators by BTS Class |
|
Carrier Group |
Count |
Major |
17 |
National |
23 |
Large Regional |
7 |
Medium Regional |
2 |
Small Certificated |
3 |
Commuter |
14 |
Total |
66 |
These BTS classifications, while useful to describe the relative scope of airline operations, do not provide a useful classification system for describing and distributing the impact Secure Flight will have on the industry. Instead, to represent airline reprogramming costs, TSA had to develop its own classification system in which it divided airlines into “marketing” and “affiliate” carriers and then grouped them based on the nature of their reservation systems. The following paragraphs explain the reasoning behind TSA’s classification method.
In order to communicate with the airlines, Secure Flight needs to interact with the airline reservation systems (ARS) or separate systems established by the airlines specifically for interacting with Secure Flight. TSA has assumed for the purpose of this analysis that airlines will modify their existing reservation systems to create SFPDs, manage transmissions to TSA, and process the boarding and gate pass printing instructions returned by TSA.12 While some airlines maintain their own reservation systems, others choose to subscribe to a hosting system managing multiple ARSs or subscribe to a global distribution system (GDS).13 Some public charter airlines do not maintain a reservation system at all.
Further complexities arise from the fact that in order to increase the number of destinations they can market, most major airlines purchase subsidiary airlines or offer contracts to independent airlines to transport their passengers. In such cases, the major airline is referred to as the “marketing” carrier. The benefit of these arrangements to the “affiliated” carriers is that the marketing carrier is responsible for the reservations process and ticket counters.
In light of this intricate sharing of reservation systems, TSA conducted interviews with the industry to determine the best means of connecting Secure Flight to the covered aircraft operators. Based on these discussions, TSA determined that establishing connectivity with airlines’ reservation and departure control systems, which are frequently hosted and maintained by GDSs and host ARSs, would enable Secure Flight to receive 98% of the enplanements of all covered aircraft operators.
The remaining carriers not utilizing these systems comprise a diverse group. Some of them have independently maintained reservation systems that are highly developed while others, as noted above, do not have a reservation system at all. TSA technical experts considered the number of enplanements and technological capabilities of each of these remaining covered aircraft operators and determined three operators had sufficiently automated systems to make a direct connection to the Secure Flight system cost-effective. TSA assumed the remaining 16 carriers—either not having reservation systems or having systems that would be too costly to modify to support a direct connection—will transmit passenger information to Secure Flight through a secure Web interface DHS is in the process of developing. Carriers may choose, however, which of the transmission interfaces they prefer to implement.
TSA conducted information-gathering interviews with a small number of airlines and ARS service providers. The eight airlines with which TSA spoke came from the diverse groups that make up the domestic passenger aviation industry, including legacy “hub and spoke” carriers, large and small “low cost” carriers that operate in a more point-to-point manner, smaller carriers that serve regional or niche markets, and carriers that provide charter services rather than scheduled passenger transportation. TSA also spoke with two providers of airline reservation system services. One of these is an ARS provider that has provided these services to legacy and other airlines throughout the world for many years, and the other is a more recently established company providing web-based reservation services to airlines that are predominantly “low cost” operators from many parts of the world.
Based on its conversations with host ARSs and airlines regarding the likely cost implications of Secure Flight and input from internal subject matter experts, TSA divided covered airlines into four cost groups, as shown in Table 1.4.1.d. These groups are based on 1) the anticipated difficulty of reprogramming the GDS or host ARS used by an airline to accept additional data elements and communicate with Secure Flight and 2) the BTS class of non-legacy airlines. This method of grouping carriers takes into account the interdependence that exists between airlines and their ARS service providers. Much of the reprogramming work to enable an airline to communicate with Secure Flight will be done by its GDS or host ARS. TSA assumed the costs associated with this work will then be passed on to the subscribing airline. At the same time, airlines also have to make modifications to their own computer systems. In both cases, the older the system being modified, the higher the costs. Similarly, the newer the system or, presumably, smaller its scope (as would be true of regional, commuter, and small carriers as opposed to major or national carriers), the lower the costs.
Table 1.4.1.d Airline vs. GDS/host ARS Reprogramming Effort |
||||
|
|
GDS/host ARS Reprogramming |
||
|
|
Most Effort (Older GDSs/ host ARSs) |
Medium Effort (Newer GDSs/ host ARSs) |
Least Effort (Independent ARSs) |
Airline Reprogramming |
Most Effort (Legacy Airlines) |
Group 1 (10 carriers) |
N/A |
N/A |
Medium Effort (Majors, Nationals) |
Group 2 (6 carriers) |
Group 2 (2 carriers) |
Group 3 (3 carriers) |
|
Least Effort (Regionals, Commuters, Small) |
Group 3 (6 carriers) |
N/A |
N/A |
|
Implementation Group 1 represents all legacy marketing carriers and their affiliates utilizing an older GDS or host ARS. Legacy airlines, those flying prior to the Airline Deregulation Act of 1978 (P.L. 95-504), are all major airlines and have the oldest computer systems. Accordingly, TSA assumed this group will incur the highest compliance costs. Implementation Group 2 includes marketing carriers utilizing a newer GDS or host ARS, as well as national carriers subscribing to an older GDS. Implementation Group 3 represents the three carriers determined capable of receiving a direct connection to Secure Flight, as well as regional, commuter, and small airlines subscribing to an older GDS or host ARS. Group 4 (not shown) contains the remaining 16 carriers that TSA assumes will utilize the Web interface.
Column 2 of Table 1.4.1.e presents the total distribution of carriers, both marketing and affiliated, within each of these four groups according to their BTS classification. The third column provides the number of marketing airlines that TSA assumes will bear the up-front cost burden to connect to Secure Flight. This column shows that of the 66 total carriers, 43 will initially incur costs to connect to the Secure Flight system due to affiliated carriers utilizing the reservation systems of marketing carriers. TSA anticipated these costs will likely be passed on from the marketing carriers to their affiliates, but TSA did not have sufficient information to determine how these costs will be distributed. The fourth column presents the proportion of covered enplanements represented by each group.
Table 1.4.1.e Major Secure Flight Implementation Groupings |
||||
|
Group |
Distribution of Carriers by BTS Classification (66 Carriers) |
Number of Marketing Carriers |
Proportion of Covered Enplanements |
Direct Connection to Secure Flight |
1 Legacy marketing carriers and their affiliates using an older GDS/ host ARS |
Majors: 15 Nationals: 9 Large Regionals: 1 Med. Regionals: 0 Small: 1 Commuter: 6 |
10 |
89.10% |
2 Non-legacy major or national carriers and their affiliates using a GDS/ host ARS |
Majors: 2 Nationals: 6 Large Regionals: 0 Med. Regionals: 0 Small: 1 Commuter: 0 |
8 |
9.20% |
|
3 Remaining non-legacy carriers using a GDS/ host ARS; Majors and nationals with own ARS |
Majors: 0 Nationals: 3 Large Regionals: 1 Med. Regionals: 1 Small: 1 Commuter: 3 |
9 |
1.10% |
|
Secure Flight Web Interface |
4 Non-legacy airlines with manual reservation systems |
Majors: 0 Nationals: 5 Large Regionals: 5 Med. Regionals: 1 Small: 0 Commuter: 5 |
16 |
0.60% |
The global scope of many of these domestic airlines presented additional challenges to estimating the costs these airlines incur to implement the Secure Flight system. Concurrent with the publication of the Secure Flight NPRM, U.S. Customs and Border Protection (CBP) published its Advance Passenger Information System (APIS) pre-departure final rule. The APIS pre-departure final rule modified CBP’s requirements for commercial airlines carrying passengers into and out of the United States, establishing data transmission and watch list matching procedures similar to those of Secure Flight.
While TSA will take over the watch list matching function from CBP for certain carriers through this final rule, the scope of Secure Flight will not cover all carriers subject to CBP’s APIS regulations. Even so, those carriers that will be covered by Secure Flight carry the bulk of international passenger traffic.14 Through this final rule, Secure Flight only covers those international carriers that are generally the foreign equivalent of the U.S. carriers also covered by this rule. Secure Flight will cover commercial foreign airlines flying to or from the U.S. that currently operate under a security program agreement with TSA as set forth in TSA’s existing regulations under 49 CFR 1546.101(a) and (b). TSA chose to implement Secure Flight with this subset of carriers because, as previously indicated, they currently transport the bulk of commercial passenger traffic to, from, and within the U.S. Under the second phase, Secure Flight will phase in requiring operators to submit SFPD for covered flights that overfly the continental US, not including Hawaii and Alaska. Operators unsure if the flight is covered can ask TSA for a determination.
CBP’s APIS final rule gives international air carriers the option to continue transmitting passenger data to CBP in batches using their existing infrastructure; the rule also affords them the option of utilizing a system known as APIS Quick Query (AQQ). This system, maintained and operated by CBP, has interactive messaging capabilities similar to Secure Flight, allowing international air carriers to send passenger information and receive watch list results in real time. CBP will continue to use this system to perform passenger watch list matching for carriers covered by both rules until this responsibility is transferred to TSA during the second phase of Secure Flight implementation.15
Given this overlap in covered populations, TSA sought to identify which domestic carriers will be subject to both APIS and Secure Flight requirements and which will only be subject to Secure Flight. Air carriers with international traffic will likely make their business decisions based on the requirements in both CBP’s and TSA’s final rules, weighing their individual business needs against the various reprogramming options. In this analysis, TSA assumed carriers covered by both rules will seek to minimize their IT investments.
Given that the APIS final rule forms the baseline for the international portion of Secure Flight, TSA adopted as the endpoints of its airline reprogramming estimate the assumptions underlying the high and low scenarios in CBP’s APIS pre-departure final rule regulatory impact assessment. TSA sought to identify the range of investment options available to carriers covered by both rules without double-counting airline reprogramming costs CBP has already reported. In the high scenario, TSA assumed all large foreign and domestic carriers wait to reprogram their systems until Secure Flight becomes effective and small carriers will not need to make any reprogramming changes to comply with the APIS rules. In its low scenario, TSA assumed all large foreign and domestic carriers implement AQQ without waiting for Secure Flight. Corresponding to CBP’s assumption, TSA assumed small foreign carriers will not need to make any reprogramming changes to comply with the rule.
In its final regulatory impact assessment, CBP identifies 11 large domestic air carriers as subject to the APIS requirements, where “large” is identified as a carrier with more than 1,500 employees. Although CBP’s evaluation does not explicitly identify groups of marketing and affiliate carriers when estimating reprogramming costs, the use of this methodology is implied by the fact that 35 domestic carriers subject to Secure Flight are both large carriers and have international enplanements subject to APIS regulations. Of these 35 domestic carriers, 1 falls into Group 4 and is not expected to incur any reprogramming costs. Of the remaining 34, 17 are Secure Flight points of implementation—assumed to incur reprogramming costs—and 17 are affiliate carriers. Table 1.4.1.f below shows the distribution of these carriers by their respective Secure Flight implementation groups.
Table 1.4.1.f Secure Flight Large* Domestic Carriers Reporting to APIS |
|||||
Carrier |
Implementation Group |
|
|||
Characteristics |
1 |
2 |
3 |
Total |
|
Marketing Carriers |
9 |
6 |
2 |
17 |
|
(Affiliate Carriers) |
(16) |
(1) |
(0) |
(17) |
|
|
|
|
|
|
|
Marketing Carriers Connected to CBP |
9 |
2 |
0 |
11 |
|
* “Large” here corresponds to the definition used by the Small Business Administration, namely, carriers which have more than 1,500 employees or which are subsidiaries of such companies. |
|||||
As can be seen from the table, 9 Group 1 marketing carriers and 2 of the marketing carriers from Group 2 already have connections established to CBP. Carriers utilizing a direct connection to CBP are charged a flat monthly fee regardless of the number of transmissions they send. Carriers transmitting information through another source pay a per-kilobyte fee for each transmission, making them sensitive to the number of transmissions. Establishing a direct connection requires installation of routers, circuits and other hardware in which carriers have been reluctant to invest pending TSA’s publication of the final requirements for Secure Flight, particularly since the APIS final rule permits them to continue using batch processing. Since the existing messaging structure for the 11 implementation carriers identified above makes them less sensitive to increases in their message traffic, it is reasonable to assume they may have implemented AQQ prior to issuance of a final rule implementing Secure Flight. TSA’s estimate of costs associated with these decisions is presented below in Section 1.6.2.
Foreign Aircraft Operators
This rule affects foreign air carriers that are required to have a security program under 49 CFR 1546.101(a) or (b). These aircraft operators generally are the passenger airlines that offer scheduled and public charter flights from commercial airports. The rule covers all flights conducted by a covered foreign air carrier arriving in, departing from, or overflying the United States.16 TSA will conduct watch list matching for overflights in order to protect the United States against terrorist activity that could occur in its airspace. At the time of writing, there were 146 foreign air carriers that are be covered by this rule.
In calculating the number of international reservations, TSA based its estimate on the passenger estimates in the regulatory impact assessment accompanying CBP’s 2007 APIS final rule, assuming one reservation per passenger. CBP divided passengers into four categories: passengers on large U.S. carriers, passengers on large foreign carriers, passengers on small U.S. carriers, and passengers on small foreign carriers. Secure Flight will cover all of these passengers carried by large U.S. and foreign carriers. However, not all of the international passengers on small U.S. and foreign carriers will be covered by the rule. In order to determine the number of international passengers on small carriers, TSA first determined the ratio of international enplanements on large domestic carriers to small domestic carriers. Foreign carriers were handled in the same manner. Examining international enplanements for FY05 yields small to large carrier enplanement ratios of 1.9 : 52.8 for domestic carriers and 1.5 : 43.8 for foreign carriers. Each category of international enplanements by carrier type is presented as a percentage of total international enplanements in Table 1.4.1.g.
Table 1.4.1.g International Enplanement Shares |
|||
|
Not Small |
Small |
Sum |
US Flag |
52.8% |
1.9% |
54.7% |
Foreign Flag |
43.8%** |
1.5% |
45.3% |
Sum |
96.6% |
3.4% |
100.0% |
** Includes carriers of unknown size Source: BTS. |
|||
Those ratios were then applied to known anchors. The two known anchors are the international passengers by large carriers, both foreign and domestic. These are “known” because they are all covered by Secure Flight. TSA did not use the total international passengers because an unknown number are not covered. As an example, in 2006 there were an estimated 1,273,000 international passengers on small U.S. flag carriers. This is derived by multiplying the 2006 Large U.S. international passengers (35,373,000) by the proportion of U.S. small to large carrier enplanements (1.9/52.8) which yields 1,273,000 international passengers on small U.S. carriers in 2006. The same method is used to calculate the projected international passengers on small foreign carriers.
Neither DHS nor DOT publishes statistics on passenger data for flights that overfly the United States. The existing APIS regulations require foreign carriers to submit crew manifests to CBP; however, CBP does not track this data or collect information about passengers. In order to estimate the number of affected passengers on covered international carriers overflying the U.S., TSA consulted the FAA’s Enhanced Traffic Management System (ETMS), which records flight information of aircraft entering U.S. airspace. TSA extracted fiscal year 2005 overflight data by carrier and then by ranges of aircraft seats (e.g., flights by aircraft with 0 to 60 seats, flights by aircraft with 61 to 100 seats, etc.). To arrive at an estimate of passenger totals, TSA analyzed the types of aircraft flying within each category and multiplied the number of flights by a weighted average number of seats and an applicable load factor. TSA then compared the derived passenger totals to a list of international operators that are covered by Secure Flight in order to estimate the number of passengers overflying the U.S. who are affected by this rule. This method enabled TSA to estimate passengers for 96.3% of covered overflights. ETMS data for the remaining flights did not contain enough information for TSA to project passenger totals; thus, the totals presented here may slightly understate the actual number of covered passengers overflying the U.S. TSA adopted CBP’s assumption that these passenger totals will grow by 5% annually.
The rule also covers U.S. carriers flying between two foreign points. Since these flights operate exclusively outside the United States, they are distinct from international flights operated by large U.S. carriers in the passenger totals reported by CBP. DOT’s Bureau of Transportation Statistics reports that U.S. flag carriers transported 3.6 million passengers on such flights in 2006. TSA applied the estimated 5% annual growth rate in international passenger traffic to project this traffic through 2017.
Through these combined methods, Table 1.4.1.h projects annual totals of covered international passengers.
Table 1.4.1.h Projected Secure Flight Covered International Passengers (Millions) |
||||||||
Program Year |
Large U.S. |
Large Foreign |
Small U.S. |
Small Foreign |
Total U.S. Entries/ Exits |
Covered Foreign Carriers Overflying |
U.S. Carriers, Foreign Point-to-Point |
Total Covered Passengers |
1 |
39.0 |
44.0 |
1.4 |
1.5 |
85.9 |
34.2 |
4.0 |
124.1 |
2 |
40.9 |
46.2 |
1.5 |
1.6 |
90.2 |
35.9 |
4.2 |
130.3 |
3 |
43.0 |
48.5 |
1.5 |
1.7 |
94.7 |
37.7 |
4.4 |
136.8 |
4 |
45.1 |
50.9 |
1.6 |
1.7 |
99.4 |
39.6 |
4.6 |
143.7 |
5 |
47.4 |
53.5 |
1.7 |
1.8 |
104.4 |
41.6 |
4.8 |
150.8 |
6 |
49.8 |
56.1 |
1.8 |
1.9 |
109.6 |
43.7 |
5.0 |
158.3 |
7 |
52.3 |
58.9 |
1.9 |
2.0 |
115.1 |
45.9 |
5.3 |
166.3 |
8 |
54.9 |
61.9 |
2.0 |
2.1 |
120.8 |
48.2 |
5.6 |
174.6 |
9 |
57.6 |
65.0 |
2.1 |
2.2 |
126.9 |
50.6 |
5.9 |
183.4 |
10 |
60.5 |
68.2 |
2.2 |
2.3 |
133.2 |
53.1 |
6.2 |
192.5 |
Airport Operators
The rule establishes a process by which airports having a TSA-approved program to authorize non-travelers to enter the airport sterile area will transmit non-traveler information to TSA for watch list matching by Secure Flight. Since covered carriers are responsible for authorizing non-traveling individuals who wish to accompany passengers, this clause for airport operators is intended largely for commercial purposes. For example, an airport with a large shopping center beyond the checkpoints may wish to open those stores to the public. Consequently, this rule does not require airport operators to change existing operations. Further, airport operators are not part of Secure Flight operational testing and their participation in a program to authorize non-traveling individuals to enter a sterile area is voluntary.
At present, most airports are not permitted to grant individuals authorization to enter the sterile area; rather, non-travelers must acquire a gate pass from airlines. TSA recently began a pilot program, however, at three domestic airports where hotels are located on the airport. Guests at those hotels are given the option to enter the airport sterile area for shopping and dining purposes. This option is only available to guests who do not have an airline itinerary for the same day; guests with flight itineraries must use their airline boarding pass to enter the sterile area. Currently, guests wishing to enter the sterile area under the pilot program must provide their personal information to the hotel. Hotel personnel then give this information to a law enforcement officer who typically conducts a manual comparison of the information against the watch lists, checks the guests’ identifications and, if approved, issues them a pass to enter the sterile area. The guests must then pass through the TSA screening checkpoint.
Under the rule, the function of comparing guests’ names against the watch list is transferred from a manual process to an automated process, likely using the Secure Flight web interface. TSA is unable to say at this time, however, how this change will affect the processes in place at the time of Secure Flight’s implementation. Given the small number of airports involved and the eligibility restrictions, guest participation in the pilot has been limited. TSA will continue to evaluate different operational processes as the pilot progresses in order to determine which are most efficient without jeopardizing security.
Travel Agencies, GDSs, and Host ARSs
As previously discussed, the high degree of interconnectedness of airline reservation systems requires GDSs and host ARSs to incur costs as a consequence of this regulation. While they are not a regulated party, TSA sought to represent the impact of the rule to these groups.
Travel agents are also impacted by this rule. Travel agents rely on GDSs to make reservations on behalf of their clients. Changes to GDS systems can subsequently require a period of adjustment on the part of travel agents, resulting in a temporary slowing of the reservation process. More directly, the requirement within this rule that aircraft operators must request each passenger’s full name, date of birth, gender, and submit if available the Redress Number will result in a long-term impact to travel agents because it lengthens the time required to complete each reservation.
For the purposes of this analysis, TSA considered two types of travel agencies: online and traditional. Online travel agencies, like Expedia and Travelocity, are an intermediary to a GDS interface. TSA estimated in 2004 that GDSs processed approximately 70% of airline bookings from travel agencies and Internet reservation sites, with five GDSs handling a majority of these transactions. Based on guidance from industry experts, GDSs will bill airlines for changes they will have to make to comply with Secure Flight. GDSs will then push the modifications to their online travel agency subscribers. Thus, many of the reprogramming changes that will be required for online travel agencies are assumed to be covered in the airline reprogramming costs. Some online travel agencies, particularly the very large ones, may incur additional costs to modify their user interfaces and other corporate systems to incorporate the changes provided by the GDS. Accordingly, TSA has estimated a nominal cost for this effort in Section 1.6.4.
Traditional travel agencies comprise a diverse industry. According to survey information on the American Society of Travel Agents’ (ASTA) website17, most traditional travel agencies are small, with an average staff size of four to five full-time employees. With the ease of Internet booking, travel agents have experienced a decline in the number of domestic air traffic reservations they place on behalf of customers in recent years. Survey data collected by ASTA shows that airline tickets as a proportion of travel agency business has fallen from 58% in 1996 to 29.3% in 2005. As a strategy to cut costs, airlines began reducing commissions to travel agents in 1995 and eliminated commissions for domestic itineraries altogether in 2002. Airlines have also aggressively promoted the use of online reservation methods by offering special low fares that they do not always pass on to travel agents.18 Nevertheless, data in Travel Weekly’s 2004 annual survey shows that airlines anticipated 36% of reservations would be made by traditional travel agents that year.19 TSA was unable to update these findings for more recent years, but Travel Weekly’s 2005 survey notes, “when suppliers were asked how their mix of intermediary and direct sales for 2005 are expected to differ from 2004, most said they expect no significant changes this year.”20
1.4.2 The Airline Reservation Process
Domestic Reservations
Airline reservations are placed primarily through three sources: online reservation sites, airline call centers, and traditional travel agencies. Online reservation methods include both airline websites (which are examples of ARSs) and online travel agencies (GDSs). Travel Weekly’s 2004 annual survey indicates that airlines anticipated 49% of their bookings that year would come from online sources. Meanwhile, only 15% of bookings were expected to be placed through airline call centers, a result of continuing airline efforts to reduce their costs per reservation. The remaining 36% of bookings were expected to come from traditional travel agents.
Due to the lack of reliable raw data on the distribution of passenger reservations, TSA adopted these booking proportions for the purposes of calculating opportunity costs in this analysis. Although TSA recognized there is considerable uncertainty surrounding the future distribution of airline reservations, TSA did not have sufficient data to estimate growth rates and chose to hold these proportions steady over the ten year projected costs.
Since this rule impacts the time required to complete airline reservations, TSA had to estimate the number of actual reservations processed annually for the covered airlines. The aviation industry keeps no record of the actual number of passengers transported, so TSA chose to use a combination of enplanement data and analysis of BTS’ Airline Origin and Destination Survey to estimate a number of annual airline reservations.
Since total enplanements is a count of the number of passengers who board passenger aircraft in a given year, this figure likely overestimates the number of reservations made annually. For example, a passenger flying from Des Moines to Washington, D.C., with a connecting flight in St. Louis, is counted as two passengers rather than one. Further adjustment must be made for the fact that a roundtrip reservation will account for at least two enplanements.
To estimate the number of roundtrip flights booked by passengers, TSA conducted an analysis of BTS’ Airline Origin and Destination Survey DB1B Ticket Data.21 Table 1.4.2.a presents data for 2000 through 2004, which reveals that the proportion of roundtrip itineraries over the five years remained very close to the average of 79%.
Table 1.4.2.a Percent of Roundtrip Itineraries |
|
Year |
Roundtrip |
2000 |
77.4% |
2001 |
79.6% |
2002 |
80.4% |
2003 |
79.6% |
2004 |
78.5% |
Average |
79.1% |
Further analysis of the BTS Origin and Destination Survey provided insights into the number of itineraries with connecting flights at a hub airport. Calculations based on all domestic enplanements (including international connections from outside the U.S. headed for other U.S. destinations) for the year ending in the third quarter of 2005 indicate that approximately 30% of itineraries involve connecting enplanements.
Combining the data on roundtrip itineraries and connecting flights enabled TSA to make a rough conversion from annual enplanements to the number of reservations those enplanements potentially represent. One offsetting consideration, however, is that a significant percentage of reservations are cancelled and rebooked or otherwise modified such that assuming each reservation results in a completed trip could result in underestimating the number of reservations. According to a December 2005 USA Today article, the percentage of cancelled itineraries across the airline industry is approximately 12%.22
Since some reservations represent more enplanements than others, TSA used the available data to come up with four broad categories of reservations. The data on roundtrip flights first allowed TSA to distinguish between roundtrip (79%) and one-way (21%) reservations. The data on connecting flights (30%) then permitted TSA to subdivide these reservations into the four categories: direct roundtrip, multi-segment roundtrip, direct one-way, and multi-segment one-way reservations. To convert enplanements into reservations, TSA assumed that each direct roundtrip and connecting one-way reservation represent two enplanements. TSA further assumed that multi-segment roundtrip reservations represent four enplanements and that direct one-way reservations represent a single enplanement. Having thus converted enplanements into a projected number of reservations, TSA inflated the yearly totals by 12% to compensate for cancelled and rebooked reservations.
Table 1.4.2.b presents projected reservations by reservation method based on these calculations over the next ten years. Reservations for Group 4 are not included in the table below because this group does not process reservations in the same manner as the rest of the industry. These differences are discussed in greater detail below.
Table 1.4.2.b Covered Carrier Forecasted Domestic Reservations (Millions) |
||||
Program Year |
Airline Call Centers (15%) |
Traditional Travel Agency (36%) |
Online Reservation Method (49%) |
Total Domestic Reservations |
1 |
58.1 |
139.5 |
189.8 |
387.4 |
2 |
59.9 |
143.8 |
195.7 |
399.4 |
3 |
61.8 |
148.3 |
201.9 |
412.0 |
4 |
63.7 |
153 |
208.2 |
424.9 |
5 |
65.8 |
157.9 |
214.9 |
438.6 |
6 |
67.9 |
162.9 |
221.7 |
452.4 |
7 |
70.1 |
168.2 |
228.9 |
467.1 |
8 |
72.3 |
173.6 |
236.3 |
482.3 |
9 |
74.7 |
179.4 |
244.2 |
498.3 |
10 |
77.3 |
185.4 |
252.4 |
515.0 |
* Totals may not sum due to rounding. |
||||
While there is no standardized format for reservations accepted throughout the air travel industry, very few travel agents or airlines currently request a passenger’s full name, date of birth, and gender, Redress Number, Known Traveler Number or passport information as required under this regulation. Analysis of the June 2004 PNRs submitted by the airlines revealed that many PNRs did contain both a first and last name. Middle names or initials were often included in the first name field, however, and date of birth was rarely present at all.
Booking systems that do not currently have unique fields for each of these data elements need to be reprogrammed in order to accept them. This work will be done largely by the GDSs and host ARSs that maintain reservation systems for airlines subscribing to such services. The GDSs and host ARSs will then bill these charges back to the airlines. Additional reprogramming may be required specifically of airlines and travel agencies to accept this information in their customer databases. These costs are discussed in section 1.6.2.
ASTA representatives informed TSA that nearly all travel agencies maintain databases containing customer profiles. When asked about likely travel agent responses to the addition of one or two passenger data elements to the air reservation process, ASTA indicated most travel agencies find it more cost-effective to collect this information when their clients book their next trip. ASTA also indicated, however, that some corporate travel agencies may attempt to contact business travelers, asking them to update their profiles prior to their next booking. ASTA pointed out that such an outreach will likely be cost-effective only for a small number of firms. As TSA has quantified both the anticipated cost for travel agencies to request the additional information and for their clients to provide it, TSA believes the remaining unquantified cost will be small.
Given the absence of data on profiles retained by travel agencies, customer loyalty to a particular form of booking air travel, and an estimate of repeat travelers, TSA assumed for the purposes of this evaluation that all passengers will be asked to provide their full names, dates of birth, genders, and Redress Numbers when making air travel reservations. TSA developed three scenarios to capture the range of potential impacts to airlines and travel agents of the data collection requirements in the rule.23 TSA assumed that these burdens to be more significant for reservations made via telephone than those booked online because information must be relayed between the reservation agent and passenger. Consequently, TSA assumed for all online reservations an additional 10 seconds per reservation is required for passengers to provide the requested information. The scenarios, described below, thus address the uncertainty surrounding reservations made over the telephone.
Requesting and collecting additional data elements during telephone reservations lengthens the time to complete those reservations. Airlines and travel agents informed TSA that they closely monitor their telephone reservation process, assigning an undisclosed cost to each second a reservation extends beyond an optimum time. According to industry information from ASTA, many travel agents facilitate this process by utilizing “scripts,” software code that prompts the agent word-for-word through the reservation process based on the information they enter into the booking system. Any change to the reservation process requires reprogramming of these scripts. Both airlines and travel agents use these time targets to make a variety of operational decisions. Stakeholder representatives said that extending the time required to complete an average reservation will be costly. Neither group provided estimates to TSA, however, that would allow for actual quantification of this impact. Passengers listening to the request and deciding whether to provide the additional information also incur opportunity costs in the form of lost time.
To account for these costs, TSA estimated the additional time needed to request and provide the additional information to be an average of 25 seconds per reservation. This forms TSA’s primary estimate. For its low scenario, TSA assumed the information collection add only 20 seconds to each telephone reservation. TSA assumed in the high scenario that the information collection adds 30 seconds to each telephone reservation.
Since airline reservation agents will collect personal information from passengers and share that information with the Federal Government, the rule requires airlines to make available to passengers before collecting their information a privacy notice on a website or self-service kiosk. TSA also will post a copy of the notice on its own website. Airlines and internet reservation sites will then duplicate this notice on their own privacy pages or provide a link to the notice on TSA’s website. Many online booking systems have privacy notices already built into the reservations process for their own purposes; thus, TSA determined that adding the TSA privacy notice to these existing notices have little impact on either those systems or their customers. As a result, TSA assumed provision of a privacy notice adds no appreciable time to reservations.
The discussion in this section applies to carriers in Implementation Groups 1-3 but cannot be extended to carriers in Group 4 because not all carriers in this group accept reservations in the same manner as those discussed above. Some are scheduled service carriers that accept reservations from the public through their company websites or call center, while others are public charter operations and only accept reservations through a tour operator. A few operate as a combination, providing limited scheduled service and accepting charter reservations. In the case of a charter reservation, the carrier does not receive individual passenger reservations. Instead, the tour operator or group chartering the aircraft submits information for a full planeload of passengers in a passenger manifest. Consequently, charter-only operators do not have their own reservation systems but instead receive these manifests two to three days prior to a flight.24 Per the Final Rule, covered aircraft operators performing private charter operations may submit voluntarily the SFPD for their passengers to TSA.
Due to these differences, TSA has treated reservations for these Group 4 carriers separately from those of Carriers in Groups 1 - 3. Costs for passengers traveling on Group 4 carriers to provide the additional date requested in the final rule are presented in Section 1.6.6. Based on the way these carriers collect reservations and observations of similar carriers currently reporting to CBP’s web-based application, eAPIS, TSA believes these carriers will be able to shift the data collection burden directly to the passenger. Accordingly, TSA has not estimated data collection costs for these Group 4 airlines. Table 1.4.2.c shows forecasted reservations for Group 4 carriers over the next ten years using the same calculation techniques as above.
Table 1.4.2.c Forecasted Group 4 Reservations |
|
Program Year |
Millions of Reservations |
1 |
2.4 |
2 |
2.4 |
3 |
2.4 |
4 |
2.6 |
5 |
2.6 |
6 |
2.8 |
7 |
2.8 |
8 |
3.0 |
9 |
3.0 |
10 |
3.1 |
International Reservations
TSA did not have information on the distribution of international reservations between different reservation methods. As a proxy, TSA assumed international reservations for large domestic and large foreign carriers will be distributed among airline call centers, brick and mortar travel agencies, and online reservation sites in the same proportions as reported above for domestic reservations. TSA assumed, however, that the reservation processes for small foreign carriers exhibit characteristics more comparable to domestic carriers in Group 4 than to large carriers. Thus, consistent with its determination regarding Group 4 carriers, TSA has based its estimates of data collection costs only on the international passenger totals for large domestic and large foreign carriers, including overflights and U.S. carriers flying point-to-point internationally. These totals are presented in Table 1.4.1.h. TSA has summarized these international passengers by their assumed respective reservation methods in Table 1.4.2.d below. Opportunity costs for passengers on small foreign carriers are presented in Section 1.6.6.
