Family report, MTW Family Report, MTW Expansion Family Report
Family Report, MTW Family Report, MTW Expansion Family Report
InterconnectionSecurityAgreementMTWApplicationUAT
Family report, MTW Family Report, MTW Expansion Family Report
OMB: 2577-0083
|
U.S. Department of Housing and Urban Development
Controlled Unclassified Information (CUI)
Interconnection Security Agreement (ISA) |
|
U.S. Department of Housing and Urban Development (HUD)
Office of the Chief Information Officer (OCIO)

Interconnection Security Agreement (ISA)
Between the U.S