Table 1.4.2.d Covered Carrier Forecasted International Reservations (Millions) |
||||
Program Year |
Airline Call Centers (15%) |
Traditional Travel Agency (36%) |
Online Reservation Method (49%) |
Total International Reservations |
1 |
18.2 |
43.6 |
59.4 |
121.2 |
2 |
19.1 |
45.8 |
62.4 |
127.3 |
3 |
20.0 |
48.1 |
65.5 |
133.6 |
4 |
21.0 |
50.5 |
68.7 |
140.2 |
5 |
22.1 |
53.0 |
72.2 |
147.3 |
6 |
23.2 |
55.7 |
75.8 |
154.7 |
7 |
24.4 |
58.5 |
79.6 |
162.5 |
8 |
25.6 |
61.4 |
83.6 |
170.6 |
9 |
26.9 |
64.5 |
87.7 |
179.1 |
10 |
28.2 |
67.7 |
92.1 |
188.0 |
* Totals may not sum due to rounding. |
||||
1.4.3 Watch List Matching Today
Domestic
At present, covered aircraft operators employ a variety of methods to conduct watch list matching. Most major carriers have a corporate security department that keeps track of when TSA posts updated watch lists. These lists are then incorporated into the carriers’ automated reservation systems. Though there are various procedures in place across airlines, representatives of two carriers stated the process of incorporating the updated watch list into their reservation systems requires two to three hours to complete.
The reservation systems perform name-based comparisons of passenger names to the names in the watch lists. Some major airlines have recently invested in technology that uses sophisticated algorithms to compare passenger names to TSA’s watch lists. Others continue to perform more basic automated comparisons, while some, predominately smaller, airlines do not use an automated process. The boarding pass of a passenger whose name matches a name on the list is “inhibited” until it can be determined the passenger is not a threat to aviation security. In the case of some major carriers, the passenger record is referred to a special watch list adjudication staff maintained by the carrier 24 hours a day. This staff attempts to verify the individual’s identity and rule out false positives before the passenger checks in at the ticket counter.
If this staff cannot distinguish the passenger from the name on the watch list, or if the carrier does not have such a staff, additional information is collected from the passenger at the ticket counter. Generally, the carrier’s Ground Security Coordinator or TSA is consulted to determine the appropriate course of action based on the available information. In some cases, an interview with a law enforcement officer is required before a passenger can be cleared to enter the airport sterile area.
Since each carrier determines its own procedures, there are many variations in current processes based on carrier size and the automation of their systems. Some of the larger carriers maintain 24-hour operations to manage the watch list matching process. Even among these large carriers, however, there are some that require all of their watch list matches to be adjudicated at the ticket counter rather than dedicate staff to attempting to clear these passengers prior to check-in. In similar cost-saving fashion, mid-size and smaller carriers may also use resources for the watch list process that also perform other tasks. This yields great diversity in the current application, continuity, and quality of watch list checks.
Air carriers today do not keep records on the number of false positives created by their watch list matching processes. They are only required to report true positive matches, i.e., when the passenger requesting transportation is actually the person identified on the No Fly list. The airlines are responsible for maintaining these records for only seven days.
After much inquiry, TSA was able to acquire only anecdotal estimates from a few airlines on the number of watch list matches processed daily. As noted, some large and many smaller airlines adjudicate all of their matches at the ticket counter and no record is kept of the outcome. Many smaller airlines could not even speculate on a daily volume of watch list matches, much less a rate of false positives. Overall, there is no industry data available to estimate what percentage of domestic air passengers are affected by watch list matching performed by the covered aircraft operators. Consequently, TSA was unable to identify a watch list baseline for the industry.
International
The baseline watch list matching process for international passengers under Secure Flight is the process established by the APIS pre-departure final rule. Interested parties are referred to the preamble of the APIS final rule to learn about changes to the international watch list process.
Secure Flight operational testing will exercise and validate TSA’s ability to connect with the aircraft operators and the TSC, receive passenger and non-traveler information, conduct watch list matching, and transmit watch list results back to the aircraft operators using live data from SFPDs. Once the testing results achieve the program’s desired efficacy levels, Secure Flight will be implemented and TSA will receive the primary responsibility for airline passenger watch list matching.
Benefits of the rule occur in two phases: the first during operational testing and the second post-implementation. During operational testing, Secure Flight screens passengers in parallel with the airlines. Primary responsibility for watch list matching remains with covered aircraft operators during this period, but Secure Flight may notify aircraft operators if its watch list matching technology enables it to detect a potential match the aircraft operator may have missed. Therefore, during the operational testing phase, benefits include increased aviation security resulting from the detection of threats not identified by carriers participating in the testing.
Most of the rule’s benefits occur post-implementation. These include more accurate, timely, and comprehensive screening, and a reduction in false positives. This occurs because Secure Flight has access to more data than airlines with which to distinguish passengers from records in the watch lists. Further, the airlines will be relieved of watch list matching responsibilities, and TSA will be relieved of distributing the watch lists.
Other benefits include increased security due to the watch list matching of non-traveling individuals who request access to a sterile area. Also, the rule anticipates that TSA may allow airports also to authorize non-traveling individuals to enter the airport sterile area. As a result, the rule establishes requirements related to airports’ transmission of information from non-traveling individuals to Secure Flight for watch list matching. These requirements only apply to airports that request and receive authorization from TSA to grant non-traveling individuals access to the airport sterile area.
Once TSA assumes responsibility of watch list matching, and assuming passenger data provided to TSA matches the data on the government-issued identification, watch list matching should be more efficient and secure than methods the airlines currently have in place. The resources used by the government enable TSA to better focus its resources and security screening efforts on those passengers who are identified as likely to pose a threat to aviation security. This benefit is further augmented by the requirement that covered airlines must print on boarding passes a code generated by the Secure Flight system that is unique for each watch list result returned. Depending on the final implementation method, this requirement at a minimum allows checkpoint personnel to verify that a boarding or gate pass has been processed by the Secure Flight system.
Finally, the rule consolidates passenger prescreening operations within the department, thereby reducing redundancies between similar programs and facilitating better governance. The rule enables CBP to focus its resources on its mission of protecting U.S. borders while permitting TSA to apply its expertise in watch list matching consistently across all commercial air traffic within and overflying the United States. DHS expects that reducing overlap between these agencies’ missions will improve national security through more efficient and targeted use of national resources.
TSA has also conducted a “break-even” analysis which indicates the tradeoffs between program cost and program benefits (in the form of reductions in the baseline risk of a significant aviation-related terror attack) that would be required for Secure Flight to be a cost beneficial undertaking.
1.5.2 Improved Security and Additional Access for Non-traveling Individuals
The security benefits of passenger screening by Secure Flight also apply to the screening of non-traveling individuals. Secure Flight requires the airlines to submit the full name, date of birth, gender, and Redress Number (if available) of a non-traveling individual, along with the airport code of the airport to which access is being requested, to Secure Flight for watch list matching purposes before issuing the individual a pass to enter the sterile area. The rule also requires an aircraft operator representative to obtain other identifying information if TSA is unable to complete watch list matching for the individual.
TSA currently permits airlines to authorize non-traveling individuals to enter the sterile area if the individual has a permitted reason to do so, such as escorting a minor or a passenger with disabilities. The rule anticipates that TSA may allow airports to also authorize non-traveling individuals to enter the airport sterile area. As a result, the rule establishes requirements related to airports’ transmission of information from non-traveling individuals to Secure Flight for watch list matching. The requirements only apply to airports that request and receive authorization from TSA to grant non-traveling individuals access to the airport sterile area.
While approved programs are not strictly defined, these could include programs that would provide access to retail facilities within the sterile areas. Several airport operators have significant retail establishments within the sterile areas and individuals who are not currently permitted to access the sterile area are not permitted access to these establishments.
Once the initial testing period and parallel processing is completed, the reduction in the incidence of false positives through enhanced watch list matching processes becomes available. TSA will utilize the first phase to create benchmark data upon which to compare match rates in the future. The additional information required by the rule, date of birth, gender, and Redress Number, focuses security efforts on passengers and non-traveling individuals who truly pose a potential threat to aviation security. Passengers who have the same name as but a different gender from a record in the watch list will no longer be flagged as possible watch list matches and will not be subject to delays at the ticket counter, higher levels of screening, or the possibility of being denied boarding.
This reduction will be achieved through a multilayered approach. First, the additional personal data collected should contain enough uniquely identifying information to differentiate a false positive from a watch list match. Secondly, a TSA matching analyst compares the available information for any potential match to the Selectee and No Fly lists to classified and unclassified governmental terrorist, law enforcement, and intelligence databases25 in an attempt to distinguish a false positive from a watch list match prior to the individual’s arrival at the airport. Thirdly, Secure Flight will keep a limited record of close name matches that have been previously cleared to prevent those individuals from being flagged during future travel. Finally, a robust redress procedure has been implemented, enabling those who feel they have been incorrectly identified by TSA as a watch list match to submit paperwork to DHS’ Traveler Redress Inquiry Program (TRIP). If DHS should determine the redress applicant is not a person on the watch list, DHS adds the applicant’s name to a list of known misidentified persons to avoid future name matches and issue the person a Redress Number.
Extensive testing was done against a control group of known false positives and false negatives to evaluate the relative efficiencies gained from matching with various data elements. Date of birth, full name, and gender were selected based on their non-sensitive nature and value in reducing false positives. TSA did not receive sufficient baseline data, however, to quantify the net reduction of false positives under Secure Flight relative to the current rate of false positives.
The centralized watch list matching conducted through Secure Flight also allows for development of a centralized record of passengers and non-traveling individuals flagged as possible matches to a name in the Federal watch lists and subsequently cleared. Under the current system, these passengers and non-traveling individuals may experience delays each time they request access to a sterile area. Additionally, a robust redress procedure allows false positives to be added to a list of known misidentified persons. This list contains the names of all travelers who have completed DHS’ redress procedures and are deemed by DHS not to be a match to the individuals on the watch lists. As the names of false positives are added to these lists, fewer false positives will be generated by the Secure Flight system over time.
The false positive rate under Secure Flight will be affected by the stringency requirements determined during the testing phase and the size of the watch lists. Several methods and techniques exist to identify watch list matches using SFPD, and these can create a wide range of false positive rates. Only when Secure Flight operational testing is complete will a projected false positive rate be known.
1.5.4 Airlines Relieved of Watch List Responsibilities
Once TSA assumes primary responsibility for watch list matching and the airlines are no longer required to match passenger data in parallel, airlines will be relieved of passenger watch list matching responsibilities. For the purpose of the estimates in this analysis, TSA assumed that domestic implementation will be completed in the first year of the rule, and international implementation will be completed in the second year. However, the actual date the carriers will be completely relieved is not known at this time and is contingent on several factors, such as the impact of budgetary constraints and the results of operational testing. Prior to implementation, operational testing has to demonstrate that Secure Flight does not produce a large number of false positives, has the ability to process all matching requests in an efficient and accurate manner, and is fully integrated with a system of due process for passengers who believe they have been incorrectly delayed or denied boarding as a result of Secure Flight matching. Elimination of the watch list matching responsibilities should enable airlines to offset some costs imposed by the regulation by reallocating to other tasks some of their operational resources currently dedicated to comparing passenger information to the watch lists.
The amount of resources dedicated to watch list matching ranges significantly across airlines. Additionally, personnel tasked to conduct watch list matching often perform additional tasks as well. Some major airlines use more than 20 full-time employees and dedicated computer systems to conduct watch list matching and match adjudication. Other major airlines decentralize their matching procedures and require check-in agents to adjudicate many of the name matches. Smaller airlines may have the reservation agent conduct a simple name search in the watch list database to screen passengers. Due to the vast differences in resources used by each of the airlines for watch list matching and the uncertainty regarding the actual date each will be relieved of watch list duties, TSA was unable to quantify these cost savings.
Airlines currently screen passengers using the latest version of the watch lists distributed by TSA within the prescribed time period permitted. Variables such as the vigilance of personnel tasked to monitor TSA updates to the watch lists and the time to download and begin using these new lists can result in lags between the time when a name is added to a watch list and when it is incorporated into the matching process. Secure Flight uses the most recent data available in the extracted TSDB when comparing passenger information to the most current watch list and known misidentified persons list. Thus, passenger information screened under Secure Flight is ultimately more timely and accurate than the information used in current matching methods.
The automation and centralization of watch list matching allows for the matching to be more standardized and consistent. Current matching by the airlines is completed using different methods and techniques causing some travelers to be considered a match by one airline but not by others, resulting in frustration for travelers and differing levels of security across commercial passenger aviation. Secure Flight eliminates these differences by using a standard method for all matching.
1.5.6 Increased Watch List Security
Currently, TSA distributes the No Fly and Selectee lists to all air carriers required to perform watch list matching. Secure Flight improves the security of the watch lists by eliminating the mass distribution of the lists to the numerous air carrier personnel involved in the domestic passenger watch list matching process. This additional level of data control reduces the possibility of unauthorized individuals accessing or obtaining the watch lists.
While the distribution is reduced once airlines are fully relieved of watch list matching responsibilities, the watch lists will not be completely within the government domain. Small carriers not affected by this rule will still use the distributed watch lists for their passenger matching.
1.5.7 Consolidated Regulatory Policy
The regulation consolidates passenger pre-screening programs within the Department of Homeland Security. Channeling all pre-screening activities through one agency provides for increased program efficiencies and better governance. Consolidating two program offices that perform similar tasks can reduce redundancy. Consolidation also allows for better coordination within the government to remain responsive to both the airline industry and to traveling individuals, thereby generally improving governance.
1.5.8 Boarding Pass Authentication
TSA also requires covered airlines to print on boarding or gate passes a unique code generated by the Secure Flight system when returning watch list results for individuals requesting access to the sterile area. The benefits of this requirement vary, depending on how it is implemented. At minimum, this unique code enables checkpoint personnel to verify that a boarding pass had been processed by Secure Flight, precluding the use of forged passes. A more robust and costly implementation would allow checkpoint personnel to query the Secure Flight system and return the ID information and watch list status for the presented boarding or gate pass. Checkpoint personnel would then be able to verify whether the information on the presented ID matched the information that had been processed by the Secure Flight system.
A break-even analysis for a rulemaking such as Secure Flight is aimed at framing the relationships between the effects of the rulemaking (in increasing domestic security and reducing the risk of terror attack), the cost of implementing the rule, and the baseline risks of domestic terror attacks which would be improved by the rulemaking. Ideally, the quantification and monetization of the security benefits of this regulation would involve two steps. First, TSA would estimate the reduction in the probability of a successful terrorist attack resulting from implementation of the regulation and estimate the monetary value of the consequences of the avoided event (collectively, the risk associated with a potential terrorist attack). Then TSA would identify individuals’ willingness to pay for this incremental risk reduction and multiply it by the population experiencing the benefit. Both of these steps, however, rely on key data about risks and individual preferences that are not available for this analysis.
In light of these limitations, TSA conducted a “break-even” analysis to determine what reduction in overall risk of a terror attack and resulting reduction in the expected losses for the nation due to such a terror attack would be necessary in order for the expected benefits of the rule to exceed the costs. Because the types of attacks that would be prevented by this regulation vary widely in their intensity and effects, depending both on the intent of those undertaking the attack and their effectiveness in completing it, TSA considered three example attack scenarios and the monetized losses associated with each. Similar break-even analyses have been undertaken in support of other DHS rules, and TSA has coordinated the current analysis with these earlier ones, with the aim of maintaining consistency in DHS analyses and results. In the case of the Secure Flight rule, some of the types of terror attacks that might be undertaken using aircraft operated by those covered under the proposed rule are similar to those that have been considered by U.S. Customs and Border Protection (CBP), and this similarity has informed the current analysis and examples. For one scenario, however, TSA has relied on DHS research into the effects of successful delivery of a weapon of mass destruction (WMD) by an aircraft of the type affected by the proposed rule. The conclusions of this DHS research are consistent with results from existing academic and think tank research into similar issues.
In order to compare the losses associated with each scenario to the cost of the proposed rule, TSA converted casualties into a monetary total. TSA used the Value of a Statistical Life (VSL) of $5.8 million that is used by the Department of Transportation (DOT), and which was recently revised to reflect current academic and other research into this quantity.26 The VSL represents an individual’s willingness to pay to avoid a fatality onboard an aircraft, based on economic studies of the value individuals place on small changes in risk. TSA emphasizes that the VSL is a statistical value for regulatory comparison and does not suggest that the actual value of a life can be stated in dollar terms.
The following paragraphs present a description of the three scenarios considered by TSA with corresponding estimates of their monetary consequences. Together, these scenarios make up a wide range of possible consequences, which reflects the varied opportunities for attack and targeting that may exist for those intent on doing harm to the nation and its citizens. In order to compare direct costs to direct benefits, TSA only presents the direct economic losses estimated to ensue from the attack scenarios and has omitted economic “ripple effects,” “multiplier effects” and transfers from its calculations.
Scenario 1 involves the targeting of an aircraft for destruction, which would result in the complete loss of the aircraft and the deaths of all passengers and crew on board the aircraft. For this scenario, TSA has relied on official FAA guidance on aviation-related values for regulatory and investment analysis.27 The value and capacity of the average aircraft in the US fleet was used in these calculations, which include an average aircraft value of $21.9 million and an average of 132 souls on board the aircraft (which includes passengers and crew, calculated at an 80% load factor). Using the DOT VSL of $5.8 million, the monetary estimate associated with the loss of life is $766 million. Taken together, the monetary consequence of this scenario totals $0.79 billion.
Scenario 2 posits a situation where a large aircraft is used as a missile to carry out a direct attack on a building or building complex in a densely populated urban area. Because of these locational details, a successful attack would result in much more severe consequences, including significantly increased loss of life and widespread real property damage, compared to Scenario 1. This scenario requires terrorist control of the aircraft’s flight path. For valuation purposes for this scenario, TSA assumes 3,000 fatalities, valued at $17.4 billion using the DOT VSL of $5.8 million. To maintain consistency with existing DHS analyses, in particular the APIS analysis,28 TSA assumes property losses totaling $21.8 billion; this total is motivated by comparison to the City of New York Comptroller’s estimate of direct losses to the city due to the September 11 attacks.29 Finally, based on the FAA estimate of aircraft value, losses in Scenario 2 include $52.5 million due to complete hull loss of the aircraft used in the attack. The scenario elements aggregate to a total consequence of $39.25 billion.
Finally, Scenario 3 assumes a catastrophic situation in which an aircraft is used to deliver a nuclear or biohazard device to an urban center. This does not necessarily involve terrorist intrusion into the cockpit. This scenario has been examined by DHS in detail for a nuclear device.30 This research concludes that the consequences of such an event would be immense and highly uncertain. For the present analysis, TSA is using a value of $1 trillion for the direct consequences of an attack of this severity. This value falls in the midrange of values developed in the DHS research, and is consistent with results obtained from a review of academic and think tank research into the consequences of nuclear and bioterror attacks on urban areas. The value of $1 trillion results from loss of life in an attacked urban area in the hundreds of thousands and enormous loss of property and other productive assets.
To judge the value or effectiveness of the Secure Flight rule in the context of these scenarios, it is necessary to compare the scale of monetary consequence from successful attacks like those identified with the cost of the Secure Flight program that will be deployed to reduce the risk or likelihood of such an attack being successfully accomplished. The annual risk reductions required for the rule to break even under each of the three scenarios are presented in Table 1.5.9.a. In this analysis the comparison is made between the estimated scenario consequence and the Secure Flight undiscounted annualized cost of $326.2 million; the “required risk reduction” for breakeven is simply the ratio between this annualized program cost and the scenario consequence total. As shown, depending on the attack scenario, underlying baseline risk of terror attack would have to be reduced by approximately 0.83 percent (in the case of Scenario 2); 0.03 percent (in the case of Scenario 3); and 41 percent (in the case of Scenario 1) for the rule to break even with respect to the specific scenario consequence.
Table 1.5.9.a: Required Reduction in Annual Risk Required (%) for Secure Flight Annualized Undiscounted Costs ($326.2 M) to Equal Expected Benefits (Avoided Loss), by Attack Scenario
Scenario |
Scale |
Loss of Life |
Valuation at VSL of $5.8 M ($ billion) |
Hull Loss ($ billion) |
Property Loss ($ billion) |
Total Consequence ($ billion) |
Required Risk Reduction by SF |
1 |
AC as Target |
132 |
$0.77 |
$0.022 |
none |
$0.79 |
41.15% |
2 |
Major Impact |
3000 |
$17.4 |
$0.053 |
$21.8 |
$39.25 |
0.83% |
3 |
Catastrophic |
Large and Variable across Studies |
|
$1,000.0 |
0.03% |
||
While the “required risk reduction” due to Secure Flight can be quantified, the rule’s relationship to underlying baseline risk of attack (which is the risk that would be reduced by the Secure Flight program) can be more clearly illustrated graphically using a break even frontier. This is especially true because while the amount by which baseline risk must be reduced by Secure Flight if the Rule is cost-beneficial can be directly calculated as a ratio of program costs to attack consequences, the underlying baseline risk of an attack in any given year is highly uncertain, variable over time and in most cases can be calculated with greater accuracy only through reliance on security-sensitive information. Such a break-even frontier graphic is depicted in Figure 1.5.9.b.
Figure 1.5.9.b: Secure Flight Breakeven Frontier for Cost Beneficial Reduction of Annual Aviation Terror Attack Risk, by Attack Consequence (Annualized Undiscounted Secure Flight Primary Cost = $326.2 M)
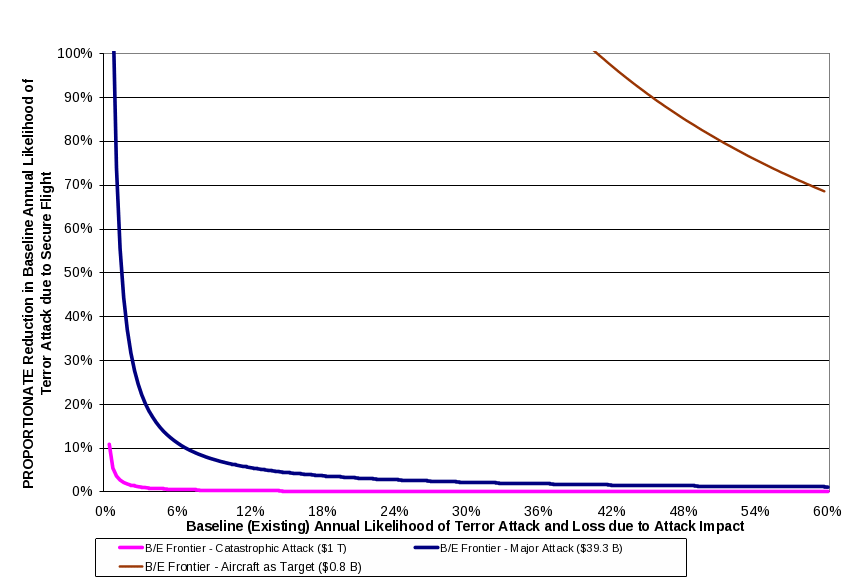
In the figure, breakeven curves are shown for each of the three attack consequence scenarios. Moving from the northeast corner of the figure in a southwesterly direction, the curves depict Scenario 1, Aircraft as Target, Scenario 2, Major Impact, and Scenario 3, Catastrophic Impact. Along the horizontal axis is measured the baseline annual probability or likelihood of a terror attack involving an aircraft. In the figure, these values run from 0 percent – no chance of such an attack – to 60 percent. (This axis could be extended to 100 percent – certainty that an attack would occur in a given year – but doing so adds little or nothing to the analysis and the presentation of the break-even frontiers.) This baseline risk may vary at different points in time, as geopolitical and other factors change, and different decision-makers may have different views and judgments on precisely what value or range of values is taken by the baseline risk. This baseline risk expresses the status quo security setting, which will be improved, at an annualized undiscounted cost of $381.3 million, by the Secure Flight requirements.
Along the vertical axis is the proportionate reduction in this baseline risk due to Secure Flight. These values range from 0 percent to 100 percent. A completely ineffective program would not reduce baseline risk at all (taking a 0 percent value on this axis) and a completely effective program, relative to baseline risk, would take a 100 percent value on this axis.
For a given breakeven frontier (loss scenario), points along the curve represent values of baseline risk and proportionate reduction in that risk for which the expected benefits of Secure Flight, represented by a reduction in the expected societal losses due to a successful terror attack, exactly offset the estimated annualized costs of the program. Points to the northeast of a specific frontier are cost-beneficial for that scenario, because they represent values for which the Secure Flight program provides more than enough annual risk reduction (and reduction in expected loss due to terror attack) to cover the annualized costs of the program. Points to the southwest of a frontier are not cost-beneficial with respect to the scenario, since they indicate that the program does not provide enough risk reduction – expressed in the figure as proportionate reduction in baseline risk – to justify the program costs. Because it depicts the relationship between baseline likelihood of an attack (of a given severity) and the extent to which the Secure Flight program reduces that baseline risk, the break-even frontier presentation is a useful tool for communicating to decision-makers some important tradeoffs related to the rule.
As indicated in the figure and the earlier table, for Scenario 1, Aircraft as Target, if the underlying baseline risk is less than 41.15 percent, the Secure Flight program is not cost beneficial, however effective it is, since on its own it must reduce baseline risk by at least 41.15 percent. At the other extreme, Scenario 3, Catastrophic Attack, given the size of the impact relative to the cost of Secure Flight, the program is cost beneficial requiring a 0.03 percent risk reduction to meet that criteria. For Scenario 2, Aircraft as Weapon, risk reduction must reach 0.83 percent for the Secure Flight to be cost.
This analysis divides the cost impact of the final rule into the following major categories: reprogramming of traveler reservation systems (1.6.2), burden of information collection (1.6.3 and 1.6.4), government infrastructure development (1.6.5), and opportunity cost to travelers and non-traveling individuals (1.6.6). Table 1.6.1.a presents projected annual costs for fiscal years 2008 through 2017. A discussion of each cost category follows the summary tables and explains in detail TSA’s derivation of the high and low scenario totals. All costs in this section are in undiscounted 2005 constant dollars unless otherwise noted.
Given the global nature of commercial aviation and the prevalence of airline partnerships, TSA was unable to divide the incidence of the estimated costs between the domestic and foreign economies. Thus, the table below presents the aggregate costs attributable to the Secure Flight rule. TSA has divided its discussion within each of the cost sections between domestic and international operations, reflecting the scope and phasing of the rule. However, this distinction between costs accruing to domestic and international operations should not be confused with costs to the domestic and foreign economies.
Table 1.6.1.a Total Secure Flight Costs, Millions of 2005 $ |
||||||||
|
Fiscal Year |
Airline Reprogramming Costs |
Airline Collection Costs |
Travel Agency Costs |
Federal Costs |
Total Cash Outlay |
Passenger Opportunity Costs |
Total Costs |
|
2008 |
$101.6 |
$11.0 |
$43.0 |
$100.6 |
$256.2 |
$74.5 |
$330.7 |
2009 |
183.8 |
11.5 |
27.3 |
139.6 |
362.1 |
77.0 |
439.1 |
|
2010 |
23.4 |
11.9 |
28.2 |
146.2 |
209.8 |
79.8 |
289.5 |
|
2011 |
24.3 |
12.3 |
29.2 |
135.6 |
201.4 |
82.7 |
284.0 |
|
2012 |
25.2 |
12.7 |
30.4 |
141.8 |
210.1 |
85.7 |
295.8 |
|
2013 |
26.1 |
13.3 |
31.4 |
146.4 |
217.2 |
88.8 |
306.0 |
|
2014 |
27.0 |
13.8 |
32.6 |
147.8 |
221.2 |
92.1 |
313.3 |
|
2015 |
28.1 |
14.2 |
33.8 |
150.4 |
226.5 |
95.4 |
321.9 |
|
2016 |
29.1 |
14.7 |
35.1 |
156.0 |
234.9 |
99.2 |
334.1 |
|
2017 |
$30.2 |
$15.3 |
$36.4 |
$163.0 |
$245.0 |
$102.9 |
$347.9 |
|
|
Primary |
$498.8 |
$130.7 |
$327.4 |
$1,427.5 |
$2,384.4 |
$877.9 |
$3,262.3 |
High |
$635.1 |
$156.6 |
$393.5 |
$1,675.4 |
$2,860.6 |
$961.6 |
$3,822.2 |
|
Low |
$362.4 |
$104.8 |
$260.6 |
$1,370.5 |
$2,098.3 |
$793.8 |
$2,892.1 |
|
Table 1.6.1.b shows annual total costs discounted at 7% and 3%.
Table 1.6.1.b Total Secure Flight Costs, Discounted 7% and 3% |
|||||
Fiscal Year |
Total Costs (millions) |
Total Annual Cost Discounted 7% (millions) |
3% Discount Factor |
Total Annual Cost Discounted 3% (millions) |
|
2008 |
$330.7 |
93.46% |
$309.1 |
97.09% |
$321.1 |
2009 |
439.1 |
87.34 |
383.5 |
94.26 |
413.9 |
2010 |
289.5 |
81.63 |
236.3 |
91.51 |
265.0 |
2011 |
284.0 |
76.29 |
216.8 |
88.85 |
252.2 |
2012 |
295.8 |
71.30 |
210.9 |
86.26 |
255.1 |
2013 |
306.0 |
66.63 |
203.9 |
83.75 |
256.2 |
2014 |
313.3 |
62.27 |
195.2 |
81.31 |
254.8 |
2015 |
321.9 |
58.20 |
187.4 |
78.94 |
254.1 |
2016 |
334.1 |
54.39 |
181.8 |
76.64 |
256.1 |
2017 |
347.9 |
50.83 |
176.8 |
74.41 |
258.9 |
Total, Primary Scenario |
$3,262.3 |
|
$2,301.8 |
|
$2,787.4 |
Total, |
$3,822.2 |
|
$2,693.3 |
|
3,264.1 |
Total, |
$2,892.2 |
|
$2,038.9 |
|
2,470.5 |
1.6.2 Airline Reprogramming and Implementation Costs
This section presents TSA’s estimates of costs for both domestic and international airlines to reprogram their systems in light of both TSA’s final rule and CBP’s recent APIS pre-departure final rule, which forms part of the international baseline of Secure Flight. Accordingly, TSA has assumed in its high scenario that all carriers subject to both the APIS and Secure Flight rules chose not to implement AQQ but waited to modify their systems until Secure Flight implementation. In the low scenario, TSA has assumed that 9 domestic marketing carriers in Group 1 and 2 domestic marketing carriers in Group 2 will implement AQQ in addition to 81 large foreign carriers subject to the Secure Flight rule.31 The true airline cost will likely lie somewhere between these two endpoints; without better information about likely airline decisions, TSA has adopted the midpoint for its primary scenario. An explanation of the overlap between the APIS and Secure Flight programs, as well as the reasoning behind TSA’s assumptions, is provided below and in Section 4.
Costs for Domestic Carriers
As discussed in Section 1.4.2, airlines incur costs to modify their individual reservation systems. In many cases, GDSs and host ARSs will make the changes necessary for each covered carrier to send SFPD to Secure Flight and receive watch list responses. Marketing carriers will make further modifications to their individual “in-house” systems in conjunction with the work performed by their GDS or host ARS. Since some airlines maintain their own reservation systems and because GDSs and host ARSs bill subscribing airlines for the work they perform, TSA has represented these simultaneous efforts as an aggregate airline cost.
In general, these modifications can be grouped into two categories: reprogramming and program implementation. Reprogramming includes such tasks as reprogramming the airline website to enable passengers to enter each component of their full name in a separate field, adding fields for date of birth, gender, and Redress Number, as necessary, and adding the privacy notice to web sites. Additional reprogramming requirements include modifying ticketing consoles and kiosks to accept and properly process the gate and boarding pass printing instructions returned by Secure Flight. Costs associated with program implementation include customer awareness campaigns, implementation support staff, and retraining of employees whose duties are affected by the requirements of the rule.
TSA conducted information-gathering interviews with a small number of airlines and ARS service providers as part of the research for the Secure Flight NPRM. Since the NPRM requirements for airlines have not been changed in the final rule, these interview responses also apply to the final rule. The eight airlines with which TSA spoke came from the diverse groups that make up the domestic passenger aviation industry, including legacy “hub and spoke” carriers, large and small “low cost” carriers that operate in a more point-to-point manner, smaller carriers that serve regional or niche markets, and carriers that provide charter services rather than scheduled passenger transportation. TSA also spoke with two providers of airline reservation system services. One of these is an ARS provider that has provided these services to legacy and other airlines throughout the world for many years, and the other is a more recently established company, providing web-based reservation services to airlines that are predominantly “low cost” operators from many parts of the world. The interviews were conducted in person and over the telephone.
The airlines and ARS providers interviewed were generally unable to assign precise costs for the software and hardware improvements and investments that are necessary for gathering and processing the additional data elements that is requested under the rule. In general, those reservation processes that relied on older computer programs and interfaces were expected to be the more expensive systems to modify, compared to newer systems that rely more on web-based software and applications. Airlines using hosted ARS services were unable to estimate the costs to their ARS service provider of enabling the use of the additional data elements called for under the rule, nor were they able to estimate the additional ARS costs the airlines themselves might face once modifications were successfully in place.
In TSA’s view, the lack of additional quantitative information developed from the interviews is regrettable but understandable. The airlines and ARS service providers interviewed were hesitant to estimate complex modification costs quickly, especially with limited information about the exact requirements that would exist under the rule. The complexity of these modifications increases for those carriers that rely on legacy computer systems, both for software modifications and hardware changes. Compounding this was the interview subjects’ natural concern over proprietary information that has competitive implications, especially for ARS service providers. Because of this, interview subjects were reluctant to comment officially on specific impacts of the rule in such a setting. Further, although TSA provided a preliminary copy of DHS’ Secure Flight/APIS implementation guidance and proposed requirements containing detailed information about the planned Secure Flight system, these airlines still preferred not to provide estimates.
As a result, TSA estimated reprogramming and implementation costs for Group 1 marketing carriers based upon an extrapolation of estimates provided by three legacy airlines and an independent cost estimate prepared by a Secure Flight subject matter expert. In general, these estimates provided little detail and TSA was unable to disaggregate them into comparable components. Estimates from the legacy carriers for reprogramming of their in-house reservation systems differed widely: $1,066,000, $1,700,000, and $2,358,000. The Secure Flight subject matter expert estimated average carrier reprogramming costs at $846,000. Without more specific information, TSA chose to use the average of these disparate estimates ($1,500,000) for Group 1 airline reprogramming costs.
Two of the legacy airlines also provided estimates of their costs to support implementation efforts, including customer awareness campaigns and retraining of staff. As before, these estimates differed by a wide margin: $400,000 and $4,000,000. TSA chose to adopt the lower estimate for inclusion in its calculations. This decision was driven by the greater detail accompanying the lower estimate and TSA’s assumption that, considering the range of airlines covered by Secure Flight, incorporating the higher estimate would overstate the likely expenditure of most airlines.
Two airlines and the TSA subject matter expert also provided general estimates of recurring costs. These costs principally reflect technical support and maintenance of the infrastructure installed or modified as a result of Secure Flight. Here the range was narrower: $166,000, $169,000, and $216,000. As with the reprogramming costs, TSA chose to use the average of these estimates ($184,000) in its calculation.
Based on these inputs, TSA estimated airline reprogramming results in an initial cost of $1,500,000 per marketing carrier in Group 1 and recurring costs of $184,000 per year. Implementation costs add $400,000 during the initial phase with no recurring costs.
TSA was unable to discern whether the provided estimates included modifications to affiliated carriers’ systems as well. Without actual estimates from these carriers, TSA did not estimate additional reprogramming costs for affiliated carriers.
Given the sparse available data regarding airline reprogramming costs, TSA subject matter experts assumed reprogramming for marketing carriers in Groups 2 and 3 will be 50% and 25%, respectively, of the costs incurred by Group 1 carriers. Group 4 carriers will use the Secure Flight web interface rather than reprogram any existing systems they may have. Consequently, the minimum equipment a Group 4 carrier needs will be a personal computer, an internet connection, and a commercial spreadsheet or database application. TSA assumed all Group 4 carriers already have this equipment; therefore, no reprogramming or recurring costs are assigned to this group. Given the diversity of airlines included in this group, however, TSA assumed some incur costs for customer awareness and retraining of staff. Without specific information about likely airline expenditures, TSA assumed Group 4 carriers will spend comparable sums on implementation as Group 3 carriers ($400,000 x 25% = $100,000) in cases where Group 4 carriers had revenue, employment, and enplanement totals similar to Group 3. Thirteen of the 16 Group 4 carriers met these criteria and are included in the calculations below. Table 1.6.2.a presents the unit initial and recurring costs for domestic carriers.
In the low scenario, TSA assumed that 9 marketing carriers in Group 1 and 2 marketing carriers in Group 2 implemented AQQ in response to CBP’s APIS rule and prior to the implementation of Secure Flight. These 11 marketing carriers are assumed to incur implementation costs in the first year of Secure Flight but not need to make reprogramming changes. The remaining covered domestic operators incur both reprogramming and implementation costs.
In the high scenario, TSA assumed that all carriers covered by Secure Flight have not implemented AQQ but will reprogram their systems during Secure Flight implementation. Tables 1.6.2.b and 1.6.2.c present the total initial and recurring costs under the low and high scenarios.
Table 1.6.2.b Total Initial and Recurring Marketing Carrier Costs, Domestic High Scenario |
||||||||
Carrier Type |
# of Carriers |
Initial Reprogram Costs per Carrier |
# of Carriers |
Implementation Costs per Carrier |
Total Initial Costs |
# of Carriers |
Recurring Costs per Carrier |
Total Recurring Cost per Year |
Group 1 |
10 |
$6,500,000 |
10 |
$400,000 |
$69,000,000 |
10 |
$184,000 |
$1,800,000 |
Group 2 |
8 |
$4,880,000 |
8 |
$300,000 |
$41,400,000 |
8 |
$140,000 |
$1,100,000 |
Group 3 |
9 |
$1,625,000 |
9 |
$100,000 |
$15,500,000 |
9 |
$46,000 |
$400,000 |
Group 4 |
13 |
$650,000 |
13 |
$100,000 |
$9,800,000 |
13 |
$18,400 |
$239,200 |
Total |
40 |
|
40 |
|
$135,700,000 |
40 |
|
$3,500,000 |
Table 1.6.2.c Total Initial and Recurring Marketing Carrier Costs, Domestic Low Scenario |
||||||||
Carrier Type |
# of Carriers |
Initial Reprogram Costs per Carrier |
# of Carriers |
Implementation Costs per Carrier |
Total Initial Costs |
# of Carriers |
Recurring Costs per Carrier |
Total Recurring Cost per Year |
Group 1 |
1 |
$6,500,000 |
10 |
$400,000 |
$10,500,000 |
1 |
$184,000 |
$184,000 |
Group 2 |
6 |
$4,880,000 |
8 |
$300,000 |
$31,700,000 |
6 |
$140,000 |
$840,000 |
Group 3 |
9 |
$1,625,000 |
9 |
$100,000 |
$15,500,000 |
9 |
$46,000 |
$414,000 |
Group 4 |
13 |
$650,000 |
13 |
$100,000 |
$9,800,000 |
13 |
$18,400 |
$239,200 |
Total |
29 |
|
40 |
|
$67,500,000 |
29 |
|
$1,700,000 |
Table 1.6.2.d presents the ten-year costs for domestic marketing airlines. The primary scenario is the midpoint of the high and low scenarios.
Table 1.6.2.d Total Domestic Reprogramming and Implementation Costs (millions of 2005 $) |
|||
Year |
Primary Scenario |
Low Scenario |
High Scenario |
1 |
$101.6 |
$67.5 |
$135.7 |
2 |
2.6 |
1.7 |
3.5 |
3 |
2.6 |
1.7 |
3.5 |
4 |
2.6 |
1.7 |
3.5 |
5 |
2.6 |
1.7 |
3.5 |
6 |
2.6 |
1.7 |
3.5 |
7 |
2.6 |
1.7 |
3.5 |
8 |
2.6 |
1.7 |
3.5 |
9 |
2.6 |
1.7 |
3.5 |
10 |
$2.6 |
$1.7 |
$3.5 |
Total |
$125.0 |
$82.8 |
$167.2 |
Secure Flight and APIS Quick Query
Concurrent with the publication of the Secure Flight NPRM, U.S. Customs and Border Protection (CBP) published a final rule modifying requirements for air carriers subject to its Advance Passenger Information System (APIS) regulations. The modification requires air carriers operating flights to or from the United States to submit passenger manifests prior to the aircraft’s departure. Previously, carriers subject to CBP regulations submitted these manifests after the departure of the aircraft.
Under previous regulations and security directives, international carriers (a term here collectively referring to U.S. and foreign air carriers operating flights between a U.S. city and a foreign port) were responsible for comparing passenger information to the U.S. government No Fly and Selectee lists, denying boarding to individuals who are determined to be a No Fly match and identifying Selectees for enhanced screening. These carriers then submitted to CBP a passenger manifest after the departure of the flight. This information was used for a variety of border enforcement purposes, including a second check of the passengers against the No Fly list. In some cases, this follow up comparison led to the diversion of flights carrying passengers CBP suspected of being on the No Fly list, resulting in lengthy delays and highlighting the need for a more reliable means of preventing terrorist suspects from boarding an aircraft.
The APIS final rule transferred the responsibility for conducting watch list matching from the airlines to CBP. CBP requires international air carriers to submit passenger information prior to departure and to withhold a passenger’s boarding pass until the airline has received a watch list response for that passenger. The watch list results are identical to those that are returned by Secure Flight: “cleared,” “selectee,” or “inhibited.” Inhibited passengers are not issued a boarding pass.
Recognizing that inserting this requirement into the international check-in process could result in costly delays or passengers missing their flights, CBP developed a system known as APIS Quick Query (AQQ). This automated system has the capability to receive a passenger record from an airline and return a gate or boarding pass printing instruction in a matter of seconds. Carriers that chose to modify their computer systems to support this interactive messaging capability incurred significant costs. Nevertheless, some carriers, particularly those handling large volumes of connecting and business travelers determined the expense to be justified.
Since many of the carriers for which AQQ is a viable option are also subject to the Secure Flight requirements, DHS purposely coordinated the publication of CBP’s final rule and TSA’s NPRM in order to provide carriers with as much information as possible to inform their business decisions. For example, to minimize airline reprogramming for carriers choosing to implement AQQ, DHS built a router that receives all information submitted from the airlines. This router extracts only the information required by DHS and sends it to the appropriate agency. Thus, prior to Secure Flight, all information goes to CBP. As Secure Flight becomes operational, however, the router sends information needed for border enforcement to CBP and information needed for watch list matching to TSA.
Although DHS is taking such steps to minimize the impact to airlines, the Secure Flight requirements require some changes of the airlines beyond what is specified in the APIS final rule. Given that Secure Flight performs matching not only for most international passengers covered by APIS but also for all passengers aboard covered U.S. carriers and passengers overflying the U.S., TSA has determined these changes are necessary to enable TSA to handle the anticipated volume of watch list matching requests. Thus, under Secure Flight airlines must submit their passenger information required for watch list matching, as available, beginning approximately 72 hours prior to the scheduled departure of the flight. In order to comply with this requirement, airlines are required to obtain each passenger’s full name, date of birth, gender, and, if available, a Redress Number. DHS assumes airlines will build this requirement into their existing reservation processes; however, the regulation does not require this if airlines find it cost-effective to adopt a different approach. Presently, airlines reporting to APIS collect passenger information during the check-in process, often through a passport swipe.
Other than this change, however, DHS has attempted to make the Secure Flight requirements as close as possible to the APIS process. This is both to minimize the costs for airlines that are fully operational in APIS prior to the Secure Flight transition, and to allow airlines to take advantage of direct or indirect experience they have gained with the APIS program when implementing Secure Flight. For example, after the required 72 hour batch transition of available information, the airlines may transition to an AQQ format as the departure time approaches, or they may continue to update information in batch mode. In substance, DHS has sought to ensure that the Secure Flight transmission requirements are identical to those established in the APIS final rule, with the exception of the initial 72-hour transmission. As a result, aside from the initial transmission requirements, the requirements of Secure Flight are identical to the baseline created by the APIS pre-departure final rule.
Given these considerations, CBP estimated a broad range of costs when evaluating airline decisions to implement AQQ in response to CBP’s final rule. Recognizing this same uncertainty and to avoid double-counting, TSA has adopted these assumptions in estimating its range of airline reprogramming and implementation costs to comply with this TSA final rule. Accordingly, TSA has assumed in its high scenario that all carriers subject to both the APIS and Secure Flight rules have chosen not to implement AQQ but are waiting to modify their systems until Secure Flight implementation. In the low scenario, TSA has assumed that 9 domestic marketing carriers in Group 1 and 2 domestic marketing carriers in Group 2 implemented AQQ in addition to 81 large foreign carriers subject to the Secure Flight rule.32 DHS assumed the true airline cost likely lies somewhere between these two endpoints, but without better information about airline decisions, TSA adopted the midpoint for its primary scenario. DHS also notes that CBP thoroughly analyzed the impact of adopting APIS AQQ versus adopting batch mode requirements in the international setting, before the transition to Secure Flight, in the regulatory impact assessment accompanying the APIS pre-departure final rule.
Costs for Foreign Carriers
To estimate costs for foreign carriers, TSA relied upon the estimates provided in the regulatory impact assessment accompanying CBP’s 2007 final rule establishing pre-departure APIS requirements. In its evaluation, CBP estimates that carriers choosing to implement APIS Quick Query (AQQ) will incur an initial cost of $2,000,000. TSA adopted this unit cost estimate for covered large foreign carriers that choose to wait until Secure Flight is implemented before reprogramming their systems to enable interactive queries. In keeping with CBP’s estimates, TSA assumed this total includes implementation as well as reprogramming costs. Although foreign carriers are required to implement Secure Flight on a date specified by TSA, this analysis anticipates these costs occurring in fiscal year 2009, one year after domestic implementation. To estimate recurring costs for foreign air carriers, TSA considered recurring costs as 2.8 percent of the implementation cost. This is consistent with the recurring costs associated with domestic carriers.
In the high scenario, TSA assumed that 81 covered foreign operators have waited until Secure Flight is implemented to reprogram their systems for interactive queries. In both its high and low scenarios, CBP assumed that small foreign carriers will not implement APIS Quick Query but will instead simply change the timing of their transmissions and continue to submit passenger information to CBP as they currently do. TSA thus assumed that these small carriers, like domestic Group 4 carriers, incur initial implementation costs of $100,000 in the year they are connected to Secure Flight. Table 1.6.2.e presents costs to covered foreign carriers under this high scenario.
Table 1.6.2.e Total Initial and Recurring Carrier Costs, Foreign High Scenario |
||||||||
Carrier Type |
# of Carriers |
Initial Reprogram Costs per Carrier |
# of Carriers |
Implementation Costs per Carrier |
Total Initial Costs |
# of Carriers |
Recurring Costs per Carrier |
Total Recurring Cost per Year |
Large Foreign |
81 |
$2,000,000 |
N/A |
N/A |
$162,000,000 |
81 |
$53,300 |
$4,317,000 |
Small Foreign |
N/A |
N/A |
65 |
$100,000 |
$6,500,000 |
65 |
$0 |
$0 |
Total |
81 |
|
65 |
|
$168,500,000 |
146 |
|
$0 |
In the low scenario, TSA assumed that the 81 covered large foreign carriers chose to implement AQQ prior to Secure Flight and do not need to undertake any further substantial reprogramming to comply with Secure Flight. Some retraining of staff and other minor modifications to systems may be necessary, however, to address differences between the APIS and Secure Flight rules. Additionally, under the rule, these operators are required to develop an Aircraft Operator Implementation Plan (AOIP) detailing how the carrier intends to implement Secure Flight. TSA subject matter experts estimated it should take a carrier already connected to AQQ no more than 200 man hours to complete the AOIP. TSA thus assumed these carriers will expend initial implementation costs of $400,000, equivalent to domestic Group 1 carriers. Similarly, TSA again assumed covered small foreign carriers will experience implementation costs of $100,000. Table 1.6.2.f presents costs to covered foreign carriers under this low scenario.
Table 1.6.2.f Total Initial and Recurring Carrier Costs, Foreign Low Scenario |
||||||||
Carrier Type |
# of Carriers |
Initial Reprogram Costs per Carrier |
# of Carriers |
Implementation Costs per Carrier |
Total Initial Costs |
# of Carriers |
Recurring Costs per Carrier |
Total Recurring Cost per Year |
Large Foreign |
0 |
$2,000,000 |
81 |
$400,000 |
$32,400,000 |
81 |
$49,100 |
$3,977,000 |
Small Foreign |
N/A |
N/A |
65 |
$100,000 |
$6,500,000 |
65 |
$0 |
$0 |
Total |
0 |
|
146 |
|
$38,900,000 |
146 |
|
$0 |
In its final APIS regulatory evaluation, CBP included in its estimates for carriers choosing to implement AQQ a cost of $0.20 per passenger to transmit each passenger’s information to DHS and receive back a message response. TSA was unable to reliably determine prior to publication of the Secure Flight NPRM how this per passenger fee would be affected by the significantly larger passenger population covered by Secure Flight. TSA did not receive any input addressing this estimate and therefore it is an unknown. Corresponding to its other efforts to align TSA’s assumptions with CBP’s, TSA estimated costs for low, primary, and high scenarios. In the low scenario, TSA assumed all airlines implemented AQQ in advance of Secure Flight; therefore, TSA calculated costs only for the difference between the international population covered by Secure Flight and the APIS population. In the high scenario, TSA assumed that all carriers waited until Secure Flight is implemented to invest in interactive query technology. As a result, TSA applied the $0.20 message fee to all international reservations covered by Secure Flight. The primary scenario is the average of these two estimates. As with the foreign airline reprogramming estimates, TSA assumed these costs are not incurred until the second year of the Secure Flight program. Table 1.6.2.g presents the estimated message costs.
Table 1.6.2.g Potential Secure Flight Message Fees (millions of 2005 $) |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
2008 |
$0.0 |
$0.0 |
$0.0 |
2009 |
$15.9 |
$7.2 |
$24.6 |
2010 |
$16.7 |
$7.5 |
$25.8 |
2011 |
$17.5 |
$7.9 |
$27.1 |
2012 |
$18.4 |
$8.3 |
$28.5 |
2013 |
$19.3 |
$8.7 |
$29.9 |
2014 |
$20.3 |
$9.2 |
$31.4 |
2015 |
$21.3 |
$9.6 |
$33.0 |
2016 |
$22.4 |
$10.1 |
$34.6 |
2017 |
$23.5 |
$10.6 |
$36.4 |
Total |
$175.3 |
$79.3 |
$271.4 |
TSA notes that the Secure Flight requirement that airlines submit available passenger information approximately 72 hours prior to departure may have a significant impact on covered airlines, particularly those that are unable to establish a direct connection to CBP. This impact may be compounded by TSA’s decision in the rule to require covered airlines to bear the responsibility for all implementation costs. Thus, covered airlines bear any applicable transmission costs associated with both submission of SFPD information to DHS and return transmissions containing watch list results.
Table 1.6.2.h presents the total estimated costs for covered foreign airlines under the high and low scenarios. Again, without more detailed information on how carriers have responded to the APIS final rule, TSA has adopted the midpoint of these estimates as its primary scenario.
Table 1.6.2.h Total Foreign Reprogramming and Implementation Costs (millions of 2005 $) |
|||
Year |
Primary Scenario |
Low Scenario |
High Scenario |
2008 |
$0.0 |
$0.0 |
$0.0 |
2009 |
$181.2 |
$175.7 |
$186.6 |
2010 |
$20.8 |
$11.5 |
$30.2 |
2011 |
$21.7 |
$11.9 |
$31.5 |
2012 |
$22.6 |
$12.3 |
$32.8 |
2013 |
$23.5 |
$12.7 |
$34.2 |
2014 |
$24.4 |
$13.2 |
$35.7 |
2015 |
$25.5 |
$13.6 |
$37.3 |
2016 |
$26.5 |
$14.1 |
$39.0 |
2017 |
$27.6 |
$14.6 |
$40.7 |
Total |
$373.8 |
$279.6 |
$467.9 |
Table 1.6.2.i presents the initial, recurring and total costs for both covered domestic and foreign carriers over the next ten years.
Table 1.6.2.i Total Annual Reprogramming and Implementation Costs, All Carriers (millions of 2005 $) |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
2008 |
$101.6 |
$67.5 |
$135.7 |
2009 |
183.8 |
177.4 |
190.1 |
2010 |
23.4 |
13.2 |
33.7 |
2011 |
24.3 |
13.6 |
35.0 |
2012 |
25.2 |
14.0 |
36.3 |
2013 |
26.1 |
14.4 |
37.7 |
2014 |
27.0 |
14.9 |
39.2 |
2015 |
28.1 |
15.3 |
40.8 |
2016 |
29.1 |
15.8 |
42.5 |
2017 |
$30.2 |
$16.3 |
$44.2 |
Total |
$498.8 |
$362.4 |
$635.1 |
TSA requires airlines to print a separate code on boarding passes for the purpose of enabling security personnel to authenticate boarding passes at the checkpoint. TSA provides this code to covered aircraft operators when returning the gate or boarding pass printing instruction for a passenger. As proposed in the NPRM, this code will be printed separately from any other code on the boarding pass. TSA was unable to find data on the cost this requirement might impose upon covered airlines.
1.6.3 Airline Data Collection Costs
Under the rule, airline passenger reservation agents are required to collect additional passenger information at the time of reservation. Due to differences in population, TSA has broken the estimate into two larger categories, domestic passengers and international passengers.
Additionally, airline ticket counter agents are required to request additional information for those passengers who will be initially inhibited from receiving a boarding pass. TSA has estimated the costs for collecting information at the time of reservation for both domestic and international flights, as discussed below. TSA did not have information on the use of profiles within the air travel industry and thus applied the incremental time cost to all reservations.
Domestic passengers
The primary impact on covered carriers resulting from collection of additional passenger information is the additional time requirements for their reservation agents. Airlines accept reservations by telephone via their reservation call centers. As discussed in Section 1.4.2, TSA estimated in its primary scenario that reservation agents need an average of an additional 25 seconds to collect full name, date of birth, gender, and Redress Number. The costs associated with collecting this information are incurred for all reservations.
Twenty seconds of incremental time represents an additional 323,000 hours in the first year of implementation for airline call centers. This estimate was calculated by multiplying the share of reservations attributable to airline call centers from Table 1.4.2.b by the 25 seconds of incremental time (58,100,000 reservations x 25 seconds = 1,452,500,000 seconds, or, 403,000 hours). Using the Bureau of Labor Statistics fully loaded wage rate of $20.89 for ticket reservation agents, TSA estimated the cost of data collection at $8.4 million in the first year of implementation of Secure Flight (403,000 x $20.89). Table 1.6.3.a shows the 10-year cost of collection for ticket reservation agents at airline reservation call centers, for the primary, low and high scenarios.
Table 1.6.3.a Cost of Data Collection for Airline Reservation Call Centers, Domestic Passengers |
||||||||
Fiscal Year |
Airline Call Center Reservations (millions) |
Total Additional Hours, Primary Scenario |
Total Additional Hours, Low Scenario |
Total Additional Hours, High Scenario |
Call Center Agent Hourly Wage |
Total Cost, Primary Scenario (millions) |
Total Cost, Low Scenario (millions) |
Total Cost, High Scenario (millions) |
|
(A) |
(B) |
(C) |
(D) |
(E) |
(B x E) |
(C x E) |
(D x E) |
2008 |
58.1 |
403,000 |
323,000 |
484,000 |
$20.89 |
$8.4 |
$6.7 |
$10.1 |
2009 |
59.9 |
416,000 |
333,000 |
499,000 |
$20.89 |
8.7 |
7.0 |
10.4 |
2010 |
61.8 |
429,000 |
343,000 |
515,000 |
$20.89 |
9.0 |
7.2 |
10.8 |
2011 |
63.7 |
442,000 |
354,000 |
531,000 |
$20.89 |
9.2 |
7.4 |
11.1 |
2012 |
65.8 |
457,000 |
366,000 |
548,000 |
$20.89 |
9.5 |
7.6 |
11.4 |
2013 |
67.9 |
472,000 |
377,000 |
566,000 |
$20.89 |
9.9 |
7.9 |
11.8 |
2014 |
70.1 |
487,000 |
389,000 |
584,000 |
$20.89 |
10.2 |
8.1 |
12.2 |
2015 |
72.3 |
502,000 |
402,000 |
603,000 |
$20.89 |
10.5 |
8.4 |
12.6 |
2016 |
74.7 |
519,000 |
415,000 |
623,000 |
$20.89 |
10.8 |
8.7 |
13.0 |
2017 |
77.3 |
537,000 |
429,000 |
644,000 |
$20.89 |
$11.2 |
$9.0 |
$13.5 |
Total |
|
|
|
|
|
$97.4 |
$78.0 |
$116.9 |
Airline reservation agents need to be retrained on the updated software and reservation procedures. These costs are included in the reprogramming and implementation costs presented in the preceding section.
This rule also affects airlines’ ticket counter agents. Based on its understanding of the Secure Flight program in 2004, one major airline believed the requirements of Secure Flight could require passengers to spend more time at the ticket counter for identification verification and other security purposes during check-in. In order to maintain current passenger flow levels and avoid delays, the airline believed additional ticket counter agents would need to be hired. Until operational testing reveals the actual rate of possible No Fly matches requiring further adjudication at the counter, TSA could not determine whether this impact will come to pass. Secure Flight should reduce the number of passengers stopped at the ticket counter; thus, any increase in counter adjudication times may be offset by a reduction in the number of affected passengers.
As discussed in Section 1.4.1, Group 4 carriers are required to transmit passenger information to Secure Flight through a secure web interface. At the time of writing, this interface was still in the development phase. As envisioned, the web interface allows aircraft operators to enter passenger information directly into the system or upload and submit a specifically formatted file.
If the airline should choose to enter passenger information manually (as may be the case for certain small scheduled service carriers accepting reservations over the phone or when an operator needs to enter updated information for a specific passenger during the clearance process), the operator is required to enter information about the flight and then information about each passenger. Flight information may include such data elements as the carrier code, flight number, departure date and time, arrival date and time, and the departure and arrival airport codes. TSA estimated it should take no longer than 15 seconds to enter this information. Passenger information is identical to the passenger data elements required of all aircraft operators under this regulation. TSA estimated it may take 30 seconds to enter this information for each passenger. Reservations accepted over the telephone may require an additional 30 seconds for each reservation.
Since these requirements would impose a disproportionate burden on this group of carriers relative to Groups 1-3, DHS intends to design the web interface such that Group 4 operators can upload a specifically formatted file. TSA assumed that carriers with web reservation systems will be able to make modifications that will enable the reservation system to export reservations into the specified file format for upload to Secure Flight. TSA further assumed that carriers accepting charter reservations will develop a template file containing the information required for transmission to Secure Flight and require that manifests be submitted to them in this format. One charter carrier has already implemented such a procedure in response to similar passenger information requirements imposed by CBP for international flights.
Table 1.4.2.c presents projected reservations for Group 4 carriers. In light of the fact that the Secure Flight web interface is being finalized at the time of writing and TSA has no data on the number or distribution of reservations accepted by each carrier, TSA did not base any estimates on the assumptions presented above. The carriers using this web interface will not be required to transmit data to Secure Flight until after the interface is operational.
International Travelers
TSA used the same method to estimate the costs associated with international travelers as presented for domestic passengers above. As is the case for domestic carriers, international carriers also need to collect SFPD at the time of reservation.33 TSA recognizes that international carriers operating a flight subject to CBP’s APIS requirements will likely collect the SFPD a second time through a passport swipe at a ticket counter when they collect the more extensive APIS information at check in. TSA views the collection of the Secure Flight passenger data during the reservation process and subsequent transmission to TSA 72 hours prior to departure as necessary in order to allow TSA sufficient time to prioritize and process the incoming data in advance of passenger check in. TSA views the information collected through the passport swipe to be a vital follow-up, which helps to further clear passengers who may initially match the watch lists by providing TSA with additional or corrected information, such as passport number, date of birth, and gender, if these elements were not previously provided.
TSA did not have information on the distribution of international reservations between online, airline call center, and travel agent booking methods. Without this information, TSA chose to use its domestic estimates as a proxy, although the agency recognizes that travel agencies may represent a larger share of international reservations.
TSA has separated its international estimates between covered passengers flying to and from the United States (also subject to APIS) and covered passengers overflying the United States (not subject to APIS). First, TSA has estimated the impact for all international passengers traveling to or from the U.S. This population has been segregated from domestic travelers because they will be implemented at a later date than passengers flying domestic routes. Further, not all of these costs occur within the U.S. economy. For instance, some U.S. flagged carriers code-share flights with foreign airlines. As a result, a passenger may call a U.S. airline’s reservation center and be booked on a foreign airline. Thus, though the incremental cost for that reservation attributable to Secure Flight is borne by a domestic airline’s reservation agent, the traveler appears among a foreign operator’s passenger totals. Conversely, a passenger may call a foreign airline’s reservation center and be booked on a flight operated by a domestic airline. TSA was unable to find information on the frequency with which this occurs and thus was unable to determine what proportion of the incremental costs presented below occurs within the U.S. economy. TSA has therefore included all related costs in this analysis, regardless of national economic divisions.
The marginal cost to airlines for collecting additional information at the time of reservation for international passengers traveling to and from the U.S. is $23.9 million. This estimate was developed in the same manner as the costs for collecting information for domestic passengers. Detailed year-by-year estimates are in Table 1.6.3.b.
Table 1.6.3.b Cost of Data Collection for Airline Reservation Call Centers, International Passengers |
||||||||
Fiscal Year |
Airline Call Center Reservations (millions) |
Total Additional Hours, Primary Scenario |
Total Additional Hours, Low Scenario |
Total Additional Hours, High Scenario |
Call Center Agent Hourly Wage |
Total Cost, Primary Scenario (millions) |
Total Cost, Low Scenario (millions) |
Total Cost, High Scenario (millions) |
|
(A) |
(B) |
(C) |
(D) |
(E) |
(B x E) |
(C x E) |
(D x E) |
2008 |
13.0 |
90,000 |
73,000 |
108,000 |
$20.89 |
$1.9 |
$1.6 |
$2.2 |
2009 |
13.7 |
95,000 |
76,000 |
115,000 |
20.89 |
2.0 |
1.6 |
2.4 |
2010 |
14.4 |
100,000 |
80,000 |
120,000 |
20.89 |
2.1 |
1.7 |
2.5 |
2011 |
15.1 |
105,000 |
84,000 |
126,000 |
20.89 |
2.2 |
1.8 |
2.6 |
2012 |
15.8 |
110,000 |
87,000 |
132,000 |
20.89 |
2.3 |
1.8 |
2.8 |
2013 |
16.6 |
115,000 |
93,000 |
138,000 |
20.89 |
2.4 |
2.0 |
2.9 |
2014 |
17.4 |
121,000 |
97,000 |
145,000 |
20.89 |
2.6 |
2.0 |
3.0 |
2015 |
18.4 |
128,000 |
103,000 |
154,000 |
20.89 |
2.7 |
2.2 |
3.2 |
2016 |
19.2 |
133,000 |
107,000 |
160,000 |
20.89 |
2.8 |
2.2 |
3.4 |
2017 |
20.2 |
140,000 |
113,000 |
168,000 |
$20.89 |
$2.9 |
$2.4 |
$3.5 |
Total |
|
|
|
|
|
$23.9 |
$19.3 |
$28.5 |
The rule requires covered foreign air carriers to also request full names, dates of birth, gender, and Redress Numbers from passengers flying over the U.S. While U.S. regulations do not currently require these carriers to submit information to DHS for such passengers, the additional data elements airlines need to request during the reservation process is identical to those identified for the above populations. For this reason, the marginal burden estimates used for flights to and/or from the U.S. are also a reasonable approximation of the marginal burden for overflights. Using the same method as for domestic and international flights, TSA estimated the marginal cost of collecting additional information from over-flight passengers at the time of reservation at $9.4 million. Detailed estimates by year are in Table 1.6.3.c.
Table 1.6.3.c Cost of Data Collection for Airline Reservation Call Centers, Overflights |
||||||||
Fiscal Year |
Airline Call Center Reservations (millions) |
Total Additional Hours, Primary Scenario |
Total Additional Hours, Low Scenario |
Total Additional Hours, High Scenario |
Call Center Agent Hourly Wage |
Total Cost, Primary Scenario (millions) |
Total Cost, Low Scenario (millions) |
Total Cost, High Scenario (millions) |
|
(A) |
(B) |
(C) |
(D) |
(E) |
(B x E) |
(C x E) |
(D x E) |
2008 |
5.1 |
35,000 |
28,000 |
43,000 |
$20.89 |
$0.7 |
$0.6 |
$0.9 |
2009 |
5.4 |
38,000 |
30,000 |
45,000 |
20.89 |
0.8 |
0.6 |
0.9 |
2010 |
5.7 |
40,000 |
32,000 |
48,000 |
20.89 |
0.8 |
0.7 |
1.0 |
2011 |
5.9 |
41,000 |
33,000 |
49,000 |
20.89 |
0.9 |
0.7 |
1.0 |
2012 |
6.2 |
43,000 |
34,000 |
52,000 |
20.89 |
0.9 |
0.7 |
1.1 |
2013 |
6.6 |
46,000 |
37,000 |
55,000 |
20.89 |
1.0 |
0.8 |
1.1 |
2014 |
6.9 |
48,000 |
38,000 |
58,000 |
20.89 |
1.0 |
0.8 |
1.2 |
2015 |
7.2 |
50,000 |
40,000 |
60,000 |
20.89 |
1.0 |
0.8 |
1.3 |
2016 |
7.6 |
53,000 |
42,000 |
63,000 |
20.89 |
1.1 |
0.9 |
1.3 |
2017 |
8.0 |
56,000 |
44,000 |
67,000 |
$20.89 |
$1.2 |
$0.9 |
$1.4 |
Total |
|
|
|
|
|
$9.4 |
$7.5 |
$11.2 |
As is the case with domestic passengers, TSA is unable to determine the burden on airline ticket counter agents due to changes in the proportion of and time to resolve inhibited passengers. However, because international travel generally requires the presentation of a passport and more extensive baseline data, the marginal impact of collecting more data at the ticket counter is likely to be less of an impact than for domestic operations
Airline Data Collection Cost Summary
Combined, airlines incur $130.7 million over ten years to collect the additional information at the time of reservation in the primary scenario. Table 1.6.3.d shows year-by-year estimates.
Table 1.6.3.d Total Marginal Cost for Airline Reservation Call Centers (millions of constant 2005 $) |
||||
Fiscal Year |
Domestic |
International |
Overflight |
Total |
2008 |
$8.4 |
$1.9 |
$0.7 |
$11.0 |
2009 |
8.7 |
2.0 |
0.8 |
11.5 |
2010 |
9.0 |
2.1 |
0.8 |
11.9 |
2011 |
9.2 |
2.2 |
0.9 |
12.3 |
2012 |
9.5 |
2.3 |
0.9 |
12.7 |
2013 |
9.9 |
2.4 |
1.0 |
13.3 |
2014 |
10.2 |
2.6 |
1.0 |
13.8 |
2015 |
10.5 |
2.7 |
1.0 |
14.2 |
2016 |
10.8 |
2.8 |
1.1 |
14.7 |
2017 |
$11.2 |
$2.9 |
$1.2 |
$15.3 |
Primary Total |
$97.4 |
$23.9 |
$9.4 |
$130.7 |
Low Total |
$78.0 |
$19.3 |
$7.5 |
$104.8 |
High Total |
$116.9 |
$28.5 |
$11.2 |
$156.6 |
Although not directly regulated and impacted by the rule, travel agencies will be required to request additional information at the time of reservation as a cost of doing business with air carriers. Due to differences in the population, TSA has broken the estimate into two areas: domestic and international passengers.
Domestic Passengers
TSA assumed the time impact for travel agencies to collect full name, date of birth, gender, and, if available, Redress Number are equal to airline reservation call centers: 25 additional seconds per reservation (for discussion, see Sections 1.4.2 and 1.6.3). Furthermore, some online travel agencies will likely need to modify their websites in order to collect additional information.
To calculate compliance costs for traditional agencies, TSA used the same technique discussed in 1.6.3 above to calculate the additional collection time for travel agents. Using the Bureau of Labor Statistics fully loaded wage rate of $20.69 for travel agents, TSA estimated in its primary scenario the cost of data collection at $20.0 million in the first year of implementation of Secure Flight. Table 1.6.4.a shows this impact on travel agents.
Table 1.6.4.a Travel Agency Data Collection Costs, Domestic Passengers |
||||||||
Fiscal Year |
Travel Agent Reservations (millions) |
Total Additional Hours, Primary Scenario |
Total Additional Hours, Low Scenario |
Total Additional Hours, High Scenario |
Travel Agent Hourly Wage |
Total Cost, Primary Scenario (millions) |
Total Cost, Low Scenario (millions) |
Total Cost, High Scenario (millions) |
|
(A) |
(B) |
(C) |
(D) |
(E) |
(B x E) |
(C x E) |
(D x E) |
2008 |
139.5 |
969,000 |
775,000 |
1,163,000 |
$20.69 |
$20.9 |
$16.9 |
25.0 |
2009 |
143.8 |
999,000 |
799,000 |
1,198,000 |
20.69 |
20.7 |
16.5 |
24.8 |
2010 |
148.3 |
1,030,000 |
824,000 |
1,236,000 |
20.69 |
21.3 |
17 |
25.6 |
2011 |
153 |
1,063,000 |
850,000 |
1,275,000 |
20.69 |
22 |
17.6 |
26.4 |
2012 |
157.9 |
1,097,000 |
877,000 |
1,316,000 |
20.69 |
22.7 |
18.1 |
27.2 |
2013 |
162.9 |
1,131,000 |
905,000 |
1,358,000 |
20.69 |
23.4 |
18.7 |
28.1 |
2014 |
168.2 |
1,168,000 |
934,000 |
1,402,000 |
20.69 |
24.2 |
19.3 |
29 |
2015 |
173.6 |
1,206,000 |
964,000 |
1,447,000 |
20.69 |
25 |
19.9 |
29.9 |
2016 |
179.4 |
1,246,000 |
997,000 |
1,495,000 |
20.69 |
25.8 |
20.6 |
30.9 |
2017 |
185.4 |
1,288,000 |
1,030,000 |
1,545,000 |
20.69 |
26.6 |
21.3 |
32 |
Total |
|
|
|
|
|
$232.6 |
$185.9 |
$278.9 |
*Totals in this row include a one-time cost of $0.9 million for the largest online travel agencies tomodify their user interfaces to accommodate the additional data elements. See discussion below. |
||||||||
Travel agents currently collect a great deal of information, including full name, in order to build a profile for their patrons. Accordingly, TSA assumed that a large proportion of travel agencies have enough existing capacity to accommodate the collection of the additional information. According to industry information provided by ASTA, TSA assumed that travel agents do not incur any of the costs associated with reprogramming the booking systems they use. GDSs fund these systems through fees charged to airlines and offer them free of charge to travel agents. As an incentive for travel agencies to use their booking systems, many GDSs offer commission packages to travel agents based on the volume of reservations they process. Based on ASTA information, TSA determined that while the modifications GDSs has to make to their booking systems do not result in any direct costs to travel agents, it may prompt GDSs to raise commission thresholds. TSA deemed this unlikely to affect a large number of travel agents, however, as currently only very large agencies are able to achieve the reservation volumes required to trigger commissions.
As discussed in Section 1.4.2, most travel agencies conduct training through email updates and rely on scripts to guide agents through the reservation process. These scripts are software programs that overlay the core booking system provided by the GDS. These dynamic interfaces prompt the travel agent to provide specific information to the client based on the type of reservation. Travel agents will be required to reprogram these scripts as a consequence of this regulation; however, TSA could not obtain industry estimates on the magnitude of this reprogramming cost. In the absence of such information, TSA was unable to estimate these costs.
While GDSs will make the necessary changes to enable travel agencies to transfer the additional required data elements to the GDS, travel agencies will need to modify their websites to enable users to enter the requested information. TSA anticipates this will be a significant burden only for very large online travel agencies, which have their websites connected to an array of business systems. While TSA was unable to determine the exact number of such travel agencies, TSA solicited information from subject matter experts on the likely cost for these firms to make the necessary front-end changes. The subject matter experts concluded that online travel agencies incur a one-time cost of approximately $125,000 to modify their systems. Based on a web query, TSA estimated this cost impacts 7 major online travel agencies, totaling $875,000. The total is figured into the fiscal year 2008 costs in Table 1.6.4.a.
International Passengers
Under the rule, travel agencies also need to collect additional information from international passengers. TSA used the same method to estimate the costs associated with international travelers as it did for domestic travelers. However, population and timing differences require slightly different discussion and interpretation.
TSA estimated the impact for all international passengers traveling to or from the U.S. This population has been segregated from domestic travelers because while travel agents will be required to request full names, dates of birth, genders, and Redress Numbers from these passengers, this information will not be used for watch list matching until the second phase of Secure Flight implementation. Further, not all of these costs occur within the U.S. economy. For instance, U.S.-based travel agencies may book itineraries on foreign carriers and foreign travel agencies may book itineraries on U.S. carriers. TSA was unable to determine what proportion of the costs occur within the U.S. economy and therefore included all related costs in this analysis, regardless of national economic divisions. The primary estimated cost for travel agencies to collect additional information is $56.6 million over ten years. Table 1.6.4.b presents estimates for each of the ten years, along with low and high estimates.
Table 1.6.4.b Travel Agency Data Collection Costs, International Passengers |
||||||||
Fiscal Year |
Travel Agent Reservations (millions) |
Total Additional Hours, Primary Scenario |
Total Additional Hours, Low Scenario |
Total Additional Hours, High Scenario |
Travel Agent Hourly Wage |
Total Cost, Primary Scenario (millions) |
Total Cost, Low Scenario (millions) |
Total Cost, High Scenario (millions) |
|
(A) |
(B) |
(C) |
(D) |
(E) |
(B x E) |
(C x E) |
(D x E) |
2008 |
31.3 |
218,000 |
174,000 |
261,000 |
$20.69 |
$4.5 |
$3.6 |
$5.4 |
2009 |
32.9 |
228,000 |
183,000 |
274,000 |
20.69 |
4.7 |
3.8 |
5.7 |
2010 |
34.6 |
241,000 |
192,000 |
289,000 |
20.69 |
5.0 |
4.0 |
6.0 |
2011 |
36.2 |
251,000 |
201,000 |
302,000 |
20.69 |
5.2 |
4.1 |
6.3 |
2012 |
38.0 |
264,000 |
211,000 |
317,000 |
20.69 |
5.5 |
4.4 |
6.5 |
2013 |
39.9 |
277,000 |
221,000 |
332,000 |
20.69 |
5.7 |
4.6 |
6.9 |
2014 |
41.9 |
291,000 |
233,000 |
350,000 |
20.69 |
6.0 |
4.8 |
7.3 |
2015 |
44.1 |
306,000 |
245,000 |
368,000 |
20.69 |
6.3 |
5.1 |
7.6 |
2016 |
46.3 |
322,000 |
257,000 |
386,000 |
20.69 |
6.7 |
5.3 |
8.0 |
2017 |
48.6 |
338,000 |
270,000 |
405,000 |
$20.69 |
$7.0 |
$5.6 |
$8.3 |
Total |
|
|
|
|
|
$56.6 |
$45.3 |
$68.0 |
Travel agencies booking overflight itineraries also need to request the same information. Using the method to estimate travel agency costs for travel to and/or from the U.S., TSA has estimated the cost to travel agencies for collecting the additional information at $22.4 million over ten years. Table 1.6.4.c contains the year-specific estimated marginal burden on travel agencies to collect additional information from overflight passengers.
Table 1.6.4.c Travel Agency Data Collection Costs, Overflight Passengers |
||||||||
Fiscal Year |
Travel Agent Reservations (millions) |
Total Additional Hours, Primary Scenario |
Total Additional Hours, Low Scenario |
Total Additional Hours, High Scenario |
Travel Agent Hourly Wage |
Total Cost, Primary Scenario (millions) |
Total Cost, Low Scenario (millions) |
Total Cost, High Scenario (millions) |
|
(A) |
(B) |
(C) |
(D) |
(E) |
(B x E) |
(C x E) |
(D x E) |
2008 |
12.3 |
85,000 |
68,000 |
103,000 |
$20.69 |
$1.8 |
$1.4 |
$2.1 |
2009 |
12.9 |
90,000 |
72,000 |
108,000 |
20.69 |
1.9 |
1.5 |
2.2 |
2010 |
13.6 |
94,000 |
76,000 |
113,000 |
20.69 |
1.9 |
1.6 |
2.3 |
2011 |
14.3 |
99,000 |
79,000 |
119,000 |
20.69 |
2.0 |
1.6 |
2.5 |
2012 |
15.0 |
104,000 |
83,000 |
125,000 |
20.69 |
2.2 |
1.7 |
2.6 |
2013 |
15.7 |
109,000 |
87,000 |
131,000 |
20.69 |
2.3 |
1.8 |
2.7 |
2014 |
16.5 |
115,000 |
92,000 |
138,000 |
20.69 |
2.4 |
1.9 |
2.9 |
2015 |
17.3 |
120,000 |
96,000 |
144,000 |
20.69 |
2.5 |
2.0 |
3.0 |
2016 |
18.2 |
126,000 |
101,000 |
152,000 |
20.69 |
2.6 |
2.1 |
3.1 |
2017 |
19.1 |
133,000 |
106,000 |
159,000 |
$20.69 |
$2.8 |
$2.2 |
$3.3 |
Total |
|
|
|
|
|
$22.4 |
$17.8 |
$26.7 |
Travel Agencies’ Collection Cost Summary
Combined over domestic, international and overflight reservations, travel agencies incur $310.7 million over ten years to collect the additional information at the time of reservation. Table 1.6.4.d shows year-by-year estimates.
Table 1.6.4.d Total Marginal Cost for Travel Agency Data Collections (millions of constant 2005 $) |
||||
Fiscal Year |
Domestic |
International |
Overflight |
Total |
2008 |
$20.0 |
$4.5 |
$1.8 |
$26.3 |
2009 |
20.7 |
4.7 |
1.9 |
27.3 |
2010 |
21.3 |
5.0 |
1.9 |
28.2 |
2011 |
22.0 |
5.2 |
2.0 |
29.2 |
2012 |
22.7 |
5.5 |
2.2 |
30.4 |
2013 |
23.4 |
5.7 |
2.3 |
31.4 |
2014 |
24.2 |
6.0 |
2.4 |
32.6 |
2015 |
25.0 |
6.3 |
2.5 |
33.8 |
2016 |
25.8 |
6.7 |
2.6 |
35.1 |
2017 |
$26.6 |
$7.0 |
$2.8 |
$36.4 |
Primary Total |
$231.7 |
$56.6 |
$22.4 |
$310.7 |
Low Total |
$185.0 |
$45.3 |
$17.8 |
$248.1 |
High Total |
$278.0 |
$68.0 |
$26.7 |
$372.7 |
In the initial year of the Secure Flight program, travel agents will receive training regarding the Secure Flight requirements for data collection and management as part of the reservation making process. These unique training needs would become part of standard training procedures in subsequent years, and in TSA’s view the training component directly related to Secure Flight requirements would be a negligible part of overall training for new travel agents. For this reason, Secure Flight-related training costs are estimated for the first year of the rule period only. Based on a recent survey of the Travel Agency industry34, TSA estimates that there are approximately 110,000 travel agents working in the industry. TSA assumes that annual training requirements for these agents will be one hour, and TSA believes this to be a generous estimate of the time required to explain the Secure Flight data collection requirements to the existing agent population. Table 1.6.4.e reports this travel agent training cost estimate, which, based on the average travel agent hourly wage of $20.69, totals $2.3 million.
Table 1.6.4.e Total Costs of Training for Travel Agencies (millions) |
||||
Fiscal Year |
Employees |
Hourly Rate |
Total Hours (1 per employee) |
Total |
2008 |
110,000 |
$20.69 |
110,000 |
$2.3 |
2009 |
- |
$20.69 |
- |
$0.0 |
2010 |
- |
$20.69 |
- |
$0.0 |
2011 |
- |
$20.69 |
- |
$0.0 |
2012 |
- |
$20.69 |
- |
$0.0 |
2013 |
- |
$20.69 |
- |
$0.0 |
2014 |
- |
$20.69 |
- |
$0.0 |
2015 |
- |
$20.69 |
- |
$0.0 |
2016 |
- |
$20.69 |
- |
$0.0 |
2017 |
- |
$20.69 |
- |
$0.0 |
Primary |
|
|
|
$2.3 |
Low (75%) |
|
|
|
$1.7 |
High (125%) |
|
|
|
$2.8 |
Also in the initial year of the Secure Flight program, travel agencies will incur costs related to reprogramming electronic profiles of clients and other data management functions in order to incorporate the additional data collection requirements into existing business practices. Based on comments from the public received on this issue, TSA used an estimate of $9,000 in reprogramming and related costs for each travel agency affected. It is estimate that these costs will be incurred by the 1,604 travel agency firms with sales above $2 million annually that were in business at the end of 2006. However, in TSA’s view these reprogramming costs do not recur in later years, as the Secure Flight requirements become part of normal business and data collection procedures. Table 1.6.4.f shows this reprogramming cost estimate, which totals $14.4 million.
Table 1.6.4.f Total Costs of Reprogramming Travel Agency Electronic Profiles (millions) |
|||
Fiscal Year |
Agencies |
Cost per Agency |
Total |
2008 |
1,604 |
$9,000 |
$14.4 |
2009 |
- |
$9,000 |
$0.0 |
2010 |
- |
$9,000 |
$0.0 |
2011 |
- |
$9,000 |
$0.0 |
2012 |
- |
$9,000 |
$0.0 |
2013 |
- |
$9,000 |
$0.0 |
2014 |
- |
$9,000 |
$0.0 |
2015 |
- |
$9,000 |
$0.0 |
2016 |
- |
$9,000 |
$0.0 |
2017 |
- |
$9,000 |
$0.0 |
Primary Total |
|
|
$14.4 |
Low (75%) |
|
|
$10.8 |
High (125%) |
|
|
$18.0 |
The government will incur several costs to implement Secure Flight. To meet the requirements of this rule, TSA will have to establish infrastructure enabling it to efficiently screen millions of SFPDs per day, communicate with airlines and the TSC, and verify passenger boarding passes at the checkpoint. TSA also will have to provide the support necessary to maintain and sustain these operations. The following paragraphs describe each of the major cost categories involved in operating and maintaining the Secure Flight system, and estimates of the annual costs to TSA are found in Table 1.6.5.a. As a result of recent Congressional appropriations, TSA has revised its estimate of the 10-year cost to the government to implement and operate the Secure Flight Program. These adjustments result in a $242.8 million reduction in the cost of Secure Flight over 10 years.
TSA also estimated costs for low, high, and primary scenarios associated with verifying boarding passes at checkpoints. Table 1.6.5.i presents the total costs to TSA to operate and maintain the Secure Flight system and to verify boarding passes at checkpoints.
In order for TSA to prepare these costs, it was necessary for the agency to estimate a timeline for Secure Flight implementation. TSA assumed for its budgeting purposes that implementation will stretch over fiscal years 2008 through 2010, after which the program will be at full operating capacity. As discussed elsewhere in this regulatory evaluation, the actual implementation timeline will be contingent on the results of the operational testing phase and future budget allocations. Consequently, the costs presented below reflect TSA’s best estimate of its future costs given available assumptions. TSA’s actual costs may ultimately differ from the projections below.
Following the presentation of TSA’s costs is a brief description of possible costs to the TSC, which are summarized in Table 1.6.5.j. Table 1.6.5.k presents the total potential Federal Government costs.
TSA Costs
Infrastructure
Secure Flight will require TSA to incur costs for the infrastructure of the program at dual sites with failover capability. This category includes lease payments and utilities for facilities used by Secure Flight. TSA has also established an Independent Validation and Verification (IV&V) group, which TSA is using to ensure the quality and integrity of the program. The IV&V group will provide an independent review of critical systems and their development by reviewing preliminary and system designs, witnessing and monitoring testing, facilitating technical issue resolution, and reviewing technical deliverables. The Infrastructure category projects costs for compensation, travel, and training of several full-time government employees who will be maintaining infrastructure or working as part of the IV&V group. Infrastructure costs remain relatively static, with the exception being FY 2010, over the ten year period of the analysis.
Information Technology
In order for TSA to process in a timely and efficient manner the large number of SFPDs airlines will be transmitting, Secure Flight will require significant investment in the information technology components of the system. These costs include the system’s physical hardware and licenses required to operate and maintain the system’s software. Secure Flight also will require extensive development, integration, and testing in order to ensure the speed and accuracy necessary so as not to impact air carrier operations. These development and testing costs will decrease as TSA completes implementation of the system. Costs in this category exhibit increases and decreases corresponding to planned tech refresh cycles as TSA updates the software and hardware used by the Secure Flight system.
Planning, Policy, and Assessment
The Planning, Policy, and Assessment category budgets funds for compensation, travel, and training of several full-time government employees who will be responsible for assessment of the Secure Flight architecture from fiscal years 2008 through 2017. The focus of their efforts will be reviewing the existing system and planning for upgrades to ensure Secure Flight maximizes the security of passenger data and protects passenger privacy.
Design, Development, and Testing
This category includes TSA’s estimated costs to conduct operational testing and bring the Secure Flight system to full-operating capacity. TSA has budgeted costs for compensation, travel, and training for twenty full-time government employees under this category.
Implementation, Operations Planning, and Service Center
TSA will maintain a service center in order to enable ticket agents to provide additional passenger information to TSA. As noted previously, this will occur when a passenger or non-traveling individual’s SFPD does not contain sufficient information for Secure Flight matching analysts to distinguish that person from a record in the watch lists. The service center will be staffed 24-hours a day, 365 days a year at staff levels enabling it to promptly answer all incoming calls. This budget category includes estimated costs for operation of the service center as well as maintenance of facilities and infrastructure.
Data Center Operations
This budget category covers costs for the operation and maintenance of the Secure Flight matching system, including data center operations (for automated watch list matching). Secure Flight will conduct data center operations twenty-four hours a day, seven days a week and will include a backup site to ensure continuous operation. TSA assumed its automated watch list matching workload and associated costs will increase over the ten-year period as the number of enplanements grows.
Examples of operations personnel that will be required include data center operators, system operators, system administrators, and database administrators. These individuals will support the network infrastructure and software programs performing the matching operations, including government oversight of system software maintenance and rollout of newly developed software releases.
Table 1.6.5.a presents the estimated costs to support the Secure Flight system and processes.
Table 1.6.5.a TSA Direct Costs to Operate and Maintain Secure Flight (millions of 2005 $) |
|||||||
Fiscal Year |
Infrastructure |
Information Technology |
Planning, Policy and Assessment |
Design, Development, and Testing |
Implementation, Operations Planning, and Service Center |
Data Center Operations |
TSA Total Costs* |
2008 |
$12.2 |
$4.9 |
$7.8 |
$10.2 |
$11.2 |
$6.5 |
$52.8 |
2009 |
15.7 |
10.9 |
8.5 |
11.7 |
33.5 |
14.0 |
94.3 |
2010 |
20.5 |
14.3 |
8.9 |
11.3 |
30.6 |
14.4 |
100.1 |
2011 |
13.5 |
8.4 |
9.1 |
11.7 |
31.1 |
14.9 |
88.6 |
2012 |
13.9 |
11.2 |
9.4 |
12.0 |
32.1 |
15.3 |
93.9 |
2013 |
14.3 |
10.8 |
9.7 |
12.4 |
34.6 |
15.8 |
97.6 |
2014 |
14.8 |
8.6 |
10.0 |
12.8 |
35.7 |
16.3 |
98.1 |
2015 |
15.3 |
7.5 |
10.4 |
13.2 |
36.8 |
16.8 |
99.8 |
2016 |
15.8 |
9.2 |
10.7 |
13.6 |
37.9 |
17.3 |
104.5 |
2017 |
$16.3 |
$12.3 |
$11.0 |
$14.0 |
$39.1 |
$17.8 |
$110.5 |
Total |
|
|
|
|
|
|
$940.3 |
* Totals may not sum due to rounding. |
|||||||
Verifying Boarding Pass Codes at Checkpoints
TSA is considering the introduction of boarding pass coding to reinforce the integrity of the airline boarding pass and checkpoint identification requirements. Coding can take various formats and provides an efficient means to both encrypt and process information. The most common formats are bar codes (typically acquired by bar code scanners) and alpha-numeric character strings (typically captured by optical character readers). The use of coding is ubiquitous; applications and benefits are already well known to the stakeholders in the air domain, as well as other sectors. For the purpose of the analysis in this section TSA focused on the bar code and the bar code scanner; however, employing an alpha-numeric character string and optical character reader would yield similar results.
While TSA proposed in the NPRM that airlines should have to print a separate code on boarding passes that will contain information provided in the Secure Flight message response for each passenger, the agency has not settled upon a specific means of implementing this requirement at the checkpoints. TSA estimated three possible scenarios by which this may be implemented. In the low scenario, these codes are assumed to be optical character codes which checkpoint personnel will be trained to read. TSA assumed training checkpoint personnel to read these codes will be worked into existing staff briefings and will not result in incremental costs. Thus, costs are discussed below only for the primary and high scenarios. In the primary scenario, TSA assumed handheld scanners will be used to verify a unique and variable algorithm generated by Secure Flight and printed on the boarding pass. In the high scenario, TSA assumed these scanners have a live connection to the Secure Flight system. Under this high scenario, when the Secure Flight code is scanned, the reader will display the ID information and watch list status for that passenger. TSA emphasizes that the bar codes themselves contain no personally identifying passenger information.
Typically, bar code scanning is supported by an integrated set of equipment: the scanner, the recharging cradle, and the central processing unit (CPU) providing communication links, commonly referred to as a server. To estimate the cost of scanning barcodes, TSA calculated the number of each type of inventory needed to support barcode scanning. Screening operations are currently conducted at 805 checkpoints around the country.35 Assuming that each checkpoint has two employees examining boarding passes and identification documents, there is a need for 1,600 scanners available for operations at a given time. Some proportion of scanners will be unavailable for use at any given time, however, because scanner batteries may need to be recharged, some scanners may become damaged or require routine maintenance, etc. TSA estimates that the inventory needs to be 1.5 times the number of scanners that need to be available for use. As a result, checkpoints need an inventory of 2,400 scanners. Each of these scanners will have a dedicated station, or cradle, where the batteries recharge and synchronization with the server will occur, if necessary. Each cradle holds up to 4 scanners.36 A total of 805 cradles could house all the scanners for each checkpoint. Finally, 805 servers will be needed, one for each checkpoint, to interface with the cradles and to facilitate either real-time or periodic synchronization of scanners with the Secure Flight program. Table 1.6.5.b shows the detailed inventory requirements.
Table 1.6.5.b Calculation of Inventory Needed |
||
a |
Screening Checkpoints |
805 |
b |
Average ID Checkers per Checkpoint |
2 |
c |
Scanners in operation (= a * b ) |
1,610 |
d |
Total scanners needed for each in operation |
1.5 |
e |
Scanner inventory needed (= c * d ) |
2,415 |
|
|
|
f |
Scanners per cradle, up to |
4 |
g |
Cradles needed (1 per checkpoint) |
805 |
|
|
|
h |
Cradles per server, up to |
4 |
i |
Servers needed (1 per checkpoint) |
805 |
Assuming that scanners have a life-cycle of 1 year, a total of 2,400 new scanners will need to be purchased every year. At a cost of $708 each, the 10-year cost to purchase scanners is $17.1 million. The cradles will last an average of 2 years. Purchasing a total of 4,428 cradles at $300 each will cost $1.3 million over 10 years. Finally, refreshing servers every 2 years will require the purchase of 4,428 servers over 10 years. At $8,000 each, the purchase of servers will cost $35.4 million. Combined, the 10 year cost for scanners, cradles and servers is $53.9 million. Table 1.6.5.c presents detailed calculations.
|
Scanners |
Cradles |
Servers |
|
|||
Year |
Units purchased (0.75 yr life cycle) |
Cost ($708.33 each) |
Units purchased (2 yr life cycle) |
Cost ($300 each) |
Units purchased (2 yr life cycle) |
Cost ($8000 each) |
Total |
1 |
2,415 |
$1,710,617 |
805 |
$241,500 |
805 |
$6,440,000 |
$8,392,117 |
2 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
3 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
4 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
5 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
6 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
7 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
8 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
9 |
2,415 |
1,710,617 |
403 |
120,750 |
403 |
3,220,000 |
5,051,367 |
10 |
2,415 |
$1,710,617 |
403 |
$120,750 |
403 |
$3,220,000 |
$5,051,367 |
Total |
24,150 |
$17,106,170 |
4,428 |
$1,328,250 |
4,428 |
$35,420,000 |
$53,854,420 |
The primary estimate assumes that scanners perform a “dumb” verification; that is, any information needed for the transaction is already contained in the scanner or the barcode. Typically, this process requires the scanner to read the barcode and verify its legitimacy based on an algorithm stored in the scanner’s software. In this scenario, the scanners need periodic synchronization to ensure that they contain updated encryption information. If synchronization is performed once per day and takes one minute of employee time, synchronizing the 2,400 operating scanners require 14,700 labor hours per year. If the security personnel checking boarding passes and passenger identification perform the synchronization, the total annual cost to synchronize all scanners will be $319,000 based on a $21.73 hourly rate for security personnel.37 Over ten years, the cost will reach $3.2 million. Table 1.6.5.d shows the detailed calculation.
Table 1.6.5.d Cost to Synchronize Scanners |
||
a |
Hours per synchronization |
0.0167 |
b |
Synchs per year per scanner |
365 |
c |
Total operational scanners |
2,415 |
d |
Total Synch hours (= a * b * c ) |
14,691 |
e |
Security personnel wage |
$21.73 |
f |
Total cost to synchronize scanner / year (= d * e ) |
$319,241 |
g |
Ten-year total (= f * 10 ) |
$3,192,409 |
Adding inventory costs to synchronization costs yields a 10-year primary estimate of $57.0 million. Annual detail is in Table 1.6.5.e.
Table 1.6.5.e Cost to Scan Barcodes with Synchronized Scanners, Primary Scenario (Millions) |
|||
Year |
Inventory |
Data |
Total |
1 |
$8.4 |
$0.3 |
$8.7 |
2 |
5.1 |
0.3 |
5.4 |
3 |
5.1 |
0.3 |
5.4 |
4 |
5.1 |
0.3 |
5.4 |
5 |
5.1 |
0.3 |
5.4 |
6 |
5.1 |
0.3 |
5.4 |
7 |
5.1 |
0.3 |
5.4 |
8 |
5.1 |
0.3 |
5.4 |
9 |
5.1 |
0.3 |
5.4 |
10 |
$5.1 |
$0.3 |
$5.4 |
Total |
$53.9 |
$3.2 |
$57.0 |
In the high cost scenario, TSA requires the scanner to query the Secure Flight database with a passenger record locator read from the barcode. Secure Flight then returns information back to the scanner that security staff can use to verify the authenticity of the boarding pass and whether the information on the boarding or gate pass of the person attempting to enter the sterile area matches the information submitted to TSA for watch list matching.38 Because the operational details have yet to be defined, TSA cannot provide an exact estimate of the cost of such an operation. However, other Federal government programs provide query-style data verification. TSA has estimated these costs using the Social Security Administration’s Social Security Online Verification (SSOLV) program as a proxy.39 SSOLV charges $0.03 for each real-time verification. If that fee is representative of their unit transaction cost and that cost is similar for Secure Flight transactions, verifying 8.4 billion boarding passes40 over 10 years will cost an estimated $251.0 million. See Table 1.6.5.f for year-by-year estimates.
Table 1.6.5.f Cost of Real Time Communication (millions) |
||
Year |
Passenger Checks |
Transaction cost ($0.03 each) |
1 |
720.4 |
$21.6 |
2 |
743.4 |
22.3 |
3 |
767.6 |
23.0 |
4 |
792.5 |
23.8 |
5 |
818.8 |
24.6 |
6 |
845.8 |
25.4 |
7 |
874.2 |
26.2 |
8 |
903.6 |
27.1 |
9 |
934.4 |
28.0 |
10 |
966.8 |
$29.0 |
Total |
8,367.7 |
$251.0 |
TSA assessed the impact this additional check might have on checkpoint waiting times. TSA found that a moderate lengthening of the ID verification process likely has no impact on wait times, as checkpoint throughput is presently determined by the time it takes passengers to prepare for screening (remove shoes, laptops, jackets, etc.), pass through the magnetometer, and await the X-ray screening of their carry-on luggage. A draft study of TSA checkpoint processes recently completed by an independent reviewing consortium indicates there is a sufficient difference between the time it takes passengers to proceed through the screening process and the time it takes for document verification to accommodate an increase in the document verification time that ensues under this scenario.
Adding inventory costs to the real-time transaction costs yields the high estimate of $304.9 million over 10 years. Table 1.6.5.g provides the annual detail.
Table 1.6.5.g Cost to Scan Barcodes Against Secure Flight Database in Real Time (Millions) |
|||
Year |
Inventory |
Data |
Total |
1 |
$8.4 |
$21.6 |
$30.0 |
2 |
5.1 |
22.3 |
27.4 |
3 |
5.1 |
23.0 |
28.1 |
4 |
5.1 |
23.8 |
28.8 |
5 |
5.1 |
24.6 |
29.6 |
6 |
5.1 |
25.4 |
30.4 |
7 |
5.1 |
26.2 |
31.3 |
8 |
5.1 |
27.1 |
32.2 |
9 |
5.1 |
28.0 |
33.1 |
10 |
5.1 |
$29.0 |
$34.1 |
Total |
$53.9 |
$251.0 |
$304.9 |
Table 1.6.5.h summarizes the 10-year costs to verify boarding pass information at the checkpoint under the three scenarios.
Table 1.6.5.h Total Costs to Verify Boarding Pass Information |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
2008 |
$8.7 |
$0.0 |
$30.0 |
2009 |
5.4 |
0.0 |
27.4 |
2010 |
5.4 |
0.0 |
28.1 |
2011 |
5.4 |
0.0 |
28.8 |
2012 |
5.4 |
0.0 |
29.6 |
2013 |
5.4 |
0.0 |
30.4 |
2014 |
5.4 |
0.0 |
31.3 |
2015 |
5.4 |
0.0 |
32.2 |
2016 |
5.4 |
0.0 |
33.1 |
2017 |
$5.4 |
$0.0 |
$34.1 |
Total |
$57.0 |
$0.0 |
|
Table 1.6.5.i presents the total direct costs to TSA from the preceding table and table 1.6.5.a.
Table 1.6.5.i Total Direct Costs to TSA |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
2008 |
$61.5 |
$52.8 |
$82.8 |
2009 |
99.7 |
94.3 |
121.6 |
2010 |
105.5 |
100.1 |
128.2 |
2011 |
94.0 |
88.6 |
117.4 |
2012 |
99.3 |
93.9 |
123.6 |
2013 |
103.0 |
97.6 |
128.1 |
2014 |
103.5 |
98.1 |
129.4 |
2015 |
105.2 |
99.8 |
132.0 |
2016 |
109.8 |
104.5 |
137.6 |
2017 |
$115.9 |
$110.5 |
$144.6 |
Total |
$997.3 |
$940.3 |
$1,245.1 |
Terrorist Screening Center (TSC) Costs
In conformity with Homeland Security Presidential Directive 6 (HSPD-6), the Attorney General established the TSC in 2003 as an entity within the Department of Justice (DOJ). The function of the TSC is to centralize and maintain the Federal Government’s terrorism watch lists and to coordinate Federal operations against suspected terrorist individuals when required.
To enable Secure Flight to access appropriate records in the TSDB, the TSC has to make structural modifications to the database. The TSC will make additional infrastructure changes to enable its analysts to receive SFPD information from TSA matching analysts in the case of close matches TSA analysts are unable to resolve. The TSC needs to purchase additional hardware and software to communicate with Secure Flight and process these matching requests. The TSC needs to hire additional technical staff to maintain its IT connection to Secure Flight and additional operational staff to support the anticipated increase in TSC call center volumes related to Secure Flight.
In August of 2005 the Department of Justice, Office of Inspector General released a report examining the direct and indirect costs of the Secure Flight program at the TSC.41 According to the report, the TSC estimated new hardware and software would cost $5,100,000 in fiscal year 2006. The TSC projected IT contracts and reimbursable staff for that year would be $3,527,885, while it placed operational contracts and reimbursable staff at $2,789,984. The report does not break down these cost estimates further. Together, these figures sum to a fiscal year 2006 cost to the TSC of $11,417,869 directly attributable to Secure Flight.
A significant portion of overall TSC costs in the report are for enhancements and infrastructure improvements that are not directly related to Secure Flight. While the TSC did not initiate these modifications in response to Secure Flight’s requirements, the TSC stated the expenses will support all of its activities, including Secure Flight operations. The TSC estimated additional fiscal year 2006 costs of $26,099,699 would be expended indirectly in support of Secure Flight. These expenses included such cost items as leases, building requirements, and office supplies and equipment. DOJ auditors noted in their report that they were unable to reach a conclusion about the accuracy of the financial information the TSC provided them explaining the projected direct and indirect costs of Secure Flight.
Accepting the estimates presented to the DOJ auditors, TSA included the reported figures with its internal program estimates. Table 1.6.5.j divides the TSC’s projected costs of $11,417,869 directly attributable and $26,099,699 indirectly attributable to Secure Flight into separate columns. TSA assumed these costs increase with growth in enplanements in conformity with its internal estimates for infrastructure and intelligence analysis discussed above. Accordingly, consistent with its internal budget estimates, TSA applied a growth rate of 2.1% per year. With this adjustment, estimated costs for fiscal year 2008 came to $11.9 million in direct costs and $27.2 million in indirect costs, for a total of $39.1 million.
Table 1.6.5.j Estimated TSC Costs (millions of 2005 $) |
|||
Fiscal Year |
TSC Direct Costs |
TSC Indirect Costs |
TSC Subtotal |
2008 |
$11.9 |
$27.2 |
$39.1 |
2009 |
12.2 |
27.8 |
39.9 |
2010 |
12.4 |
28.4 |
40.8 |
2011 |
12.7 |
29.0 |
41.6 |
2012 |
12.9 |
29.6 |
42.5 |
2013 |
13.2 |
30.2 |
43.4 |
2014 |
13.5 |
30.8 |
44.3 |
2015 |
13.8 |
31.5 |
45.2 |
2016 |
14.1 |
32.1 |
46.2 |
2017 |
$14.4 |
$32.8 |
$47.2 |
Total |
|
|
$430.2 |
Total Federal Government Costs
Adding the estimated total TSA and TSC costs, fiscal year 2008 costs to the Federal Government for Secure Flight are $100.6 million. Table 1.6.5.k shows the total government costs for fiscal years 2008 through 2017.
Table 1.6.5.k Estimated Total Federal Government Costs (millions of 2005 $) |
|||||||
Fiscal Year |
TSA Subtotal |
TSC Subtotal |
Total Costs |
||||
Primary Scenario |
Low Scenario |
High Scenario |
Primary Scenario |
Low Scenario |
High Scenario |
||
2008 |
$61.5 |
$52.8 |
$82.8 |
$39.1 |
$100.6 |
$91.9 |
$121.9 |
2009 |
99.7 |
94.3 |
121.6 |
$39.9 |
$139.6 |
$134.2 |
$161.6 |
2010 |
105.5 |
100.1 |
128.2 |
$40.8 |
$146.2 |
$140.9 |
$168.9 |
2011 |
94.0 |
88.6 |
117.4 |
$41.6 |
$135.6 |
$130.2 |
$159.0 |
2012 |
99.3 |
93.9 |
123.6 |
$42.5 |
$141.8 |
$136.4 |
$166.1 |
2013 |
103.0 |
97.6 |
128.1 |
$43.4 |
$146.4 |
$141.0 |
$171.5 |
2014 |
103.5 |
98.1 |
129.4 |
$44.3 |
$147.8 |
$142.4 |
$173.7 |
2015 |
105.2 |
99.8 |
132.0 |
$45.2 |
$150.4 |
$145.1 |
$177.2 |
2016 |
109.8 |
104.5 |
137.6 |
$46.2 |
$156.0 |
$150.7 |
$183.7 |
2017 |
$115.9 |
$110.5 |
$144.6 |
$47.2 |
$163.0 |
$157.7 |
$191.7 |
Total |
$997.3 |
$940.3 |
$1,245.1 |
$430.2 |
$1,427.5 |
$1,370.5 |
$1,675.4 |
1.6.6 Opportunity Costs to Travelers
This regulation imposes opportunity costs on all air passengers in the form of additional time required when making reservations. Further, as now, some passengers will experience delays because the information they provide when making a reservation will be insufficient for Secure Flight to clearly distinguish them from a name on a watch list. Some individuals will participate in a redress process when they believed they have been incorrectly delayed or denied boarding as a result of the watch list matching process. Where sufficient data was available, TSA attempted to quantify these additional opportunity costs.
TSA anticipated that all flying passengers will experience an increase in the time needed to make their reservations due to the requirement that airlines request new information from passengers. As discussed in Section 1.4.2, TSA assumed in its primary scenario that travelers making reservations online incur an opportunity cost of 10 seconds, while travelers making telephone or in-person reservations incur an opportunity cost of 20 seconds to provide the additional information airlines and travel agents will be required to collect. These costs are presented in Table 1.6.6.a. TSA did not anticipate the privacy notice impact on travelers making reservations because reservation providers can incorporate the notice into existing privacy notice pages.
For this analysis, passengers have been divided into two categories: domestic and international. TSA was unable to determine the nationality of travelers and their geographic location at the moment they make their reservation. Consequently, some portion of the estimate occurs outside of the U.S. economy.
Domestic Passengers
A 2000 Department of Transportation memorandum “Revised Departmental Guidance: Valuation of Travel Time in Economic Analysis” recommends an average hourly cost of $28.60 for evaluating opportunity costs to air travelers. TSA adopted this estimate for the purposes of this evaluation (column A). Columns B through D calculate the estimated opportunity cost to passengers booking reservations through an airline call center or travel agency. Column B sums the projected 2008 reservations for airline call centers and traditional travel agents from Table 1.4.2.b (58,100,000 + 139,500,000), presenting the total annual reservations placed through a reservation agent. Column C converts the additional 25 seconds per reservation into hours (20 seconds/reservation ÷ 3600 seconds/hour ≈ 0.007 hours/reservation). Multiplying the number of reservations by the hourly value of passenger time and incremental hours per reservation, Column D presents the estimated opportunity costs for passengers booking air travel through a reservation agent.
Columns E through G repeat the process for passengers making reservations via the Internet. As above, the incremental 10 seconds have been converted to hours (10 seconds/reservation ÷ 3600 seconds/hour ≈ 0.003 hours/reservation). Adding the subtotals in Columns D and G, TSA calculated a first-year opportunity cost to passengers of $55.9 million in the primary scenario, and a total ten-year opportunity cost to passengers of $645.6 million.
Table 1.6.6.a Domestic Passenger Reservation Opportunity Costs (Primary Scenario) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
197.6 |
0.007 |
$39.6 |
189.8 |
0.003 |
$16.3 |
$55.9 |
2009 |
28.60 |
203.7 |
0.007 |
40.8 |
195.7 |
0.003 |
16.8 |
57.6 |
2010 |
28.60 |
210.1 |
0.007 |
42.1 |
201.9 |
0.003 |
17.3 |
59.4 |
2011 |
28.60 |
216.7 |
0.007 |
43.4 |
208.2 |
0.003 |
17.9 |
61.3 |
2012 |
28.60 |
223.7 |
0.007 |
44.8 |
214.9 |
0.003 |
18.4 |
63.2 |
2013 |
28.60 |
230.7 |
0.007 |
46.2 |
221.7 |
0.003 |
19.0 |
65.2 |
2014 |
28.60 |
238.2 |
0.007 |
47.7 |
228.9 |
0.003 |
19.6 |
67.3 |
2015 |
28.60 |
246.0 |
0.007 |
49.2 |
236.3 |
0.003 |
20.3 |
69.5 |
2016 |
28.60 |
254.1 |
0.007 |
50.9 |
244.2 |
0.003 |
21.0 |
71.9 |
2017 |
$28.60 |
262.7 |
0.007 |
$52.6 |
252.4 |
0.003 |
$21.7 |
$74.3 |
Total |
|
|
|
$457.3 |
|
|
$188.3 |
$645.6 |
Table 1.6.6.b duplicates the calculations in Table 1.6.6.a for the low scenario. Accordingly, the opportunity costs for passengers booking online are unchanged. As discussed in Section 1.4.2, however, in this scenario TSA assumed reservations agents will be able to collect the requested information from passengers in 20 seconds.
Table 1.6.6.b Domestic Passenger Reservation Opportunity Costs (Low Scenario) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
197.6 |
0.006 |
$33.9 |
189.8 |
0.003 |
$16.3 |
$50.2 |
2009 |
28.60 |
203.7 |
0.006 |
34.9 |
195.7 |
0.003 |
16.8 |
51.7 |
2010 |
28.60 |
210.1 |
0.006 |
36.1 |
201.9 |
0.003 |
17.3 |
53.4 |
2011 |
28.60 |
216.7 |
0.006 |
37.2 |
208.2 |
0.003 |
17.9 |
55.1 |
2012 |
28.60 |
223.7 |
0.006 |
38.4 |
214.9 |
0.003 |
18.4 |
56.8 |
2013 |
28.60 |
230.7 |
0.006 |
39.6 |
221.7 |
0.003 |
19.0 |
58.6 |
2014 |
28.60 |
238.2 |
0.006 |
40.9 |
228.9 |
0.003 |
19.6 |
60.5 |
2015 |
28.60 |
246.0 |
0.006 |
42.2 |
236.3 |
0.003 |
20.3 |
62.5 |
2016 |
28.60 |
254.1 |
0.006 |
43.6 |
244.2 |
0.003 |
21.0 |
64.6 |
2017 |
$28.60 |
262.7 |
0.006 |
$45 |
252.4 |
0.003 |
$21.7 |
$66.8 |
Total |
|
|
|
$392 |
|
|
$188.3 |
$580.2 |
Finally, Table 1.6.6.c presents estimated passenger opportunity costs under the high scenario. Again, opportunity costs associated with Internet reservations remain unchanged. In this case, however, TSA assumed 30 seconds to be necessary to collect the requested passenger information.
Table 1.6.6.c Passenger Reservation Opportunity Costs, Domestic Passengers (High Scenario) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
197.6 |
0.008 |
$45.2 |
189.8 |
0.003 |
$16.3 |
$61.5 |
2009 |
28.60 |
203.7 |
0.008 |
46.6 |
195.7 |
0.003 |
16.8 |
63.4 |
2010 |
28.60 |
210.1 |
0.008 |
48.1 |
201.9 |
0.003 |
17.3 |
65.4 |
2011 |
28.60 |
216.7 |
0.008 |
49.6 |
208.2 |
0.003 |
17.9 |
67.5 |
2012 |
28.60 |
223.7 |
0.008 |
51.2 |
214.9 |
0.003 |
18.4 |
69.6 |
2013 |
28.60 |
230.7 |
0.008 |
52.8 |
221.7 |
0.003 |
19.0 |
71.8 |
2014 |
28.60 |
238.2 |
0.008 |
54.5 |
228.9 |
0.003 |
19.6 |
74.1 |
2015 |
28.60 |
246.0 |
0.008 |
56.3 |
236.3 |
0.003 |
20.3 |
76.6 |
2016 |
28.60 |
254.1 |
0.008 |
58.1 |
244.2 |
0.003 |
21.0 |
79.1 |
2017 |
$28.60 |
262.7 |
0.008 |
$60.1 |
252.4 |
0.003 |
$21.7 |
$81.8 |
Total |
|
|
|
$522.5 |
|
|
$188.3 |
$710.8 |
Table 1.6.6.d. compiles the total reservations opportunity cost from each scenario for domestic passengers.
Table 1.6.6.d Total Domestic Passenger Opportunity Costs, Groups 1 - 3 (millions of 2005 $) |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
2008 |
$55.9 |
$50.2 |
$61.5 |
2009 |
57.6 |
51.7 |
63.4 |
2010 |
59.4 |
53.4 |
65.4 |
2011 |
61.3 |
55.1 |
67.5 |
2012 |
63.2 |
56.8 |
69.6 |
2013 |
65.2 |
58.6 |
71.8 |
2014 |
67.3 |
60.5 |
74.1 |
2015 |
69.5 |
62.5 |
76.6 |
2016 |
71.9 |
64.6 |
79.1 |
2017 |
$74.3 |
$66.8 |
$81.8 |
Total |
$645.6 |
$580.2 |
$710.8 |
As discussed previously in Section 1.6.3, carriers in Group 4 will likely transmit passenger information to Secure Flight through a web interface. 42 Passengers making reservations through Group 4 carriers may experience different opportunity costs from the passengers described above because Group 4 carriers collect passenger information in a variety of manners. TSA did not have baseline information on either the reservations process used by each of these carriers, including the distribution of reservations between available methods, or the number of reservations handled that is needed to formulate a reliable opportunity cost estimate. Further, as the Secure Flight web application had not been developed at the time of writing, TSA could not say with certainty what impact the transition to this system will have on the reservation processes for these carriers and their passengers. As a result, TSA calculated passenger opportunity costs for Group 4 reservations by estimating the cost if all passengers are able to provide the information in 25 seconds (primary scenario), 20 seconds (low scenario), or 30 seconds (high scenario). Table 1.6.6.e presents the results of these assumptions.
Table 1.6.6.e Total Domestic Passenger Opportunity Costs, Group 4 (millions of 2005 $) |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
1 |
$0.5 |
$0.4 |
$0.6 |
2 |
0.5 |
0.4 |
0.6 |
3 |
0.5 |
0.4 |
0.6 |
4 |
0.5 |
0.4 |
0.6 |
5 |
0.5 |
0.4 |
0.6 |
6 |
0.6 |
0.4 |
0.7 |
7 |
0.6 |
0.4 |
0.7 |
8 |
0.6 |
0.5 |
0.7 |
9 |
0.6 |
0.5 |
0.7 |
10 |
$0.6 |
$0.5 |
$0.7 |
Total |
$5.4 |
$4.3 |
$6.5 |
Table 1.6.6.f thus presents total domestic passenger opportunity costs.
Table 1.6.6.f Total Domestic Passenger Opportunity Costs (millions of 2005 $) |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
1 |
$56.4 |
$50.6 |
$62.1 |
2 |
58.1 |
52.1 |
64.0 |
3 |
59.9 |
53.8 |
66.0 |
4 |
61.8 |
55.5 |
68.1 |
5 |
63.7 |
57.2 |
70.2 |
6 |
65.8 |
59.0 |
72.5 |
7 |
67.9 |
60.9 |
74.8 |
8 |
70.1 |
63.0 |
77.3 |
9 |
72.5 |
65.1 |
79.8 |
10 |
$74.9 |
$67.3 |
$82.5 |
Total |
$651.0 |
$584.5 |
$717.3 |
The rule requires those passengers whom TSA cannot rule out as a possible match to a name on the TSC’s Selectee or No Fly Lists to provide additional identifying information at the ticket counter. Persons identified as potential matches to the Selectee list by the automated system are required to provide additional information. TSA anticipated two principal situations requiring the additional data.
TSA will screen those passengers based upon the available information, but if the information is insufficient to distinguish them from a name on the Selectee or No Fly List, they are required to provide the information again at the ticket counter or self-serve kiosk that is capable of determining that the identification is a valid verifying identity document (VID), authenticating the VID, and reading and transmitting passenger information from the VID before being allowed to access the sterile area. The ticket agent will communicate additional passenger information to TSA matching analysts to facilitate adjudication of the possible match. The passenger will not be allowed to receive his or her boarding pass until TSA returns a final decision on the passenger’s status. In the ideal case where this additional information immediately clears the passenger, TSA estimated this process will take only a matter of seconds.
In a second scenario, a small percent of passengers who provide all requested information when making reservations will also encounter a delay at the ticket counter. This might occur because the information provided is insufficient to distinguish the traveler from a record in the Selectee or No Fly List. These passengers are required to check-in with a ticket agent at the airport and provide additional identifying information. As in the previous scenario, the ticket agent will then communicate this information to Secure Flight. Since these passengers have already provided the requested information, however, receiving a final decision may take longer and could vary considerably from person to person.
At the time of writing, TSA was unable to evaluate the net opportunity cost to travelers required to submit additional information at the ticket counter. Airlines do not keep a record of either the number of passengers currently required to present additional information at the ticket counter for watch list purposes or the time it takes to clear those passengers. Without sufficient baseline information, TSA was unable to estimate whether this will impact the number of passengers stopped at the ticket counter.
Once Secure Flight becomes fully operational and takes over matching from the airlines, the number of passengers required to be stopped at the ticket counter should be reduced. As TSA develops a list of individuals who have been previously distinguished from persons on the watch lists and more and more passengers provide their Redress Numbers during the reservation process, the improved matching should reduce the percentage of passengers who are required to provide additional information at the ticket counter, particularly over the first three years of implementation.
A further unknown was the net change in the time required to clear passengers. As already mentioned, airlines do not keep statistics on the time required to clear passengers. Airlines currently have the discretion to make such decisions with on-site personnel, as in the case of the Ground Security Coordinators. Secure Flight requires them to await a response from the automated system or Secure Flight intelligence analysts. TSA had no estimates of how long this process might take.
Finally, the rule allows passengers to file for redress when they believe they have been delayed or denied boarding as a result of the watch list matching process. TSA estimated a one hour opportunity cost to passengers to submit redress paperwork. This estimate includes the time to fill out the redress form and to collect the required supporting documents.
Passengers will submit their redress information through DHS’ Traveler Redress Inquiry Program. TSA assumed redress submissions will increase initially due to publicity and passengers seeking to acquire a Redress Number when the Agency announces full implementation of Secure Flight. As the list of cleared passengers grows and passengers begin to submit their Redress Number to avoid delays associated with watch list matching, the number of redress submissions should decline.
As already discussed, based on the numerous criteria that must be met before Secure Flight can become fully operational, TSA was unable to estimate when the described effects will take place. Further, TSA was unable to quantify the magnitude of the potential reduction in redress submissions.
International Passengers
Population and timing differences between domestic and international passengers require slightly different discussion and interpretation. While covered air carriers are required to request full names, dates of birth, genders, and redress numbers from international passengers beginning shortly after the effective date of the rule, Secure Flight will not perform watch list matching for this population until the second phase of Secure Flight implementation. Further, not all of these costs occur within the U.S. economy. For instance, a foreign national may make a reservation while on foreign soil. This transaction does not occur within the U.S. economy. U.S. citizens’ transactions on U.S. soil do occur within the U.S. economy. There is a gray area in-between that relies heavily on how activities are attributed to economies. They can either be attributed by geography (akin to Gross Domestic Product) or by nationality of the economic actor (akin to Gross National Product). TSA was unable to determine either geography at time of reservation or nationality of international passengers. Accordingly, all opportunity costs to individuals resulting from the rule are in this analysis, regardless of national economic divisions.
Passengers flying to and from the U.S. will spend increased time to provide the additional information for their reservations. TSA has used the same method to estimate international passenger opportunity costs as it used for domestic passengers. Accordingly, the primary ten-year marginal opportunity cost to individuals is $157.6 million. Table 1.6.6.g presents the annual estimates.
Table 1.6.6.g Passenger Reservation Opportunity Costs, International Passengers (Primary) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
44.3 |
0.007 |
$8.9 |
42.6 |
0.003 |
$3.7 |
$12.6 |
2009 |
28.60 |
46.5 |
0.007 |
9.3 |
44.7 |
0.003 |
3.8 |
13.1 |
2010 |
28.60 |
48.9 |
0.007 |
9.7 |
47.0 |
0.003 |
4.0 |
13.7 |
2011 |
28.60 |
51.4 |
0.007 |
10.3 |
49.3 |
0.003 |
4.2 |
14.5 |
2012 |
28.60 |
53.9 |
0.007 |
10.8 |
51.8 |
0.003 |
4.5 |
15.3 |
2013 |
28.60 |
56.5 |
0.007 |
11.3 |
54.3 |
0.003 |
4.7 |
16.0 |
2014 |
28.60 |
59.5 |
0.007 |
11.9 |
57.1 |
0.003 |
4.9 |
16.8 |
2015 |
28.60 |
62.4 |
0.007 |
12.5 |
60.0 |
0.003 |
5.1 |
17.6 |
2016 |
28.60 |
65.5 |
0.007 |
13.1 |
63.0 |
0.003 |
5.4 |
18.5 |
2017 |
$28.60 |
68.8 |
0.007 |
$13.8 |
66.1 |
0.003 |
$5.7 |
$19.5 |
Total |
|
|
|
$111.6 |
|
|
$46.0 |
$157.6 |
Table 1.6.6.h duplicates the calculations in Table 1.6.6.b for the low scenario. Accordingly, the opportunity costs for passengers booking online are unchanged. As discussed in Section 1.4.2, however, in this scenario TSA assumed reservations agents are able to collect the requested information from passengers in 20 seconds.
Table 1.6.6.h Passenger Reservation Opportunity Costs, International Passengers (Low Scenario) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
44.3 |
0.006 |
$7.6 |
42.6 |
0.003 |
$3.7 |
$11.3 |
2009 |
28.60 |
46.5 |
0.006 |
7.9 |
44.7 |
0.003 |
3.8 |
11.7 |
2010 |
28.60 |
48.9 |
0.006 |
8.3 |
47.0 |
0.003 |
4.0 |
12.3 |
2011 |
28.60 |
51.4 |
0.006 |
8.8 |
49.3 |
0.003 |
4.2 |
13.0 |
2012 |
28.60 |
53.9 |
0.006 |
9.3 |
51.8 |
0.003 |
4.5 |
13.8 |
2013 |
28.60 |
56.5 |
0.006 |
9.7 |
54.3 |
0.003 |
4.7 |
14.4 |
2014 |
28.60 |
59.5 |
0.006 |
10.2 |
57.1 |
0.003 |
4.9 |
15.1 |
2015 |
28.60 |
62.4 |
0.006 |
10.7 |
60.0 |
0.003 |
5.1 |
15.8 |
2016 |
28.60 |
65.5 |
0.006 |
11.2 |
63.0 |
0.003 |
5.4 |
16.6 |
2017 |
$28.60 |
68.8 |
0.006 |
$11.8 |
66.1 |
0.003 |
$5.7 |
$17.5 |
Total |
|
|
|
$95.5 |
|
|
$46.0 |
$141.5 |
Table 1.6.6.i presents estimated passenger opportunity costs under the high scenario. Again, opportunity costs associated with Internet reservations remain unchanged. In this case, however, TSA assumed 30 seconds are necessary to collect the requested passenger information.
Table 1.6.6.i Passenger Reservation Opportunity Costs, International Passengers (High Scenario) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
44.3 |
0.008 |
$10.1 |
42.6 |
0.003 |
$3.7 |
$13.8 |
2009 |
28.60 |
46.5 |
0.008 |
10.7 |
44.7 |
0.003 |
3.8 |
14.5 |
2010 |
28.60 |
48.9 |
0.008 |
11.2 |
47.0 |
0.003 |
4.0 |
15.2 |
2011 |
28.60 |
51.4 |
0.008 |
11.7 |
49.3 |
0.003 |
4.2 |
15.9 |
2012 |
28.60 |
53.9 |
0.008 |
12.3 |
51.8 |
0.003 |
4.5 |
16.8 |
2013 |
28.60 |
56.5 |
0.008 |
12.9 |
54.3 |
0.003 |
4.7 |
17.6 |
2014 |
28.60 |
59.5 |
0.008 |
13.6 |
57.1 |
0.003 |
4.9 |
18.5 |
2015 |
28.60 |
62.4 |
0.008 |
14.3 |
60.0 |
0.003 |
5.1 |
19.4 |
2016 |
28.60 |
65.5 |
0.008 |
15.0 |
63.0 |
0.003 |
5.4 |
20.4 |
2017 |
$28.60 |
68.8 |
0.008 |
$15.8 |
66.1 |
0.003 |
$5.7 |
$21.5 |
Total |
|
|
|
$127.6 |
|
|
$46.0 |
$173.6 |
Finally, Table 1.6.6.j presents the primary estimate of opportunity costs for over-flight passengers to provide additional information when they make their reservation. Because nearly all of these involve foreign nationals on foreign soil, these are not direct costs to the U.S. economy. The ten-year total estimate of opportunity costs for over-flight passengers was estimated at $62.0 million. The opportunity cost to these passengers under the low scenario was estimated to be $55.5 million and $68.1 million under the high scenario.
Table 1.6.6.j Passenger Reservation Opportunity Costs, Over-Flights (Primary Scenario) |
||||||||
Fiscal Year |
Hourly Value of Pass. Time |
Number of Offline Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Offline Opportunity Costs (millions) |
Number of Internet Bookings (millions) |
Additional Time per Booking (Hours) |
Subtotal Internet Opportunity Costs (millions) |
Total Booking Opportunity Cost (millions) |
|
(A) |
(B) |
(C) |
(D) = A x B x C |
(E) |
(F) |
(G)
= |
(H) = D + G |
2008 |
$28.60 |
17.5 |
0.007 |
$3.5 |
16.8 |
0.003 |
$1.4 |
$4.9 |
2009 |
28.60 |
18.3 |
0.007 |
3.7 |
17.6 |
0.003 |
1.5 |
5.2 |
2010 |
28.60 |
19.3 |
0.007 |
3.9 |
18.5 |
0.003 |
1.6 |
5.5 |
2011 |
28.60 |
20.2 |
0.007 |
4.0 |
19.4 |
0.003 |
1.7 |
5.7 |
2012 |
28.60 |
21.2 |
0.007 |
4.3 |
20.4 |
0.003 |
1.7 |
6.0 |
2013 |
28.60 |
22.3 |
0.007 |
4.5 |
21.4 |
0.003 |
1.8 |
6.3 |
2014 |
28.60 |
23.4 |
0.007 |
4.7 |
22.5 |
0.003 |
1.9 |
6.6 |
2015 |
28.60 |
24.6 |
0.007 |
4.9 |
23.6 |
0.003 |
2.0 |
6.9 |
2016 |
28.60 |
25.8 |
0.007 |
5.2 |
24.8 |
0.003 |
2.1 |
7.3 |
2017 |
$28.60 |
27.1 |
0.007 |
$5.4 |
26.0 |
0.003 |
$2.2 |
$7.6 |
Total |
|
|
|
$44.1 |
|
|
$17.9 |
$62.0 |
In addition to these passenger opportunity costs for reservations made with large international carriers, TSA has included a rough estimate of the passenger opportunity costs that may be experienced by passengers on small foreign carriers. Similar to the calculations presented above for domestic Group 4 carriers, TSA has based these estimates on an assumption that it takes all passengers 25 seconds (primary scenario), 20 seconds (low scenario), or 30 seconds (high scenario) to provide the requested passenger information at the time of reservation. Table 1.6.6.k presents the results.
Table 1.6.6.k Small Foreign Carrier Passenger Opportunity Costs (millions of 2005 $) |
|||
Fiscal Year |
Primary Scenario |
Low Scenario |
High Scenario |
1 |
$0.6 |
$0.5 |
$0.7 |
2 |
0.6 |
0.5 |
0.7 |
3 |
0.6 |
0.5 |
0.8 |
4 |
0.7 |
0.5 |
0.8 |
5 |
0.7 |
0.6 |
0.8 |
6 |
0.7 |
0.6 |
0.9 |
7 |
0.8 |
0.6 |
0.9 |
8 |
0.8 |
0.7 |
1.0 |
9 |
0.9 |
0.7 |
1.0 |
10 |
$0.9 |
$0.7 |
$1.1 |
Total |
$7.3 |
$5.8 |
$8.7 |
Passenger Opportunity Cost Summary
Combined, passengers incur $877.9 million in opportunity costs to provide additional information at the time of reservation. Table 1.6.6.l presents the year-by-year primary estimates for passenger opportunity costs.
Table 1.6.6.l Total Marginal Opportunity Cost for Passengers (millions) |
||||
Fiscal Year |
Domestic* |
International* |
Over-Flight |
Total |
2008 |
$56.4 |
$13.2 |
$4.9 |
$74.5 |
2009 |
$58.1 |
$13.7 |
5.2 |
77.0 |
2010 |
$59.9 |
$14.3 |
5.5 |
79.7 |
2011 |
$61.8 |
$15.2 |
5.7 |
82.7 |
2012 |
$63.7 |
$16.0 |
6.0 |
85.7 |
2013 |
$65.8 |
$16.7 |
6.3 |
88.8 |
2014 |
$67.9 |
$17.6 |
6.6 |
92.0 |
2015 |
$70.1 |
$18.4 |
6.9 |
95.4 |
2016 |
$72.5 |
$19.4 |
7.3 |
99.1 |
2017 |
$74.9 |
$20.4 |
$7.6 |
$102.9 |
Primary Total |
$651.0 |
$164.9 |
$62.0 |
$877.9 |
Low Total |
$584.5 |
$147.3 |
$55.5 |
$787.3 |
High Total |
$717.3 |
$182.3 |
$68.1 |
$967.7 |
* These totals include both large and small carrier estimates. |
||||
Passenger opportunity costs imposed by Secure Flight requirements or procedures might also come about from the occasional need for passengers whose boarding passes were inhibited due to a match with the watch list and who were consequently unable to board their scheduled flight. Such passengers would have to be rebooked by their airline, incurring the loss of valuable time as they worked with their airline’s customary customer service procedures to complete their interrupted travel itinerary. Concerns about such opportunity costs were raised in some public comments to the Secure Flight NPRM. In TSA’s view, the effect of Secure Flight will be to improve the system-wide passenger clearing process, not reduce its effectiveness. Further, any costs that may be imposed by Secure Flight should be measured as an increment from today’s baseline, which itself already includes these types of consequential but infrequent disruptions to travel plans.
TSA is confident that Secure Flight will reduce rather than increase delays, and for this reason it is not including an estimate of these opportunity costs as part of the cost estimate for the rule. However, Secure Flight is a complex system of information management and communication, and such systems are inherently subject to risk of periodic failure, and TSA believes that it is necessary to provide some accounting for this risk. To provide a frame of reference for such potential opportunity costs, TSA examined the time costs associated with all security related delays in the current system. Analysis of data from the Bureau of Transportation Statistics on commercial airline delay factors, TSA estimated that in Fiscal Year 2007, U.S. airlines experienced 1.4 seconds of security related delay per domestic enplaned passenger delay. Table 1.6.6.m extends this per passenger delay estimate to annual domestic enplanements, and calculates the value of this delay impact of security using the Department of Transportation’s value of passenger of time, $28.60. While the risk and persistence of system outages and disruptions related to system complexity are not known, TSA believes that an annual doubling of per passenger security related delay provides a conservative proxy for this potential cost to users of the air transportation system. Because the estimated 10 year undiscounted value of $88.5 million is regarded as providing a frame of reference for this risk, the value is used for the primary, low and high estimate of this opportunity cost component.
Table 1.6.6.m Passenger Opportunity Costs of Secure Flight Complexity Risks |
|||
Fiscal Year |
Annual Domestic Enplanements |
Security-Related Delay (1.4 seconds), in hours |
Opportunity Cost of Passenger Time (@$28.60/hr) |
2008 |
677,500,000 |
263,472.2 |
$7,535,306 |
2009 |
698,300,000 |
271,561.1 |
$7,766,648 |
2010 |
720,300,000 |
280,116.7 |
$8,011,337 |
2011 |
742,800,000 |
288,866.7 |
$8,261,587 |
2012 |
766,600,000 |
298,122.2 |
$8,526,296 |
2013 |
791,000,000 |
307,611.1 |
$8,797,678 |
2014 |
816,700,000 |
317,605.6 |
$9,083,519 |
2015 |
843,200,000 |
327,911.1 |
$9,378,258 |
2016 |
871,000,000 |
338,722.2 |
$9,687,456 |
2017 |
900,200,000 |
350,077.8 |
$10,012,224 |
Total |
7,827,600,000 |
3,044,067 |
$87,060,307 |
Section 7: Sensitivity Analysis
All analysis is subject to uncertainty. This section of the regulatory evaluation identifies the principle sources of uncertainty in the economic analysis and illustrates their influence on the total estimated costs of the rule. As one of TSA’s scenarios assumes coordination of the APIS and Secure Flight transition among international operators, some of the sensitivity analyses performed for the APIS pre-departure final rule are also relevant to this analysis. For example, CBP analyzed the impact on flight delays and passenger opportunity cost of a batch mode (which the airlines would run if they chose to delay their AQQ transition in anticipation of the Secure Flight requirements becoming operational) versus adoption of the AQQ approach. TSA has not reproduced these sensitivity analyses here, but encourages the reader to review the regulatory impact assessment accompanying the APIS pre-departure final rule.
With respect to Secure Flight, TSA estimates that there are three important sources of cost uncertainty as presented in the regulatory evaluation. These are discussed below, in the following order: (1) the average time required to collect Secure Flight data elements from passengers during telephone reservation sessions; (2) the number of airline reservations made annually; and (3) the distribution of airline reservations originating from internet, travel agency and airline call center sources. This section of the evaluation assesses each of these uncertainty factors by evaluating how changes in their values affect the overall cost estimate and major subelements of the cost analysis.
Section 1.7.1 Airline Reservation Time Estimates
Under the rule, airline passenger reservation agents and travel agents collect additional information from passengers at the time of flight reservation on behalf of the air carriers. TSA assumed that collecting additional information from passengers increases the amount of time to book a reservation, causing airlines to incur additional costs. Additionally, this requirement also imposes an opportunity cost on passengers making reservations.
In the primary cost estimate, TSA assumed that travel agents and airline passenger reservation agents, as well as passengers, need an additional 25 seconds to book a reservation. In its cost estimates, TSA considers a range of 20 to 30 seconds in its low and high scenarios, 25% above and below the primary estimate, respectively. A 25% decrease in this estimate (to 20 seconds) yields a 4.52% reduction in the total cost of the rule, while a 25% increase (to 30 seconds) yields an 4.5% increase in the total estimated cost. Given these considerations, the total cost estimate is somewhat sensitive to the estimated increase in reservation times.
Section 1.7.2 Domestic Reservations
To calculate the total cost of the Secure Flight rule, TSA estimated the number of domestic reservations, which served as an input to several other cost calculations. In the primary cost estimate, the number of estimated domestic reservations over the ten year period of analysis is 4.5 billion, increasing from 387.4 million in 2008 to 515 million in 2017, a total increase of about 34%. Increases from year to year are based on FAA forecasts for domestic enplanements, and average slightly over 3% each year. If those annual growth rates for reservations are increased by 25%, so that passenger activity grows at a faster rate than the most recent FAA forecasts, then from 2008 to 2017 domestic enplanements increase about 42%, and the total estimated cost of the rule increases by almost 1%. If the annual growth of domestic enplanements slows from forecast rates by about 25%, then from 2008 to 2017 domestic enplanements increase about 24%, and the estimate cost of the rule falls about 1% compared to the baseline case. The overall cost estimate is therefore not strongly sensitive to changes in the future course for the number of domestic reservations.
Section 1.7.3 Changes in the Distribution of Reservation Methods
Currently, approximately 49% of reservations are made over the internet, with the remaining 51% divided between travel agent reservations (in person or over the telephone) with 36% and airline reservation call centers, with 15%. In the analysis of the rule’s cost impacts, this distribution was assumed to hold over the period of analysis. However, while trends have been toward greater use of internet reservation channels, the future is uncertain, and the future course of reservation choices by passengers will affect the ultimate cost of the Secure Flight rule.
To estimate the sensitivity of the rule’s costs to this distribution, two cases were examined. First, it was assumed that the internet share of reservation making grew steadily from 49% in 2008 to 69% in 2017, with the remaining reservations split as before between travel agent reservations and airline call center reservations (that is, a split of the remainder by about 70% to travel agents and 30% to airline call centers). Such a growth pattern reduces the cost of the rule by approximately 4.2%, due to reduced costs devoted by call centers and passengers to data collection efforts.
Second, it was assumed that the internet’s growing share reverses itself from 49% in 2008 to 44% in 2017, with the remaining reservations split as before between travel agent reservations and airline call center reservations (that is, a split of the remainder by about 70% to travel agents and 30% to airline call centers). Such a distribution pattern increases the cost of the rule by approximately 1, due to increased costs from data collection efforts at call centers and for passengers.
Section 1.7.4 Sensitivity Analysis Summary
As shown in the Table 1.7.4.a below, the total cost estimate is most sensitive to the modeled change in the average airline and travel agent reservation time requirement. This is primarily due to the large number of reservations forecast over the ten year period of analysis. As noted in the table, changes to other variables did not exert as large of an impact on the total cost estimate.
Table 1.7.4.a Summary of Sensitivity Analysis Results (Millions of $) |
|||
Sensitivity Test and Cost Elements |
Baseline |
Sensitivity Bound |
Sensitivity Bound |
5 second increase and Decrease in Reservation Data Collection Time |
25 seconds |
30 seconds |
20 seconds |
Total Cost |
$3,965.1 |
$4,142.8 |
$3,786.0 |
Cash Outlay Cost |
$3,000.1 |
$3,088.0 |
$2,911.6 |
Airline Collection Cost |
$130.7 |
$156.6 |
$104.8 |
Travel Agent Collection Cost |
$310.7 |
$372.7 |
$248.1 |
Passenger Opportunity Cost |
$965.0 |
$1,054.8 |
$874.4 |
Change in Growth of Annual Domestic Reservations |
|
Increase growth 25%/yr |
Decrease growth 25%/yr |
Total Cost |
$3,965.1 |
$4,001.7 |
$3,929.9 |
Cash Outlay Cost |
$3,000.1 |
$3,012.3 |
$2,988.0 |
Airline Collection Cost |
$130.7 |
$134.4 |
$127.1 |
Travel Agent Collection Cost |
$310.7 |
$319.2 |
$302.2 |
Passenger Opportunity Cost |
$965.0 |
$989.4 |
$941.9 |
Change in Distribution of Reservation Methods |
|
More internet reservations |
Fewer internet reservations |
Total Cost |
$3,965.1 |
$3,799.0 |
$4,005.6 |
Cash Outlay Cost |
$3,000.1 |
$2,907.5 |
$3,022.9 |
Airline Collection Cost |
$130.7 |
$103.2 |
$137.3 |
Travel Agent Collection Cost |
$310.7 |
$245.6 |
$326.9 |
Passenger Opportunity Cost |
$965.0 |
$891.5 |
$982.7 |
Section 8: Comparison of Costs and Benefits of Regulatory Alternatives
EO 12866 requires Federal agencies to consider and analyze alternatives to rulemakings to ensure that a rule is the most cost-effective option that still meets agency objectives and legal mandates.
Some of the key agency objectives and legal mandates include:
The government must assume the performance of comparing passenger information to the automatic Selectee and No Fly lists;
Reduce the number of false positive selectees;
Standardize watch list matching methods; and,
Centralize watch list matching in order to limit distribution of the watch lists.
TSA considered a range of alternatives and quantitatively evaluated several of the most likely options. These alternatives pertain to the domestic portion of the Secure Flight rule. A qualitative analysis accompanies other alternatives considered but not quantitatively analyzed. Table 1.8.1.a presents a comparison of the qualitative alternatives; Table 1.8.2.a presents a comparison of the quantitative alternatives.
Section 1.8.1 qualitatively considers the following possible regulatory actions:
No Action: Individual air carriers compare domestic passenger information to watch lists provided by TSA. Airlines continue to pre-screen passengers using systems and methods already in place. There are no additional costs and benefits associated with this alternative and this option does not meet statutory mandates. Because this alternative is the status quo, discussed in earlier sections, and has no additional costs or benefits, it is not analyzed further.
Air carriers directly implement Federally-regulated watch list screening standards.
TSA replaces its existing watch list matching IT infrastructure and leverages use of the U.S. Custom and Border Protection’s Automated Targeting System (ATS) or APIS Quick Query (AQQ) in the domestic environment.
Preferred Alternative: Airlines request standardized passenger information at time of reservation and transmit to TSA for comparison to the Federal Government’s watch lists.
The following alternatives are fundamentally similar to Alternative #4 but include modifications in data, operational, and/or implementation requirements. Section 1.8.2 quantitatively compares these alternatives.
TSA utilizes additional SFPD attributes for watch list matching. In addition to full name, date of birth, gender, and Redress Number, TSA requires aircraft operators to request home address and home phone number from passengers and non-traveling individuals.
TSA requires airlines to give, on behalf of the U.S. Government, a brief privacy statement. At the discretion of airlines and travel agencies, reservation agents may provide the notice directly to a passenger or reprogram their automated voice response units (VRUs) to provide the notice prior to being transferred to an agent. Passengers do not have an option to skip the notice.
TSA requires airlines or their agents to give, on behalf of the U.S. Government, a complete privacy notice to each traveler making a reservation. At the discretion of airlines and travel agencies, reservation agents may provide the notice directly to a passenger or reprogram their automated voice response units (VRUs) to provide passengers the option to hear the notice prior to being transferred to an agent. Passengers, in turn, may elect to skip the notice.
Section 1.8.1 Qualitative Alternatives
These alternatives are further described on the following pages. The benefits, costs, and impact on security are relative to the baseline status quo, Alternative #1.
Alternative #2: Federally-regulated watch list screening standards.
In this alternative, TSA would not assume the watch list matching function from aircraft operators but rather would require air carriers to compare passenger information to government-issued watch lists in a uniform manner. Airlines would be required to track their false positive rates and keep them below a ceiling percentage defined by the government. The airlines would be required to comply with strict guidelines and process passengers in a standard method using government-issued watch lists. The government would oversee process implementation by air carriers, provide advice, and ensure air carrier compliance. The method by which airlines achieve compliance, however, would not be regulated by the government. Air carriers would be responsible for developing/acquiring solutions for watch list comparison and clearing passengers for boarding.
Because the data collected by the carriers would not be used by the government, there would be no requirement for air carriers and other affected stakeholders such as travel agents to issue a privacy notice at the time of reservation. This could result in significant opportunity cost and labor savings for passengers, travel agents, and airline reservation agents compared to alternatives in which the Federal Government assumes the matching function, since these alternatives could require regulated entities to provide such a notice. At the same time, TSA performance standards would likely still require air carriers to modify their systems to collect additional information in order to achieve a specified reduction in the current level of false positives.
Although this alternative would have a minimal impact on regulated entities and would increase security over the status quo, it would not meet the Congressional mandates directing TSA to conduct passenger matching and cease distribution of the watch lists.
Alternative #3: TSA leverages use of CBP’s ATS or AQQ in the domestic environment.
TSA evaluated leveraging existing IT systems within DHS; however, at the time of Secure Flight’s initial development, only CBP’s Automated Targeting System (ATS) had the potential to conduct passenger watch list matching. Used at CBP’s National Targeting Center, the ATS is a web-based enforcement tool that processes incoming cargo and passenger information. The ATS picks up on anomalies and “red flags,” providing a basis for analysts at the NTC to determine what cargo or passengers are “high risk,” whether they require additional screening at the port of entry or overseas, or whether they can even enter the country.
This system could be customized to also support domestic airline passenger watch list matching. Enabling this alternative would require significant modifications be made to the existing ATS in order to effectively meet TSA’s watch list matching objectives. Compared to building upon TSA’s existing watch list matching infrastructure, TSA determined undertaking the customizations required to utilize the ATS would not be cost-effective.
More recently, CBP has developed APIS Quick Query (AQQ), a system with interactive querying capabilities similar to Secure Flight. AQQ performs watch list matching for foreign airlines that fly to and from the United States. While this system could ostensibly be used to also perform watch list matching for domestic passengers, DHS has determined that the volume of passengers far exceeds the volume currently anticipated under AQQ by as much as five to eight times. Additionally, Secure Flight can be adjusted in accordance with a change in volumes or threat conditions. To enable CBP to focus on its primary mission of border enforcement, DHS has determined that TSA should conduct watch list matching for domestic passengers and should also take over the watch list matching function from CBP. AQQ will compare the information from passengers on covered international flights flying to and from the U.S. to the consolidated Federal watch lists until Secure Flight is ready to take over that function Transferring this watch list matching function from AQQ to Secure Flight ensures a uniform standard is applied to all individuals flying to, from, and within the United States.
Alternative #4 (Preferred Alternative): Airlines request standardized passenger information at time of reservation and transmit to TSA for comparison to the Federal Government’s watch lists.
Under this option, TSA obtains passenger and non-traveler information from aircraft operators, compare such data to the Federal watch lists, and communicate results back to aircraft operators prior to passengers’ arrival at the airport. TSA relieves airlines of their current responsibility to compare domestic passenger information to Federal Government watch lists. Based on the gate and boarding pass printing instructions, aircraft operators process passengers in the normal manner, identify them for enhanced screening at a security checkpoint, or deny them transport or authorization to enter the airport sterile area.
Airline reservation systems and GDSs are responsible for making modifications to their IT infrastructure in order to accept additional data fields in a standardized format. Since passenger information will be transmitted to the Federal Government, airlines are required to make available a privacy notice prior to collecting information on a website or self-service kiosk. Collecting additional passenger information requires changes at airline reservation call centers and travel agencies.
This alternative limits the dissemination of Federal Government watch lists outside the government, increasing aviation security over the status quo and over the Federal Standards alternative. This alternative also meets the Congressional mandate to reduce false positives by 1) standardizing the collection of information, ensuring uniform comparison of passenger data to watch list records, and 2) centralizing the matching process, reducing the likelihood that a passenger will be falsely selected by multiple airlines.
Comparison of Alternatives #1 through #4.
Table 1.8.1.a Qualitative Comparison of Regulatory Alternatives |
||||
Alternative |
1 |
2 |
3 |
4 |
Description |
Baseline Status Quo |
Federally Regulated Standards |
TSA Leverages Use of CBP’s ATS or AQQ |
TSA Compares Passenger Info to Watch Lists, Own System |
Benefits |
||||
Government Assumes Responsibility |
No |
No |
Yes |
Yes |
Reduces False Positives |
No |
Yes |
Yes |
Yes |
Standardizes Matching Method |
No |
Yes |
Yes |
Yes |
Centralizes Watch Lists |
No |
No |
Yes |
Yes |
Impact on Security |
None |
Medium |
High |
High |
Costs |
||||
Additional Costs |
None |
Low |
High |
Medium |
Alternative 4 meets all applicable Congressional mandates in the most cost-effective manner.
Section 1.8.2 Quantitative Alternatives
The following alternatives are modifications of Alternative #4 and have similar operational requirements, benefits, and impacts on security. These options were considered by TSA as it evaluated the various means of implementing the chosen alternative for domestic operations. For example, although Alternative #4 specifies that airlines and travel agents should request additional passenger information, TSA had to determine how much information it should require. Similarly, while TSA determined airlines should make available a privacy notice to passengers prior to collecting their information, TSA evaluated several means of balancing this interest in transparency with the burden it imposes on both domestic airlines and travel agencies.
Alternative
#4 (quantified): Require reservation agents to request limited
passenger data and post the TSA privacy notice on websites.
In this, the chosen alternative, TSA requires covered aircraft operators to request each passenger’s full name, date of birth, gender, and Redress Number or Known Traveler Number, should TSA make this number available to passengers. Reservation agents are required to also ask passengers if they have one of these numbers, which could be entered in the same field as and in place of the Redress Number.
TSA chose to require full names because the greater specificity narrows the number of records a name might match in the watch lists. TSA has determined that aside from passport information, date of birth and gender are the data elements most useful for conducting watch list matching. Thus, having a passenger’s date of birth and gender allows TSA to rule out a false positive match in most cases. Finally, by including the Redress Number, TSA will be able to automatically clear passengers who had previously been erroneously matched to the watch lists and who had submitted identification documents to TSA through its redress process. TSA determined this was the smallest set of data elements it can require and still meet its mandate of reducing false positives.
Airline host reservation systems and GDSs will have to be modified to accept these additional data elements and transmit them to TSA. Other airline systems will also have to be reprogrammed in order to process the gate and boarding pass printing instructions returned by TSA.
Airline reservation agents, including, by extension, travel agents, will realize longer times to complete reservations as a result of the requirement to ask passengers for these additional data elements. To evaluate these combined impacts, TSA estimated high, primary, and low scenarios. TSA assumed both airline reservation agents and travel agents will incur costs to request additional passenger information and estimated it will take 10 to 30 seconds to collect the required data elements. Passengers making Internet reservations will need 10 seconds to enter the additional data.
TSA determined that the requirement to provide a privacy notice to passengers in the interest of transparency is satisfied by posting the TSA privacy notice on its own website and requiring airline reservation providers to do likewise. This requirement avoids imposing additional costs on stakeholders by eliminating the need for airline call centers and travel agencies to reprogram their VRUs or have an agent verbally provide the privacy notice to passengers. Of the various methods of implementing the privacy notice TSA considered, this alternative was the most cost-efficient. The costs in the table below thus present the total domestic costs of the rule under Alternative #4. TSA determined that the flexibility provided in this alternative minimizes the regulatory impact while ensuring a low rate of false positives.
High Cost Scenario |
|
Low Cost Scenario |
|
|
|
||
First-year Costs: |
$405 million |
First-year Costs: |
$269 million |
Recurring average annual costs: |
$380 million |
Recurring average annual costs: |
$291 million |
10-year PV costs (7%): |
$2,693 million |
10-year PV costs (7%): |
$2,039 million |
10-year PV costs (3%): |
$3,264 million |
10-year PV costs (3%): |
$2,471 million |
Alternative #5: Require additional SFPD attributes for watch list matching.
In this alternative, TSA would require covered aircraft operators to request each passenger and non-traveler’s home address and home phone number in addition to the full name, date of birth, gender, and Redress Number required under Alternative #4.
Since TSA would require reservation agents to specifically request an individual’s home address and home phone, airlines would be unable to send information from fields they already collect, such as billing address and contact phone number. As a result, stakeholders would have to make reprogramming changes to reservation and hosting systems beyond the modifications for the data required in Alternative #4. Aircraft operators and travel agents would also be required to change phone operator scripts and Internet reservation templates. This alternative would have minimal additional costs to the government, however.
TSA assumed collection of this additional information would require an additional 20 to 30 seconds beyond the data collection time estimated under Alternative #4. Aircraft operator call centers and travel agents would thus require a total of 60 or 30 seconds to collect all personal data requested under this alternative in the high and low cost scenarios, respectively. In both scenarios, TSA assumed passengers would need a total of 20 seconds to provide the requested data when making Internet reservations.
The benefit of this alternative would be that the additional personal data transmitted may result in a lower false positive rate, as TSA would be able to compare additional passenger elements to the information in the watch lists. Further, TSA would have more information on file for passengers that TSA matching analysts had previously identified as false positive matches against the watch lists, speeding adjudication of those passengers in the future. Given that TSA will already achieve a low rate of false positives under Alternative #4, however, this alternative would benefit a small percentage of passengers. For example, TSA testing comparing the relative effects of different data elements indicated a reduction in the match rate of 50% – 85% when full name, date of birth, and gender are present in the SFPD relative to just full name. TSA determined based on these considerations that the increased costs associated with requesting this additional information from all passengers ($537 million over ten years in the low scenario, discounted at 7%) outweigh the marginal benefit that would be realized by the few passengers affected by the lower false positive rate.
High Cost Scenario |
|
Low Cost Scenario |
|
|
|
||
First-year Costs: |
$506 million |
First-year Costs: |
$336 million |
Recurring average annual costs: |
$499 million |
Recurring average annual costs: |
$370 million |
10-year PV costs (7%): |
$3,501 million |
10-year PV costs (7%): |
$2,576 million |
10-year PV costs (3%): |
$4,255 million |
10-year PV costs (3%): |
$3,129 million |
|
|
|
|
The benefit of this alternative relative to Alternative #4 would be a slight decrease in the false positive rate due to additional data used for watch list matching. |
|||
Alternative
#6: Require reservation agents to provide a brief privacy notice for
every reservation.
This alternative would require airline reservation agents, including, by extension, travel agents to provide a brief privacy notice during every reservation prior to collecting information from passengers. The reservation process for non-traveling individuals and passengers making both in-person and online reservations would be unchanged from Alternative #4. By contrast, however, this alternative would require reservation agents to provide a short privacy statement to passengers making reservations over the telephone.
This alternative would ensure that every passenger was informed that his or her personal information would be shared with TSA. Rather than requiring reservation agents to provide the entire privacy notice, however, TSA determined a brief statement would be sufficient. This statement would advise passengers that their reservation information would be shared with TSA and that they should go to www.tsa.gov for more information.
This interpretation may or may not result in costs to reservation agents due to the availability of automated voice response units (VRUs), which could be modified to provide the notice to passengers prior to transferring them to a reservation agent. TSA assumed all airline call centers would have VRUs, as would many larger travel agencies. TSA determined that only small travel agencies, as defined by the Small Business Administration, would actually be affected by the privacy notice requirement in this alternative. The SBA defines a “small” travel agency as a firm with fewer than $3.5 million in annual revenue.43 SBA data indicates that in 2003, the most recent year for which data was available, agencies with less than $5 million in annual revenue accounted for 35% of all reported travel agency revenues.44 Consequently, TSA evaluated a high scenario where travel agents verbally provide a 20 second privacy notice to passengers during 35% of their reservations, and a low scenario where neither travel agents nor airline reservation agents realize costs as a result of the notice. Passengers, however, would incur an opportunity cost of 10 to 20 seconds for every reservation in either scenario since they would not have the option to avoid listening to it.
High Cost Scenario |
|
Low Cost Scenario |
|
|
|
|
|
First-year Costs: |
$512 million |
First-year Costs: |
$336 million |
Recurring average annual costs: |
$505 million |
Recurring average annual costs: |
$370 million |
10-year PV costs (7%): |
$3,546 million |
10-year PV costs (7%): |
$2,576 million |
10-year PV costs (3%): |
$4,310 million |
10-year PV costs (3%): |
$3,129 million |
|
|
|
|
The benefit of this alternative would be greater assurance that passengers making telephone reservations were aware that their information would be shared with TSA. |
|||
Alternative #7: Reservation agents provide full privacy notice.
In this alternative, TSA would require airlines to provide all persons making domestic air travel reservations with the option of listening to the full privacy notice, which would inform them 1) that the information is being collected on behalf of the government; 2) that provision of the information is voluntary; 3) of the legal authorization for the collection; and, 4) for what purposes the information will be used. To comply with this requirement airlines and travel agents would orally issue the notice to persons making telephone reservations or reprogram their VRUs. Persons making reservations using the Internet would have to check a box indicating they had read the privacy notice prior to being able to complete the reservation process and authorize transmission of their information to the airline reservation system.
TSA anticipated covered aircraft operators and travel agents would minimize the cost of this alternative by modifying their VRUs to provide the person making the reservation with an option to hear the notice before being transferred to a reservation agent. Given the absence of data on both passenger preferences and the percentage of aircraft operators and travel agents that would use automated systems, however, TSA evaluated the full range of the possible impact of this alternative by assuming in the high scenario that 100% of persons making telephone reservations would elect to hear the notice and those notices would be given verbally by the reservation agent. The low scenario assumes all telephone reservations would be provided notice by an automated system and that all passengers would elect to skip the notice. TSA estimated reservation agents would need 45 seconds to issue the full privacy notice. TSA estimates of the cost impacts of these various scenarios are shown below. This alternative yields costs equivalent to Alternative #4 in the low scenario because TSA assumed agents would not incur costs to issue the notice. Both the primary (midpoint) and high estimates, however, are higher than in Alternative #4.
Comparison of Alternatives
Table 1.8.2.a Quantitative Comparison of Regulatory Alternatives |
||||
Alternative |
4 |
5 |
6 |
7 |
Description |
Full Name, DOB, and Redress Number Required at time of reservation; privacy notice provided online |
Alternative 4 + Home Address and Home Phone requested at time of reservation |
Alternative 4 with requirement for issuance of privacy notices for telephone reservations |
Full privacy notice made available during phone reservations; passengers may opt to skip notice |
Domestic Costs (Millions of 2005 $, Primary Estimate) |
||||
First Year Costs |
$331 |
$415 |
$447 |
$561 |
Average Annual Recurring Costs |
323 |
422 |
460 |
597 |
10-year PV costs (7%) |
2,301 |
2,974 |
3,230 |
4,158 |
10-year PV costs (3%) |
$2,787 |
$3,613 |
$3,927 |
$5,066 |
Benefits |
||||
Compared to Alternative #4. |
-- |
Reduced false positive rate possible. |
Passengers making telephone reservations are provided notice. |
More thorough notification of privacy rights; passengers may skip notice. |
Section 1.8.3 Comparison of Preferred Alternative Against Timing Variations
TSA compared the Secure Flight program at full implementation (both domestic and international passengers) at varying times of data submission from the airline operators. TSA assessed the following alternative times of data submission: 72 hours prior to the scheduled time of flight departure (which is the preferred scenario that TSA adopted); 48 hours prior to the scheduled time of flight departure; 24 hours prior to the scheduled time of flight departure; and 30 minutes prior to the scheduled time of flight departure (which is comparable to the requirements in the APIS Predeparture Final Rule). For the 72 hour alternative, TSA calculated the cost to the government, the airline industry, and the traveling public in Section 6 of this Regulatory Evaluation Analysis. The analysis below discusses and compares the impact on the government, the airline industry, and the traveling public of each alternative. However, TSA was able to quantify only the Secure Flight hardware, software, and personnel costs for all four alternatives. With respect to the airline industry and traveling public, the analysis below identifies and discusses the impacts but does not assign specific amounts because TSA was unable to obtain sufficient information to calculate the full costs.
Comparison of Alternatives
Alternative #4: 72 Hours Prior to Departure (Preferred Alternative)
In this alternative, airline operators will send TSA the initial submission of SFPD no sooner than 72 hours prior to departure. The preferred 72-hour alternative is the baseline representing the current Secure Flight design and implementation plan. The economic impact of the preferred 72-hour is discussed in Sections 5, 6, and 7 of this Regulatory and Economic Analysis. The costs in the table below are the program costs to the government, which are described in total earlier in this evaluation in Table 1.6.5.a. For this alternative, the column “Baseline Hardware, Licenses Maintenance” corresponds exactly to the “Information Technology” column in Table 1.6.5.a, and the values in the “Baseline CSA & SFA Staffing” column represent a subset of the program costs reported in the “Implementation, Operations Planning and Service Center” column of Table 1.6.5.a.
TSA chose the 72-hour timing requirements for several reasons. Under this Final Rule, all Secure Flight processing should be complete for SFPD prior to boarding pass issuance. Covered aircraft operators currently permit their passengers to check-in and obtain a boarding pass 24 hours prior to the scheduled departure of their flights. To maintain this current practice, TSA has 48 hours to perform the automated watch list matching and to conduct the appropriate manual processes. It also provided the government with sufficient time to arrange for any appropriate operational responses. Secure Flight allocates18 hours to receive batches of SFPD and process them through the automated watch list matching. This leaves 30 hours for the manual review process. This manual review process includes review by TSA personnel and, if necessary, review by and coordination with TSC and other governmental agencies involved in identifying and investigating suspected and known terrorists. The preferred 72-hour alternative will allow TSA sufficient time to clear manually many potential matches identified through the automated watch list matching process and minimize the number of passengers that need to go to the airport for resolution. In addition, TSA needs sufficient time to coordinate with other governmental agencies to confirm matches and arrange for any appropriate operational responses and the preferred 72-hour alternative provides adequate time.
According to interviews with aircraft operators in February 2006, TSA was able to estimate that 90% of flight reservations are made in advance of 72 hours before flight departure. Because TSA will be able to conduct automated watch list matching and manual review for 90 per cent of passengers prior to 24 hours before the scheduled departure time, it will be able to manage its resources to treat SFPD submitted within 24 hours of a flight as a high priority request and will return the results at the rate of up to 2.5 names per second. Thus, with the preferred 72-hour alternative, TSA will be able to manage its resources in a manner that will minimize disruption in the boarding pass issuance process.
As stated above, TSA is able to quantify the cost of Secure Flight hardware, software, and personnel for all four alternatives considered. Below are these costs for the preferred 72-hour alternative:
Alternative #4: 72 Hours Prior to Departure (millions of 2005 $)
Year |
Baseline Hardware Licenses Maintenance |
Baseline CSA & SFA Staffing |
Total |
Total 7% Discount |
Total 3% Discount |
1 |
13.30 |
8.67 |
$21.97 |
$20.5 |
$21,3 |
2 |
8.3 |
21.35 |
29.65 |
25.9 |
27.9 |
3 |
7.3 |
21.66 |
28.96 |
23.6 |
26.5 |
4 |
8.9 |
22.60 |
31.50 |
24.0 |
28.0 |
5 |
11.7 |
23.59 |
35.29 |
25.2 |
30.4 |
6 |
11.4 |
24.60 |
36.00 |
24.0 |
30.1 |
7 |
9.2 |
25.64 |
34.84 |
21.7 |
28.3 |
8 |
8.1 |
26.91 |
35.01 |
20.4 |
27.6 |
9 |
9.8 |
28.04 |
37.84 |
20.6 |
29.0 |
10 |
12.9 |
29.19 |
42.09 |
21.4 |
31.3 |
Total |
$100.90 |
$232.25 |
$333.15 |
$227.3 |
$280.6 |
Alternative #8: 48 Hours Prior to Departure
Under this alternative, aircraft operators would submit SFPD in batches for each flight, 48 hours prior to the scheduled departure time. To maintain the current practice of allowing passengers to obtain boarding passes up to 24 hours prior to the scheduled flight departure time, TSA would have 24 hours to perform the automated watch list matching and to conduct the appropriate manual processes. Processing for each batch would begin immediately upon receipt. This timeline allows 9 hours to perform the automated watch list matching and 15 hours to conduct the manual review process.
The costs to covered aircraft operators under the 48-hour alternative are similar to the costs identified in Section 6 of this Regulatory and Economic Analysis because they would need to reprogram their systems and implement Secure Flight in a similar manner as they would under the preferred 72-hour alternative. Covered aircraft operators would incur similar costs for reprogramming the travel reservation system and implementing the requirements of Secure Flight including collection of information from individuals. Because TSA would have less time to complete the manual processes, TSA may not be able to clear some passengers prior to the passengers checking in at the airport that it may otherwise be able to clear if given more time. With potentially more passengers going to the ticket counter to present their verifying identity document to obtain a boarding pass, covered aircraft operators may need to hire more personnel to handle the increased number of passengers at the ticket counter. Thus, the 48-hour alternative may increase staffing costs for covered aircraft operators. TSA was unable to estimate the amount of the increased staffing costs.
Passengers would also incur similar opportunity costs identified in Section 6 of this Regulatory and Economic Analysis because they would provide the same required information to covered aircraft operators and may also read the Privacy Notice as they would under the preferred 72-hour alternative. Because TSA would have less time to complete the manual processes, TSA may not be able to clear some passengers prior to the passengers checking in at the airport that it may otherwise be able to clear if given more time. Thus, if TSA were to adopt the 48-hour alternative, some passengers may incur additional opportunity costs of having to go to the airport to present their verifying identity document to obtain a boarding pass. Further, some of these passengers may miss their flights because there would not be sufficient time at the airport to clear them. TSA was unable to estimate the amount of the increased opportunity costs for passengers.
The 48-hour alternative has a significant impact on the government in terms of cost and decreased benefit of the Secure Flight program. To process all SFPD in a shorter amount time TSA would need to invest in more Secure Flight hardware, software, and personnel. Below are the total costs of the Secure Flight hardware, software, and personnel for the 48-hour alternative:
Alternative #8: 48 Hours Prior to Departure (millions of 2005 $)
-
Year
Additional
Hardware
Licenses
MaintenanceAdditional
StaffingTotal
Total 7% Discount
Total 3% Discount
1
$4.50
0
$4.50
$4.30
$4.40
2
$0.54
$0.757
$1.30
$1.17
$1.24
3
$0.54
$0.757
$1.30
$1.09
$1.20
4
$0.54
$0.757
$1.30
$1.02
$1.17
5
$0.54
$0.757
$1.30
$0.95
$1.13
6
$0.54
$0.757
$1.30
$0.89
$1.10
7
$0.54
$0.757
$1.30
$0.83
$1.07
8
$0.54
$0.757
$1.30
$0.78
$1.04
9
$0.54
$0.757
$1.30
$0.73
$1.01
10
$0.54
$0.757
$1.30
$0.68
$0.98
total
$4.87
$6.815
$16.20
$12.44
$13.94
One of the security benefits of the Secure Flight program is that the federal government will have greater visibility on potential matches to the watch list. By obtaining information about potential matches over 50 hours before the scheduled flight departure time under the 72-hour alternative, TSA will have more time to coordinate with other government agencies such as the FBI to confirm a match and to plan any appropriate responses. Under the 48-hour alternative, TSA would have less than 40 hours to conduct this coordination and planning. According to the experts in the federal government this difference in time would make this coordination and planning more difficult and would have a negative effect on the security benefit of Secure Flight.
The 48-hour alternative would not decrease the cost of the Secure Flight program for the covered aircraft operators and passengers and may, in fact, increase some of the costs. This alternative would increase the overall TSA costs of the program because of the increased hardware, software, and personnel costs. It would also reduce the security benefit of the Secure Flight program. Thus, TSA is not adopting the 48-hour alternative because of the impact it would have on the effectiveness of Secure Flight as a security program. Additionally, this impact is not offset by any cost savings to covered aircraft operators, the passengers, or the federal government.
Alternative #9: 24 Hours Prior to Departure
Under this alternative, aircraft operators would submit SFPD in batches for each flight, 24 hours prior to the scheduled departure time. However, as the 24-hour advance check-in window is also open, many passengers will request to check-in before Secure Flight has processed the corresponding SFPD. Aircraft operators would submit real-time SFPD transactions for passengers who request check-in before the results of the automated batch and manual review processes are available. Thus covered aircraft operators may send more than one SFPD request for the same passenger – one request as part of the 24-hour batch transmission and another high priority request when the passenger checks in if the covered aircraft operator has not received a response to the initial batch transmission.
The costs to covered aircraft operators under the 24-hour alternative are similar to the costs identified in Section 6 of this Regulatory and Economic Analysis. Covered aircraft operators would incur similar costs for reprogramming the travel reservation system and implementing the requirements of Secure Flight including collection of information from individuals as they would under the preferred 72-hour alternative because they would need to reprogram their systems and implement Secure Flight in a similar manner. Based on testing, TSA estimates that a few thousand SFPD will need to undergo manual review as the result of the automated watch list matching process. For many passengers whose SFPD must under manual review TSA would not be able to complete the manual review process prior to their checking in at the airport. Consequently, these passengers would need to go the ticket counter to present their verifying identity document for resolution. With potentially more passengers going to the ticket counter to present their verifying identity document to obtain a boarding pass, covered aircraft operators may need to hire more personnel to handle the increased number of passengers at the ticket counters. Thus, the 24-hour alternative may increase staffing costs for covered aircraft operators. TSA was unable to estimate the amount of the increased staffing costs.
Some covered foreign air carriers may obtain some savings with the 24-hour alternative because of how their reservation systems and their departure control systems (DCS) are programmed. These covered foreign air carriers’ reservations systems, from which the covered foreign air carriers would send the SFPD batch transmission, and DCS, to which the covered foreign air carriers may receive the boarding pass printing instructions, currently do not communicate with each other and they would incur some costs to accommodate this situation under the preferred 72-hour alternative and the 48-hour alternative. Under the 24-hour alternative, however, these covered foreign air carriers would be able to transmit SFPD and to receive boarding pass printing instructions from their DCS and would not involve their using their reservation systems. Thus these covered foreign air carriers would not incur the costs of accommodating the two systems. TSA was unable to estimate the amount of this saving but it is unlikely that the savings would be a substantial amount.
Passengers would also incur similar opportunity costs identified in Section 6 of this Regulatory and Economic Analysis because they would provide the same required information to covered aircraft operators and may also read the Privacy Notice as they would under the preferred 72-hour alternative. Passengers who are unable to check in via the Internet would need to obtain their boarding pass at the airport causing longer lines for the check-in kiosks. Longer lines would result in higher opportunity cost to the passengers because of the increased wait time at the airport to check in for their flights. Additionally, because TSA would have less time to complete the manual processes, TSA may not be able to clear some passengers prior to the passengers checking in at the airport that it may otherwise be able to clear if given more time. Thus, if TSA were to adopt the 24-hour alternative, some passengers may incur additional opportunity costs of having to go to the airport to present their verifying identity document to obtain a boarding pass. Further, some of these passengers may miss their flights because there would not be sufficient time at the airport to clear them. TSA was unable to estimate the amount of the increased opportunity costs for passengers.
The 24-hour alternative has a significant impact on the government in terms of cost and decreased benefit of the Secure Flight program. TSA calculated that most flights depart in an 18-hour window (0600 EST to 1200 midnight EST). This means TSA would receive and need to process the majority of the 2.24 million SFPD received each day in an 18-hour window. In order to do so, the Secure Flight system would need to support automated watch list matching of 40 passengers per second with each transaction taking less than 4 seconds and would need ability to process 80 passengers per second due to flight departures not evenly distributed throughout the day. To process all SFPD in a shorter amount time TSA would need to invest in more Secure Flight hardware, software, and personnel. Below are the total costs of the Secure Flight hardware, software, and personnel for the 24-hour alternative:
Alternative #9: 24 Hours Prior to Departure (millions of 2005 $)
-
Year
Additional
Hardware
Licenses
MaintenanceAdditional
StaffingTotal
Total 7% Discount
Total 3% Discount
1
$10.4
$0.0
$10.4
$9.70
$10.08
2
$1.7
$1.3
$3.0
$2.72
$2.89
3
$1.7
$1.3
$3.0
$2.55
$2.81
4
$1.7
$1.3
$3.0
$2.38
$2.73
5
$1.7
$1.3
$3.0
$2.22
$2.65
6
$1.7
$1.3
$3.0
$2.08
$2.57
7
$1.7
$1.3
$3.0
$1.94
$2.49
8
$1.7
$1.3
$3.0
$1.82
$2.42
9
$1.7
$1.3
$3.0
$1.70
$2.35
10
$1.7
$1.3
$3.0
$1.59
$2.28
total
$25.96
$11.68
$37.6
$28.70
$33.27
One of the security benefits of the Secure Flight program is that the federal government will have greater visibility on potential matches to the watch list. By obtaining information about potential matches over 50 hours before the scheduled flight departure time under the 72-hour alternative, TSA will have more time to coordinate with other government agencies such as the FBI to confirm a match and to plan any appropriate responses. Under the 24-hour alternative, TSA would have minimal time to conduct this coordination and planning. According to the experts in the federal government this difference in time would make this coordination and planning more difficult and would have a negative effect on the security benefit of Secure Flight.
The 24-hour alternative would not decrease the cost of the Secure Flight program for the covered aircraft operators and passengers and would likely increase some of the costs. This alternative would increase the overall TSA costs of the program because of the increased hardware, software, and personnel costs. It would also reduce the security benefit of the Secure Flight program. Thus, TSA is not adopting the 24-hour alternative because of the impact it would have on the effectiveness of Secure Flight as a security program. Additionally, this impact is not offset by cost savings to covered aircraft operators, the passengers, or the federal government.
Alternative #10: 30 Minutes Prior to Departure (APIS requirement)
Under this alternative, all Secure Flight processing would take place at 30 minutes prior to a flight departure. All SFPD transactions would be submitted to Secure Flight as passengers check-in for flights, and automated watch list matching would be performed “just in time” in interactive mode. This alternative is similar to the requirements in CBP’s APIS Pre-departure Final Rule.
With no batch transmission of SFPD, TSA would not be able to conduct automated watch list matching and any necessary manual review in advance of a passenger check-in request. Under this alternative, passengers would not longer have the option of checking in during the 24-hour window prior to flight departure as is current aircraft operator practice. All passengers would need to come to the airport to check in and to wait for TSA to complete the automated watch list matching and any necessary manual review prior to receiving a boarding pass. This consequence of the 30-minute alternative has considerable impacts on covered aircraft operators, passengers, and the federal government.
Many of the covered aircraft operators would reprogramming costs because they are not subject to APIS Predeparture Final Rule and have not reprogrammed their systems to comply with the APIS Predeparture Final Rule. All covered aircraft operators would incur implementation costs including costs for data collection and transmission. Because all passengers would need to go to the airport to check in and to obtain a boarding pass, covered aircraft operators would lose the benefits and savings of having many of their passengers check in via the Internet. Covered aircraft operators would need to invest in more kiosks at the airport to handle check in for all of their passengers that do not go to the ticket counter and would need to address congestion at the airport. Because TSA would have no time to conduct manual review, a few thousand passengers each day would need to go to the ticket counter and wait for the manual review process to be completed before they are able to obtain boarding passes. As a result, covered aircraft operators’ agents at the ticket counter would likely need to spend more time with each passenger whose SFPD are be subject to manual review. For most of these passengers, 30 minutes prior to scheduled flight departure time would not likely be sufficient time for TSA to complete the manual review process and for the passengers to proceed through the security checkpoint to their departure gate. Thus many of these passengers would likely miss their flight and the covered aircraft operators would incur the costs associated with rebooking them on other flights.
Some covered aircraft operators may experience savings under the 30-minute alternative because they have already reprogrammed their systems to comply with the APIS Predeparture Final Rule. While TSA was unable to estimate the costs of the impact discussed in the paragraph above, TSA believes that these costs would significantly outweigh the savings resulting from these covered aircraft operators not needing to reprogram their systems.
Passengers would also incur similar opportunity costs identified in Section 6 of this Regulatory and Economic Analysis because they would provide the same required information to covered aircraft operators and may also read the Privacy Notice as they would under the preferred 72-hour alternative. Passengers would not be able to check in via the Internet and would need to obtain their boarding pass at the airport causing longer lines for the check-in kiosks. Longer lines would result in higher opportunity cost to the passengers because of the increased wait time at the airport to check in for their flights. At some airports, many passengers would likely miss their flights because 30 minutes is not sufficient time to obtain a boarding pass from a kiosk or the ticket counter, to proceed through the security checkpoint, and to travel to the departure gate.
Additionally, because TSA would not be able to conduct the manual processes until the passengers arrive at the airport, TSA would not be able to clear some passengers prior to the passengers checking in at the airport that it may otherwise be able to clear if given more time. A few thousand passengers each day would incur opportunity costs because the automated watch list matching process identified them as potential matches to the watch list. These passengers would incur the opportunity cost of having to go to the airport to present their verifying identity document to obtain a boarding pass and of waiting at the ticket counter as TSA completes the manual processes. For most of these passengers, 30 minutes prior to scheduled flight departure time would not likely be sufficient time for TSA to complete the manual review process and for the passengers to proceed through the security checkpoint to their departure gate. Thus many of these passengers would incur additional opportunity costs because they would miss their flights. TSA was unable to estimate the amount of the increased opportunity costs for passengers but believes that these costs would be considerable.
The federal government would also incur additional costs under the 30-minute alternative than it would under the preferred 72-hour alternative. TSA would need to redesign the Secure Flight infrastructure and design and update of DHS router which could impact CBP’s APIS Pre-departure implementation. At a minimum, the Secure Flight system would need to support automated watch list matching of 40 passengers per second with each transaction taking less than 4 seconds and would need ability to process 80 passengers per second due to flight departures not evenly distributed throughout the day. To process all SFPD as “just in time” transactions, TSA would need to invest in more Secure Flight hardware, software, and personnel. Below are the total costs of the Secure Flight hardware, software, and personnel for the 24-hour alternative:
Alternative #10: 30 Minutes Prior to Departure -- APIS requirement (millions of 2005 $)
-
Year
Additional
Hardware
Licenses
MaintenanceAdditional
StaffingTotal
Total 7% Discount
Total 3% Discount
1
$10.4
$0.0
$10.4
$9.70
$10.08
2
$1.7
$1.3
$3.0
$2.72
$2.89
3
$1.7
$1.3
$3.0
$2.55
$2.81
4
$1.7
$1.3
$3.0
$2.38
$2.73
5
$1.7
$1.3
$3.0
$2.22
$2.65
6
$1.7
$1.3
$3.0
$2.08
$2.57
7
$1.7
$1.3
$3.0
$1.94
$2.49
8
$1.7
$1.3
$3.0
$1.82
$2.42
9
$1.7
$1.3
$3.0
$1.70
$2.35
10
$1.7
$1.3
$3.0
$1.59
$2.28
total
$25.96
$11.68
$37.6
$28.70
$33.27
One of the security benefits of the Secure Flight program is that the federal government will have greater visibility on potential matches to the watch list. By obtaining information about potential matches over 50 hours before the scheduled flight departure time under the 72-hour alternative, TSA will have more time to coordinate with other government agencies such as the FBI to confirm a match and to plan any appropriate responses. Under the 30-minute alternative, TSA would have little to no time to conduct this coordination and planning and this security benefit would be lost. .
The 30 minute alternative would not decrease the cost of the Secure Flight program for the covered aircraft operators and passengers and would likely increase some of the costs substantially. This alternative would increase the overall TSA costs of the program because of the increased hardware, software, and personnel costs. It would also reduce the security benefit of the Secure Flight program. Thus, TSA is not adopting the 30 minute alternative because of the impact it would have on the effectiveness of Secure Flight as a security program and the additional costs to covered aircraft operators, the passengers, or the federal government.
Summary of Comparison of Alternatives
The table below, Table 1.8.3a, summarizes the impact of the alternatives on the federal government, covered aircraft operators, and passengers. The impacts in this table are impacts that TSA was not able to estimate actual costs.
Table 1.8.3.a Qualitative Comparison of Regulatory Timing Alternatives |
||||
Alternative |
4 |
8 |
9 |
10 |
Description |
72 Hour Alternative |
48 Hour Alternative |
24 Hour Alternative |
30 Minute Alternative (APIS Rule) |
Technologically Feasible |
Current program development and implementation plan.
Based on 18 hours automated watch list matching and 6-30 hours for manual review. |
Need to double the number of servers to cut time required for automated watch list matching in half.
Increase in infrastructure servers. |
Reevaluation of architecture of Secure Flight system and DHS router.
|
Reevaluation of architecture of Secure Flight system and DHS router. New hardware and software licenses needed.
|
Effectiveness of Watch List Matching |
No impact to effectiveness as it is the baseline. |
No impact. |
Provides minimal time to coordinate an operation response if necessary. |
Provides little to no time to coordinate an operation response if necessary.
Most reservations that require manual review or resolution will result in either delayed or missed flights. |
Operational Impact |
No impact as it is the current implementation design. |
Increase in Secure Flight Analysts by 25% compared to 72-hour baseline. |
Increase in Secure Flight Analysts by 25% compared to 72-hour baseline.
Increase Customer Support Agents by 25% compared to 72-hour baseline. |
All watch list matches must be resolved real-time at check-in counter by calling the Service Center. Some resolutions require multiple agencies and the handle time would be greater than 30 minutes. Increase in Secure Flight Analysts by 25% compared to 72-hour baseline. Increase Customer Support Agents by 25% compared to 72-hour baseline. |
Stakeholder Impact |
The costs to covered aircraft operators are described in Section 6 of this Regulatory and Economic Analysis.
Manual review will clear a percentage of passengers who will not be required to check-in at the ticket counter.
Systems modifications needed for both reservations and departure control systems. |
The cost to covered aircraft operators are similar to those described in Section 6 of this Regulatory and Economic Analysis.
Aircraft operators will have different regulatory requirements regarding timing of transactions for APIS and Secure Flight. |
The cost to covered aircraft operators are similar to those described in Section 6 of this Regulatory and Economic Analysis.
Increased Internet check-in resources, additional self-service kiosks and airport agent counter check-in facilities. |
Additional self-service kiosks and airport agent counter check-in facilities. Simplifies application for poorly integrated reservations and departure systems, but increases infrastructure requirements due to high volume messaging. Potential for increased false positives due to no time to perform manual review.
Covered aircraft operators that have already reprogrammed to comply with APIS Predeparture Final Rule may incur Secure Flight reprogramming costs.
|
Passenger Impact |
The opportunity costs to passengers are described in Section 6 of this Regulatory and Economic Analysis.
Automatic and manually reviewed cleared passengers will be able to utilize the Internet and kiosks for check-in rather than go to the ticket counter for clearance. |
The opportunity costs to passengers are similar to those described in Section 6 of this Regulatory and Economic Analysis.
Potential matches to the Selectee and/or No Fly watch lists may have increased incidence of missed flights due to time spent at ticket counter for resolution with verifying identity document. |
The opportunity costs to passengers are similar to those described in Section 6 of this Regulatory and Economic Analysis.
Potential matches to the Selectee and/or No Fly watch lists may have increased incidence of missed flights due to time spent at ticket counter for resolution and/or manual review. |
The opportunity costs to passengers are similar to those described in Section 6 of this Regulatory and Economic Analysis. Passengers will not be able to receive boarding pass via Internet check-in. Therefore, all passengers must check in at airport.
Potential matches to the Selectee and/or No Fly watch lists may have increased incidence of missed flights due to time spent at ticket counter for resolution and/or manual review. |
The table below, Table 1.8.3.b, represents the total costs for the 72 hour preferred alternative and the total costs for Secure Flight hardware, software, and personnel for the various timing alternatives to the baseline scenario.
Table 1.8.3.b Quantitative Comparison* of Regulatory Timing Alternatives
Year |
72-Hour (preferred) |
48-Hour |
24-Hour |
30-Minute (APIS-like) |
||||||||
Total Costs |
Total Costs |
Total Costs |
Total Costs |
|||||||||
|
7% |
3% |
|
7% |
3% |
|
7% |
3% |
|
7% |
3% |
|
1 |
$22.66 |
$21.18 |
$22.00 |
$27.16 |
$25.48 |
$26.40 |
$33.06 |
$30.88 |
$32.10 |
$33.06 |
$30.88 |
$32.10 |
2 |
$39.42 |
$34.43 |
$37.16 |
$40.72 |
$35.63 |
$38.36 |
$42.42 |
$37.13 |
$40.06 |
$42.42 |
$37.13 |
$40.06 |
3 |
$43.38 |
$35.41 |
$39.70 |
$44.68 |
$36.51 |
$40.90 |
$46.38 |
$37.91 |
$42.50 |
$46.38 |
$37.91 |
$42.50 |
4 |
$45.34 |
$34.59 |
$40.28 |
$46.64 |
$35.59 |
$41.48 |
$48.34 |
$36.99 |
$42.98 |
$48.34 |
$36.99 |
$42.98 |
5 |
$50.12 |
$35.73 |
$43.23 |
$51.42 |
$36.73 |
$44.33 |
$53.12 |
$37.93 |
$45.83 |
$53.12 |
$37.93 |
$45.83 |
6 |
$50.99 |
$33.98 |
$42.70 |
$52.29 |
$34.88 |
$43.80 |
$53.99 |
$36.08 |
$45.30 |
$53.99 |
$36.08 |
$45.30 |
7 |
$50.02 |
$31.15 |
$40.67 |
$51.32 |
$31.95 |
$41.77 |
$53.02 |
$33.05 |
$43.17 |
$53.02 |
$33.05 |
$43.17 |
8 |
$50.21 |
$29.22 |
$39.64 |
$51.51 |
$30.02 |
$40.64 |
$53.21 |
$31.02 |
$42.04 |
$53.21 |
$31.02 |
$42.04 |
9 |
$53.30 |
$28.99 |
$40.85 |
$54.60 |
$29.69 |
$41.85 |
$56.30 |
$30.69 |
$43.25 |
$56.30 |
$30.69 |
$43.25 |
10 |
$57.72 |
$29.34 |
$42.95 |
$59.02 |
$30.04 |
$43.55 |
$60.72 |
$30.94 |
$45.25 |
$60.72 |
$30.94 |
$45.25 |
Total |
$463.16 |
$314.03 |
$389.18 |
$479.36 |
$326.53 |
$403.08 |
$500.56 |
$342.63 |
$422.48 |
$500.56 |
$342.63 |
$422.48 |
Conclusion
The overarching goal for the Secure Flight Program is to enhance security by conducting watch list matching of the names of passengers and non-travelers. When TSA assumes the watch list matching responsibility under the fully implemented Secure Flight program, TSA will conduct the watch list matching for all flights conducted by covered U.S. aircraft operators, including flights between two international points; for all flights operated by covered foreign air carriers that fly to or from the United States or overfly the continental United States; and for non-travelers who are seeking authorization to enter a sterile area. While TSA believes that the automated process alone for vetting this significantly larger population of travelers may not take 72 hours, that process, the volume of data involved, and the increase in records requiring a manual review due to a potential match or an insufficient amount of information to differentiate someone from an individual on the watch list, and the time required to coordinate an operational response when necessary, all suggest that a 72 hour lead time is appropriate.
By requiring covered aircraft operators to transmit available SFPD 72 hours prior to departure, TSA will be able to prioritize SFPD by departure time. This prioritization will permit TSA to return a boarding pass printing result for the vast majority of passenger in time for them to print their boarding passes 24 hours in advance of their flights while returning a boarding pass printing pass result for individuals who make reservations within 72 hours of the scheduled departure in time for them to obtain their boarding passes prior to the scheduled departure time.
In contrast, the alternatives considered (48 hours, 24 hours, and 30-minutes) are not only deficient in terms of providing increased security, but demonstrate an increased cost of regulation in total, to the federal government, and to and the traveling public. Not only do the other alternatives require additional expenditures for Secure Flight hardware, software, and personnel, the 24 hour and 30-minute timing alternatives most likely would impact the covered aircraft operators’ operations, would require more passengers to check-in at the airport instead of through the Internet, and possibly result in more passengers missing their flights because they are unable to obtain their boarding pass and clear the security checkpoints in time to board their flights. While TSA is unable to calculate the costs of these impacts, we believe that the costs could be an unnecessary burden.
TSA believes that the security benefit to covered aircraft operators and passengers is such that the 72 hour requirement is a necessity.
Part 2: Final Regulatory Flexibility Analysis (FRFA)
The Regulatory Flexibility Act of 1980 (RFA) establishes “as a principle of regulatory issuance that agencies shall endeavor, consistent with the objective of the rule and of applicable statutes, to fit regulatory and informational requirements to the scale of the business, organizations, and governmental jurisdictions subject to regulation.'' To achieve that principle, the RFA requires agencies to solicit and consider flexible regulatory proposals and to explain the rationale for their actions. The Act covers a wide range of small entities, including small businesses, not-for-profit organizations, and small governmental jurisdictions. Agencies must perform a review to determine whether a proposed or final rule will have a significant economic impact on a substantial number of small entities. If the determination is that it will, the agency must prepare a regulatory flexibility analysis as described in the Act.
However, if an agency determines that a proposed or final rule is not expected to have a significant economic impact on a substantial number of small entities, section 605(b) of the 1980 RFA provides that the head of the agency may so certify and a regulatory flexibility analysis is not required. The certification must include a statement providing the factual basis for this determination, and the reasoning should be clear. Although TSA does not believe the final rule will have a significant impact on a substantial number of small entities; the agency has prepared a Final Regulatory Flexibility Analysis (FRFA).
Section 1: Reasons for and Objectives of the Final Rule
2.1.1 Reason for the Final Rule
Section 4012(a) of the Intelligence Reform and Terrorism Prevention Act requires the Transportation Security Administration (TSA) to assume from aircraft operators the function of conducting pre-flight comparisons of airline passenger information to Federal Government watch lists.
2.1.2 Objective of the Final Rule
This rule allows TSA to begin implementation of the Secure Flight program, under which TSA will receive passenger and non-traveler information, conduct watch list matching, and transmit gate and boarding pass printing instructions back to aircraft operators indicating whether individuals should be cleared to enter the sterile area, marked as selectees, or prohibited from receiving a boarding or gate pass.
Section 2: Affected Small Business Population and Estimated Impact of Compliance
2.2.1 Aircraft Operator Small Business Population
The final Secure Flight rule affects all aircraft operators conducting flight operations under a full security program per 49 CFR 1544.101(a). In general, these aircraft operators are the major passenger airlines that offer scheduled and public charter flights from commercial airports. Specifically, the covered carriers are those performing scheduled service or public charter passenger operations either with an aircraft having a passenger seating configuration of 61 or more seats or having 60 or fewer seats if the aircraft enplanes from or deplanes into a sterile area.
Of the 66 aircraft operators that are covered by the final rule, TSA estimated that 24 of these can be identified as small business entities. This is based on the Small Business Administration (SBA) Office of Size Standards’ size standard of “fewer than 1,500 employees” for small businesses within NAICS Code 481111, Scheduled Passenger Air Transportation, and those within NAICS Code 481211, Nonscheduled Chartered Passenger Air Transportation.45 For this analysis, air carrier employee counts were developed from publicly available information and from carrier filings with the U.S. Department of Transportation’s Bureau of Transportation Statistics (BTS) and Federal Aviation Administration (FAA).
In the Secure Flight regulatory evaluation, TSA divided covered carriers into four “cost groups” based on the nature of their reservations systems and BTS size classification (i.e., major, national, large regional, etc.).46 These groupings correspond to the estimated costliness of reprogramming airline reservation systems to comply with the Secure Flight requirements. Implementation Group 1 represents all legacy marketing carriers and their affiliates utilizing an older GDS or host ARS. Legacy airlines, those flying prior to the Airline Deregulation Act of 1978, are all major airlines and have the oldest computer systems. Accordingly, TSA assumed this group incurs the highest compliance costs. Implementation Group 2 includes marketing carriers utilizing a newer GDS or host ARS, as well as national carriers subscribing to an older GDS. Implementation Group 3 represents carriers with independently maintained reservation systems TSA determined were capable of receiving a direct connection to Secure Flight, as well as regional, commuter, and small airlines subscribing to an older GDS or host ARS. Airlines with very simple or no computerized reservation systems form Group 4. Rather than requiring Group 4 carriers to establish complex systems capable of connecting directly with Secure Flight, TSA allows them to transmit passenger information through a secure Internet portal.
In Groups 1 and 2, smaller airlines often use the reservation systems of larger airlines. For example, a passenger may book a reservation with a large, marketing airline, but the flight may be operated by a smaller airline owned by or contracting with the marketing airline (an affiliate). In such cases, TSA assumed in its regulatory evaluation that the marketing airline bears the cost of changes to the reservation system and designated those carriers as “points of implementation.” Section 1.4.1 of the regulatory evaluation describes this distinction in greater detail.
In the discussion below, TSA relaxes this assumption and treats affiliate carriers as if they are marketing carriers. Since no Group 1 affiliate carriers are major airlines, they were re-categorized as Group 3 carriers (regional, commuter, or small carriers using an older GDS). Specifically, these are Carriers 3, 4, 8, and 9 in the tables.47 Although this method ensures a potential cost is estimated for all small business carriers, TSA notes that it likely overstates the actual cost that will be incurred. Thus, for this small business analysis, TSA considers 10 carriers under Implementation Groups 2 and 3. The remaining 14 carriers belong to Group 4.
Table 2.2.1.a reports annual 2005 employment and operating revenues or sales48 TSA gathered for these 24 airlines (in one case the financial data is from 2002). These small air carriers are active in different areas of the passenger air transportation marketplace. Some provide scheduled passenger service in small niche markets, often as part of the larger route system of an established hub and spoke carrier; others provide charter transportation services to tour groups or organizations such as professional sports teams. Some of those that provide scheduled passenger services use reservation systems hosted by one of the existing ARS providers, while others handle phone reservations or receive reservations from travel agents. All of these small airlines are subject to the rule, however, due to the size of aircraft they use and/or because of the airport environments in which they operate. Thus, these airlines will collect more information from passengers, but TSA will take over their current requirement to compare passenger manifests to the watch lists.
Table 2.2.1.a Secure Flight Small Business Air Carriers (2005 Data) |
|||||
|
Small Business Carrier ID # |
Employees (Total Full- and Part-Time) |
Annual Operating Revenues |
Enplanements |
Share of Total Covered Carrier Enplanements |
Aircraft Operators in Implementation Groups 2 and 3 |
1 |
914 |
$204,000,000 |
1,266,293 |
0.199% |
2 |
893 |
$80,300,000 |
1,132,207 |
0.178% |
|
3 |
546 |
$78,100,000 |
838,959 |
0.051% |
|
4 |
545 |
$60,000,000 |
440,865 |
0.069% |
|
5 |
400 |
$45,100,000 |
636,768 |
0.100% |
|
6 |
380 |
$42,800,000 |
570,291 |
0.090% |
|
7 |
255 |
$18,600,000 |
49,242 |
0.008% |
|
8 |
230 |
$39,600,000 |
355,607 |
0.056% |
|
9 |
220 |
$24,000,000 |
141,252 |
0.022% |
|
10 |
50 |
$5,000,000 |
48,221 |
0.008% |
|
Aircraft Operators in Implementation Group 4 |
11 |
964 |
$74,300,000 |
208,120 |
0.033% |
12 |
826 |
$76,392,000 |
344,741 |
0.054% |
|
13 |
739 |
$137,900,000 |
506,292 |
0.080% |
|
14 |
600 |
$68,600,000 |
91,571 |
0.014% |
|
15 |
593 |
$132,500,000 |
836,409 |
0.132% |
|
16 |
549 |
$33,400,000 |
329,418 |
0.052% |
|
17 |
411 |
$105,266,000 |
82,529 |
0.013% |
|
18 |
220 |
$6,330,000 |
18,707 |
0.003% |
|
19 |
212 |
$35,649,000 |
329,083 |
0.052% |
|
20 |
159 |
$12,000,000 |
35,788 |
0.006% |
|
21 |
75 |
$14,230,000 |
22,511 |
0.004% |
|
22 |
19 |
$930,000 |
Unavailable |
Unavailable |
|
23 |
Unavailable |
Unavailable |
38,471 |
0.006% |
|
24 |
Unavailable |
Unavailable |
17,521 |
0.003% |
|
2.2.2 Estimated Impact to Aircraft Operator Small Businesses
TSA determined that the rule does not cause a significant economic impact for a substantial number of these small business entities based on several considerations. First, under the current procedures, these small airlines must devote effort to matching passenger identification information to TSA watch lists but are not able to establish staff and back office activities that are dedicated to these security functions due to the small scale of their operations. Instead, the existing security responsibilities are fulfilled by airline personnel who may have other unrelated duties. These scale considerations suggest that the benefits of changing the current responsibilities by implementing the rule may be weighted toward these smaller airlines, when considered on a per enplanement basis.
In addition, given the variety of business activities pursued by the small carriers under consideration – scheduled passenger operations or charter operations, operations that collaborate with a larger hub and spoke carrier or that are independent of larger carriers, and operations that do or do not make use of an existing ARS host for processing reservations – it is difficult to estimate the costs that are incurred by these small carriers when the rule is implemented. In order to evaluate the possible economic impact of the rule on small aircraft operators, TSA utilized two calculation methods: one for carriers in Groups 2 and 3 and a second for carriers in Group 4.
Since reprogramming and data collection costs have already been presented in the aggregate for Groups 2 and 3 in Sections 1.6.2 and 1.6.3 of the regulatory evaluation, TSA used the same techniques to calculate the potential impact to small business carriers in these two groups. Table 2.2.2.a below shows the outcome of these calculations.
TSA first assigned an estimated initial reprogramming cost to each small business carrier based on whether it belonged to Group 2 or 3 (column B). The initial reprogramming cost was used since this is the highest expenditure in any one year. Each carrier will also experience an increase in the time required to collect passenger data during reservations, as discussed in Section 1.6.3. To arrive at the maximum annual collection cost (column D), TSA annualized the total High Scenario Airline Collection Costs from Table 1.6.3.a. These airline collection costs are a function of reservations and TSA assumed an airline’s share of reservations is proportional to its share of enplanements. Thus, TSA multiplied the total annual collection cost by each carrier’s share of enplanements (column C) to arrive at its proportion of the annual collection cost (column E). Adding the collection cost to the initial reprogramming cost yielded a per-carrier estimated cost of compliance (column F). TSA divided these estimated compliance costs by each carrier’s reported revenue to determine the percent of revenue that will be expended on Secure Flight (column G).
Although there is no hard and fast definition for “significant economic impact,” agencies frequently use 2% of an entity’s revenue as a threshold. As can be seen in the table, in one case the estimated compliance cost exceeds 2% of the carriers’ reported 2005 revenues and in one case it exceeds 8%. After reviewing the relevant information, however, TSA determined the threshold may not be applicable in this particular case. This is because the percentage is extremely sensitive to the estimated reprogramming cost (column B). TSA’s estimated reprogramming costs for these carriers are based on assumptions about limited data and may overstate the costs to smaller carriers. This consideration is especially true of carrier 10. This carrier maintained its own reservation system until August 2005, when it began subscribing to a GDS. Consequently, its reprogramming costs may be significantly lower than projected here. Further, these carriers have the option to use the Secure Flight web interface rather than reprogram their reservation systems if they determine reprogramming to be too costly.
Based on these considerations, TSA determined the estimated compliance cost likely does not meet the requirements of a significant economic impact under the RFA.
Table 2.2.2.a Estimated Small Business Impact, Carrier Groups 2 and 3 |
|||||||
Small Business Carrier ID # |
2005 Annual Operating Revenues (000) |
Estimated Carrier Reprogram Costs (000) |
Share of Total Covered Carrier Enp |
Annualized Airline Collection Costs* (000) |
Share of Airline Collection Costs* (000) |
Estimated Total Compliance Cost* (000) |
Compliance Cost as % of Revenues* |
|
(A) |
(B) |
(C) |
(D) |
(E) = C*D |
(F) = B+E |
(G) = F/A |
1 |
$204,000 |
$850 |
0.20% |
$11,690 |
$23 |
$873 |
0.43% |
2 |
80,300 |
425 |
0.18 |
11,690 |
21 |
446 |
0.56 |
3 |
78,100 |
425 |
0.13 |
11,690 |
15 |
440 |
0.56 |
4 |
60,000 |
425 |
0.07 |
11,690 |
8 |
433 |
0.72 |
5 |
45,100 |
425 |
0.10 |
11,690 |
12 |
437 |
0.97 |
6 |
42,800 |
425 |
0.09 |
11,690 |
11 |
436 |
1.02 |
7 |
18,600 |
425 |
0.01 |
11,690 |
1 |
426 |
2.29 |
8 |
39,600 |
425 |
0.06 |
11,690 |
7 |
432 |
1.09 |
9 |
24,000 |
425 |
0.02 |
11,690 |
2 |
427 |
1.78 |
10 |
$5,000 |
$425 |
0.01% |
$11,690 |
$1 |
$426 |
8.52% |
* Reflect totals from the high case scenario presented in the regulatory evaluation. |
|||||||
As discussed in Section 1.6.2 of the regulatory evaluation, TSA assumed Group 4 carriers will not have any reprogramming costs associated with implementation of Secure Flight but that 13 of the 16 Group 4 carriers will spend $100,000 in the first year of the program on staff retraining and customer outreach. TSA did not have sufficient information, however, to reliably estimate costs incurred by these carriers due to changes in their reservation process. For the purpose of discussion, TSA here calculates a unit compliance cost per enplanement in order to illustrate the average impact of the rule. The results of this calculation are shown in Table 2.2.2.b.
TSA chose to use a broad assumption in developing its unit cost and therefore included the annual costs related to the entire reservations process for air transportation providers. As reported in Tables 1.6.3.a and 1.6.4.a, costs associated with the reservations process include airline and travel agency costs to make available privacy notices and request additional passenger information. In TSA’s high scenario, these two categories total to approximately $34.2 million in fiscal year 2008. This value can be normalized to a per enplanement basis using the reservations forecast reported in Table 1.4.1.a, which totals 672.1 million in 2008. This normalized cost per enplanement equals $34.2/672.1, or about $0.05 per enplanement (column B).
Multiplying this normalized value by each carrier’s 2005 annual enplanements total (column B) and adding in the implementation expenditure where applicable (column A), TSA estimated the cost to each of the small business entities identified (column D). As column F of Table 2.2.2.b indicates, this estimate for costs never exceeds 2% of 2005 annual revenues for these small carriers. Note further that the annual enplanements value is unadjusted for round trip itineraries or for reservations that may have been generated as part of a marketing carrier’s reservations process. Thus, the estimated values in Table 2.2.2.b are very likely to be overstatements of the impact of the rule on these small carriers.
Finally, as noted previously, DHS will make available a Secure Flight Internet portal for the transmittal of passenger and other itinerary data from Group 4 small airlines to TSA. The availability of this interface simplifies the transition to the environment that will prevail once the rule is implemented, while providing greater assurance regarding the provision of the relevant security data to TSA for comparison to the watch lists.
Table 2.2.2.b Illustrative Small Business Impact, Carrier Group 4 |
||||||
Small Business Carrier ID # |
Assumed Start-up Outlay |
FY 2005 Enplanements |
Maximum Unit Compliance Cost per Enplanement |
Compliance Cost |
2005 Annual Operating Revenues |
Compliance Cost as % of 2005 Revenues |
|
(A) |
(B) |
(C) |
(D) = A+B*C |
(E) |
(F) = D/E |
11 |
$100,000 |
208,120 |
$0.05 |
$110,400 |
$74,300,000 |
0.15% |
12 |
100,000 |
344,741 |
0.05 |
117,200 |
76,392,000 |
0.15 |
13 |
100,000 |
506,292 |
0.05 |
125,300 |
137,900,000 |
0.09 |
14 |
100,000 |
91,571 |
0.05 |
104,600 |
68,600,000 |
0.15 |
15 |
100,000 |
836,409 |
0.05 |
141,800 |
132,500,000 |
0.11 |
16 |
100,000 |
329,418 |
0.05 |
116,500 |
33,400,000 |
0.35 |
17 |
100,000 |
82,529 |
0.05 |
104,100 |
105,265,872 |
0.10 |
18 |
100,000 |
18,707 |
0.05 |
100,900 |
6,330,280 |
1.59 |
19 |
100,000 |
329,083 |
0.05 |
116,500 |
35,649,201 |
0.33 |
20 |
100,000 |
35,788 |
0.05 |
101,800 |
12,000,000 |
0.85 |
21 |
100,000 |
22,511 |
0.05 |
101,100 |
14,229,510 |
0.71 |
22 |
0 |
0* |
0.05 |
0 |
930,000 |
Data Not Available |
23 |
0 |
38,471 |
0.05 |
1,900 |
0 |
Data Not Available |
24 |
$0 |
17,521 |
$0.05 |
$900 |
$0 |
Data Not Available |
* Carrier had not yet begun reporting enplanements to BTS. |
||||||
The estimates provided in Table 2.2.2.b show how Group 4 small businesses would be impacted by Secure Flight were their operations comparable to those of airlines in Groups 1 through 3. As has been noted above, however, this is not the case. Consequently, the costs Group 4 airlines actually incur to comply with Secure Flight may diverge significantly from the estimates presented. Nevertheless, the table illustrates that these costs would have to increase dramatically before they would constitute a significant economic impact.
2.2.3 Travel Agency Small Business Population
The Small Business Administration (SBA) classifies any travel agency as a small business if it has revenues of less than $3.5 million annually.49 The SBA data provided in Table 2.2.3.a indicate that in 2003 more than 98% of travel agencies had annual revenues less than $5 million. Although the division of the SBA revenue categories do not allow for a precise count of the number of small business, the average revenue per firm of $1.9 million for the $1 million to $5 million category indicates that many of the firms in this category have revenues below the $3.5 million threshold. Consequently, the discussion of small businesses in the travel agency industry will be a discussion about the vast number of firms.
Table 2.2.3.a Distribution of Travel Agencies (NAICS 561510) by Revenue, 200350 |
|||||||
|
Total |
$0 -$99,999 |
$100,000 -$499,999 |
$500,000 -$999,999 |
$1,000,000 -$4,999,999 |
Total <$5,000,000 |
Total >$5,000,000 |
Number of Firms |
14,838 |
6,125 |
6,627 |
1,098 |
714 |
14,564 |
274 |
Percent of Total |
100.00% |
41.28% |
44.66% |
7.40% |
4.81% |
98.15% |
|
Tables 2.2.3.b through 2.2.3.d below reflect the recent story of the travel agent industry. The first two tables are based on 2002 data provided by the Airlines Reporting Corporation (ARC) to the National Commission to Ensure Consumer Information and Choice in the Airline Industry (the Commission).
When the Commission prepared its report Upheaval in Travel Distribution: Impact on Consumers and Travel Agents, Report to Congress and the President (Commission Report), the SBA had just increased the small business revenue threshold from $1 million to $3 million for travel agents. Consequently, the Commission used $5 million in total revenue (approximately $2.5 million in commission and fee revenue) as a proxy threshold for small businesses when creating Tables 2.2.3.b and 2.2.3.c below. Although these tables do not capture the full universe of travel agency small businesses, they nevertheless illustrate general trends affecting these entities.
As can be seen in Tables 2.2.3.b and 2.2.3.c, the number of travel agencies whose sales are less than $5 million per year declined steadily through 2001. Correspondingly, the share of industry sales by these smaller firms also fell. At the same time, however, the largest firms increased both their share of industry sales and the dollar value of their sales.
Table 2.2.3.b Number of Travel Agencies by Size Category51 |
||||
Agency Size |
1995 |
1997 |
1999 |
2001 |
$2M or Less |
19,851 |
19,226 |
17,855 |
15,253 |
$2M - $5M |
2,356 |
2,803 |
2,482 |
1,770 |
$5M - $50M |
1,059 |
1,277 |
1,236 |
1,015 |
Greater than $50M |
77 |
107 |
117 |
117 |
Total |
23,343 |
23,413 |
21,690 |
18,425 |
Table 2.2.3.c Share of Travel Agent Sales by Size Category52 |
||||
Agency Size |
1995 |
1997 |
1999 |
2001 |
$2M or Less |
25.3% |
20.6% |
16.9% |
14.2% |
$2M - $5M |
13.5 |
12.8 |
10.7 |
8.4 |
$5M - $50M |
24.8 |
24.5 |
22.5 |
20.1 |
Greater than $50M |
36.4 |
42.1 |
49.9 |
57.2 |
Table 2.2.3.d shows aggregate monthly statistics released by the Airlines Reporting Corporation indicating that the travel agent industry continued to contract and consolidate through 2005. Corresponding revenue data, however, was not available.
Table 2.2.3.d Travel Agencies Accredited by the Airlines Reporting Corporation53 |
|||||
|
2001 |
2002 |
2003 |
2004 |
2005 |
Retail Locations |
27,633 |
24,679 |
22,244 |
20,729 |
19,871 |
Home Offices |
1,651 |
1,368 |
1,203 |
1,118 |
1,041 |
Independent/Single Entities |
15,057 |
13,206 |
11,670 |
10,578 |
9,874 |
Branch |
6,696 |
6,171 |
5,695 |
5,474 |
5,451 |
Restricted Access |
862 |
950 |
1,039 |
1,120 |
1,205 |
On-site branch |
3,367 |
2,984 |
2,637 |
2,439 |
2,300 |
Satellite Ticket Providers |
6,347 |
4,693 |
3,204 |
2,413 |
1,975 |
Corporate Travel Departments |
108 |
150 |
172 |
182 |
197 |
TOTAL LOCATIONS |
34,088 |
29,522 |
25,620 |
23,324 |
22,043 |
Change over previous year |
N/A |
-13.39% |
-13.22% |
-8.96% |
-5.49% |
TOTAL ENTITIES* |
17,678 |
15,674 |
14,084 |
12,998 |
12,317 |
Change over previous year |
N/A |
-11.34% |
-10.14% |
-7.71% |
-5.24% |
*Sum of Home Offices, Independent/Single Entities, Restricted Access, and Corporate Travel Departments. |
|||||
2.2.4 Estimated Impact to Travel Agency Small Businesses
While not directly regulated, small travel agencies will certainly be affected by the implementation of Secure Flight. TSA anticipated the most significant burden on these entities results from the increased time to collect additional passenger information. Small travel agencies may also incur incremental costs due to retraining of staff and reaching out to clients in order to update customer profiles prior to their next trip.
In Section 1.6.4 of the regulatory evaluation, TSA estimated a cost that is borne by non-Internet (brick-and-mortar) travel agencies as a result of the requirements. Detailed industry data did not exist, however, that would allow TSA to determine the portion of that cost that is borne by small travel agencies. In lieu of such information, TSA chose to calculate a minimum number of airline reservations the smallest travel agency size category would have to process in order for the requirements of the rule to result in a “significant economic impact.” This calculation corresponds to the high estimate scenario and depends on a number of assumptions:
The average hourly wage of small business travel agents is $20.69 (including benefits).
In TSA’s highest cost scenario, an additional 30 seconds per airline reservation is needed to collect additional passenger information.
The additional time to collect passenger information will be incurred for every airline reservation booked through a travel agency.
The average revenue of the smallest travel agency firms (revenues between $0 and $99,999) is $47,204.54
A firm that has $47,000 annual revenue makes 124 reservations each year, given a $378 average revenue per reservation.
Accepting these assumptions, the cost per small firm would be about $23 per year, practically 0% of revenue. This is accomplished by multiplying the 124 annual reservations by the 30-seconds additional time per reservation which yields total annual seconds of 3,720 (124 x 30). This value, in turn is divided by the number of seconds in an hour to yield total annual hours of 1 (3,720/3,600). The total annual hours per travel agency is then multiplied by the average hourly wage (including benefits) of $20.69 to yield a total annual cost of $21.31 (1.03 x $20.69). Table 2.2.4.a presents this threshold number of reservations for the range of data collection times presented in the Secure Flight regulatory evaluation. Alternatively, the table also presents the number of airline reservations a travel agency would have to process to meet 2% of the SBA small business threshold for travel agents.
These estimates below should be considered as a range of “worst case scenarios.” For example, reservations made for clients for whom a travel agency already has the requested Secure Flight information saved in a profile will not incur the additional data collection time.
Table 2.2.4.a Airline Reservations Threshold for Small Business Travel Agencies |
|||||||
|
|
Revenue Class $0-$99,999 |
SBA Small Business Threshold |
||||
Firm Revenue |
(A) |
|
$47,120 |
|
|
$3,500,000 |
|
Avg. per Reservations |
(B) |
|
$378 |
|
|
$378 |
|
Annual Reservations |
(C) = A/B |
|
124 |
|
|
9,259 |
|
Add’l hours. per reservation |
(D) |
|
0.0083 |
|
|
0.0083 |
|
Add’l Annual hours |
(E) = C*D |
|
1.03 |
|
|
76.85 |
|
Avg. Agent Hourly Wage |
(C) |
|
$20.69 |
|
|
$20.69 |
|
Add’l Annual Cost |
|
|
$21.31 |
|
|
$1,638 |
|
Section 3: Significant Alternatives Considered
The final rule provides small business carriers the flexibility of either reprogramming their reservation systems to interface directly with the Secure Flight system or to transmit passenger and non-traveler information to Secure Flight through a secure Internet interface. Thus, small business carriers identified in Groups 2 and 3 have the option of joining Group 4 and using the Internet portal if they determine reprogramming their systems to communicate directly with Secure Flight is too costly. Similarly, small business carriers TSA has identified in this analysis as scheduled to use the Secure Flight Internet portal have the option to reprogram their systems to communicate directly with Secure Flight if they determine using the portal is too burdensome on their business processes.
While either method imposes some costs on small businesses, TSA determined that exempting these carriers from the requirements of the rule would fail to meet the mandate within the IRTPA that TSA assume the watch list matching function. Taking this into consideration, TSA determined the options described above would effectively minimize the impact to small businesses.
Section 4: Identification of Duplicative or Overlapping Federal Rules
TSA is aware that other Federal agencies, such as the Centers for Disease Control and Prevention (CDC) and Customs and Border Protection (CBP), collect data concerning aviation passengers and may conduct or will conduct watch list matching for these passengers. TSA is working with other agencies, including the CDC and CBP, to develop ways to eliminate unnecessary duplication of comparable screening efforts and thereby reduce governmental and private sector costs. Therefore, the rule allows TSA to relieve covered aircraft operators of the requirement to transmit passenger information if TSA determines that the U.S. government is conducting watch list matching for a passenger on a particular flight that is comparable to the screening conducted pursuant to part 1560. TSA will work with each covered aircraft operator to establish the specific procedures and times for these transmissions as it develops its Aircraft Operator Implementation Plan.
Section 5: Final Determination of No Significant Impact
Based on the considerations above, TSA believes that it is unlikely the final has a significant economic impact on a substantial number of the small entities subject to this rulemaking. In conducting this analysis, TSA acknowledges that the ability of carriers to share the incidence of security costs with their customers has been limited.
While not required by the RFA, TSA has also considered the potential impact to small business travel agencies, as these entities are likely to be indirectly impacted by the rule given their role in the airline reservation process. TSA does not believe the final rule will have a significant economic impact on a substantial number of these small business travel agencies.
Part 3: International Trade Impact Assessment
The Trade Agreement Act of 1979 prohibits Federal agencies from engaging in any standards or related activities that create unnecessary obstacles to the foreign commerce of the United States. Legitimate domestic objectives, such as security, are not considered unnecessary obstacles. The statute also requires consideration of international standards and, where appropriate, that they be the basis for U.S. standards. In addition, consistent with the Administration’s belief in the general benefits and desirability of free trade, it is the policy of TSA to remove or diminish, to the extent feasible, barriers to international trade, including both barriers affecting the export of American goods and services to foreign countries and barriers affecting the import of foreign goods and services into the U.S.
In keeping with U.S. obligations under the Convention on International Civil Aviation, it is TSA’s policy to comply with International Civil Aviation Organization (ICAO) Standards and Recommended Practices to the maximum extent practicable. TSA has determined that there are no ICAO Standards and Recommended Practices that correspond to the regulatory standards established by this final rule (FR). TSA has assessed the potential effect of this FR and has determined that it does not create barriers to international trade.
However, when TSA reviewed the impact of foreign carrier overflights, the conclusion is not clear. The right of airlines from one country to overfly another country in the course of traveling to the destination country is the first of the well known "freedoms of the air." This technical freedom has been engrained in international aviation since the Chicago Convention of 1944. How countries might react to the new conditions being placed on the fulfillment of this freedom is uncertain. International trade in travel and international shipping may be negatively impacted should foreign countries choose to respond in a retaliatory manner. One response by foreign carriers might be to avoid overflying the U.S. entirely, thereby lengthening flight routes and the costs of operation to those carriers. These reroutings would change airline costs and thus contribute to fare increases, which would affect trade between the departure and arrival countries, even though it would not directly affect trade involving the U.S. If the foreign carrier response is to reroute, it is not clear that such a change would eliminate all risks, since aircraft skirting the boundaries of U.S. airspace could be redirected into U.S. airspace by hijackers or terrorists.
Part 4: Unfunded Mandates Reform Act
The Unfunded Mandates Reform Act of 1995 (the Act), enacted as Public Law 104-4 on March 22, 1995, is intended, among other things, to curb the practice of imposing unfunded Federal mandates on State, local, and tribal governments. Title II of the Act requires each Federal agency to prepare a written statement assessing the effects of any Federal mandate in a proposed or final agency rule that may result in a $100 million or more expenditure (adjusted annually for inflation) in any one year by State, local, and tribal governments, in the aggregate, or by the private sector. This final rulemaking does not impose an unfunded mandate on State, local, or tribal governments, but it does impose an unfunded mandate on the private sector. The analysis required under Title II of the Act is satisfied within the analysis provided above.
1 Passport information is the following information from a passenger’s passport: (1) Passport number; (2) country of issuance; (3) expiration date; (4) gender; (5) full name. See § 1560.3.
2 Itinerary information is the following information about a covered flight: (1) Departure airport code; (2) aircraft operator; (3) departure date; (4) departure time; (5) arrival date; (6) scheduled arrival time; (7) arrival airport code; (8) flight number; (9) operating carrier (if available). For non-traveling individuals in the United States, the airport code for the sterile area to which the non-traveling individual seeks access. See § 1560.3.
3 49 CFR 1560.105(b)(2) and (3).
4 Secure Flight Program Privacy Impact Assessment, June 22, 2005, 70 FR 36320.
5 TSA anticipated that in many cases a passenger’s initial contact would be with an airline ticket agent. Thus, for simplicity, TSA refers throughout to the employee verifying passenger IDs as a ticket agent; however, this function could be performed by a variety of airline employees, including management or ground security coordinators.
6 TSA anticipated that in many cases a passenger’s initial contact would be with an airline ticket agent. Thus, for simplicity, TSA refers throughout to the employee verifying passenger IDs as a ticket agent; however, this function could be performed by a variety of airline employees, including management or ground security coordinators.
7 Table 9: Total Scheduled US Passenger Traffic, “FAA Aerospace Forecasts FY 2006 – 2017,” released February 2006. Available at <http://faa.gov/data_statistics/aviation/aerospace_forecasts/2006-2017/>.
8 Operating revenues for small certificated carriers were not available.
9 BTS TranStats Database Glossary. Available at <http://transtats.bts.gov/glossary.asp>. Accessed July 16, 2006.
10 Source and Accuracy Compendium: Form 41, Schedules T100 and T100(f) Air Carrier Data. Available at <http://www.bts.gov/programs/statistical_policy_and_research/source_and_accuracy_compendium/form41_schedule.html>. Accessed July 16, 2006.
11 BTS, supra note 4.
12 If it chooses, a covered airline could establish a separate data system exclusively for storing SFPDs and managing the airline’s interaction with Secure Flight. However, TSA consulted extensively with airlines as it developed Secure Flight, and to date no airline has indicated it would establish a separate airline system specifically for interacting with the Secure Flight system.
13 Both ARSs and GDSs are types of computer reservation systems. The principal difference between them is host ARSs only process reservations from an airline’s website or call center, whereas GDSs allow travel agents and the public to make reservations for a variety of travel services through a single interface.
14 CBP estimates indicate the carriers for whom TSA would take over watch list matching from CBP carry more than 95% of international commercial air traffic.
15 It is important to note that Secure Flight will not replace CBP’s AQQ system. While Secure Flight will conduct watch list matching for the largest international air carriers, CBP will continue to conduct watch list matching for many aircraft operators subject to APIS regulations that are not covered by this final rule.
16 Because of treaty agreements, Secure Flight would not cover overflights in which a covered foreign air carrier entered U.S. airspace while transiting two points within Canada or two points within Mexico.
17 Source: “ASTA Agency Profile: Member Demographics – Collected December/January 2006.” Available at <http://www.astanet.com/about/ASTA%20Agency%20Profile%202006.pdf>. Accessed July 13, 2006.
18 Source: “Upheaval in Travel Distribution: Impact on Consumers and Travel Agents,” Report to Congress and the President by the National Commission to Ensure Consumer Information and Choice in the Airline Industry, 2002: 22-27.
19 Source: Table: “Airline Expectations of Changing Business Mix.” Source: “Highlights from Travel Weekly’s 2004 Industry Segment Survey.” Available at <http://www.travelweekly.com/specialreports/survey2004/hl2.html>. Accessed July 13, 2006.
20 Source: “Supplier Overview: Anticipating Solid Sales for 2005.” Travel Weekly’s 2005 U.S. Travel Industry Survey. Available at <http://www.travelweekly.com/multimedia/TWSURVEY2005/seg_hl.htm>. Accessed July 14, 2006.
21 The BTS Origin and Destination Survey is a 10% sample of airline itineraries from reporting carriers. All 2004 reporting carriers were covered aircraft operators except one, representing 99.95% of submitted itineraries. In 2000, their lowest representation, covered carriers still represented 94.79% of submitted itineraries.
22 De Lollis, Barbara and Barbara Hansen, “Airlines Give Fliers Fewer Chances to Do the Bump,” USA Today, December 19, 2005. Available at <http://www.usatoday.com/money/biztravel/2005-12-19-bump-usat_x.htm>. Accessed May 16, 2006.
23 Since the Known Traveler Number, if implemented, could be entered into the same field as the Redress Number, TSA determined any additional time associated with collecting this number in the future would be within the estimated range of data collection times.
24 This business model also helps to explain why carriers in Group 4 may have enplanement and revenue totals comparable to carriers of other groups and yet were still selected for the web interface.
25 These databases are maintained by the Department of Homeland Security, Department of Defense, National Counterterrorism Center and Federal Bureau of Investigation.
26 U.S. Department of Transportation memorandum, Treatment of the Economic Value of a Statistical Life in Departmental Analyses. Office of the Secretary of Transportation, February 5, 2008.
27 Federal Aviation Administration. 2007. Economic Values for FAA Investment and Regulatory Decisions, A Guide. Prepared by GRA, Inc. December 31, 2004 (updated). Table 5-1. This table reports 2003 value estimates, and the 2003 estimate of $42.3 million was brought to 2006 values using the FAA recommended method described in the document in Section 9.6 (page 9-9), using the BLS producer price index series for civil aircraft, available in the producer price index values for commodities at http://stats.bls.gov/ppi/home.htm .
28 Regulatory Assessment & Final Regulatory Flexibility Analysis for the Final Rule, Passenger Manifests for commercial Aircraft Arriving in and Departing from the United States; Passenger and Crew Manifests for Commercial Vessels Departing from the United States. Table 13, page 36.
29 Thompson, Jr., William C. Comptroller, City of New York. “One Year Later: The Fiscal Impact of 9/11 on New York City.” September 4, 2002.
30 “Economic Consequences of a Nuclear Detonation in an Urban Area” undated DHS draft.
31 See Section 1.4.1 for an explanation of how TSA determined these carriers may implement AQQ.
32 See Section 1.4.1 for an explanation of how TSA determined these carriers may implement AQQ.
33 As noted in Section 1.4.1, TSA would not mandate how covered carriers would store or extract SFPD. However, covered carriers may choose to extract the SFPD from their reservation systems rather than establishing or using a separate system for storing SFPDs and interacting with Secure Flight. TSA has assumed for the purposes of this analysis that airlines would extract the information from their reservation systems.
34 Travel Agency Distribution Landscape, prepared by PhoCusWright for the American Society of Travel Agents (ASTA), Airlines Reporting Corporation (ARC), Cruise Lines International Association (CLIA), Performance Media Group, LLC, and others. April 2008.
35 Checkpoints are comprised of clusters of screening lanes. Screening lanes typically contain one magnetometer and one x-ray machine. TSA’s Performance and Results Information System (PARIS) system indicates that there were 805 checkpoints in March, 2007.
36 Based on TSA conversations with another Federal agency using mobile scanners.
37 U.S. Bureau of Labor Statistics wage for Protective Service Occupations (SOC: 33-9099), inflated to 2005 and adjusted to include benefits.
38 This information could be limited to a “red light/green light” confirmation, or could include portions of the Passenger Reservation Data necessary for comparison of the boarding pass to the passenger’s identification.
39 SSOLV verifies SSN data by responding that submitted data matches SSA data or it will indicate which part of the original transmission from the requesting party does not match SSA data. SSOLV does not send any data from the SSA database as a response.
40 This includes the 7.8 billion domestic enplanements from Table 1.4.1.a and half of the 1.1 billion passengers either coming to or leaving the U.S from Table 1.4.1.h. Only half of international passengers are used because TSA anticipates that boarding passes would not be verified in foreign airports. TSA notes that use of enplanements may slightly overstate the actual number of passengers passing through checkpoints and may thus slightly overstate costs.
41 U.S. Department of Justice, Office of the Inspector General Audit Division, Audit 05-34. “Review of the Terrorist Screening Center’s Efforts to Support the Secure Flight Program.” August 2005.
42 BTS data shows that Group 4 carriers represented only approximately 0.60% of total FY 2005 covered domestic carrier enplanements. Group 4 projected enplanements are presented in Table 1.4.2.c.
43 Small Business Administration. Table: “Small Business Size Standards matched to North American Industry Classification System.” Available at <http://www.sba.gov/size/sizetable2002.html>. Accessed May 4, 2006.
Note: The SBA size standard for travel agencies is based on “total revenues, excluding funds received in trust for an unaffiliated third party, such as bookings or sales subject to commissions. The commissions received are included as revenue.”
44 Small Business Administration. Table: “All Industries by NAICS codes, 2003.” See TXT file “2003” available at <http://www.sba.gov/advo/research/data.html>. Accessed May 6, 2006. Note: TSA used a threshold of $5 million because the SBA tables did not contain enough detail to only include agencies with revenues less than $3.5 million.
45 Small Business Administration. Table: “Small Business Size Standards matched to North American Industry Classification System.” Available at <http://www.sba.gov/size/sizetable2002.html>. Accessed May 4, 2006.
46 For more information, please see Section 1.4.1.
47 Since in some cases the reported revenue data is proprietary, TSA substituted an ID number in place of company names.
48 In cases for which annual revenues were not available, carrier filings of total annual sales were used as a proxy for revenue.
49 Small Business Administration. Table: “Small Business Size Standards matched to North American Industry Classification System.” Available at <http://www.sba.gov/size/sizetable2002.html>. Accessed May 4, 2006.
Note: The SBA size standard for travel agencies is based on “total revenues, excluding funds received in trust for an unaffiliated third party, such as bookings or sales subject to commissions. The commissions received are included as revenue.”
50 Small Business Administration. Table: “All Industries by NAICS codes, 2003.” See TXT file “2003” available at <http://www.sba.gov/advo/research/data.html>. Accessed May 6, 2006.
51 Commission Report, p. 114.
52 Ibid.
53 “End of Year Reporting and Settlement Results,” Airlines Reporting Corporation press release, December 2002, December 2003, December 2004, December 2005. Available at <http://www.arccorp.com/regist/news_sales_doc_stats.jsp>. Accessed May 12, 2006.
54 Small Business Administration. Table: “All Industries by NAICS codes, 2003.” See TXT file “2003” available at <http://www.sba.gov/advo/research/data.html>. Accessed May 6, 2006. Estimated receipts divided by number of firms, revenue class 0-99,999.
| File Type | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File Modified | 0000-00-00 |
| File Created | 2022-05-27 |
© 2026 OMB.report | Privacy Policy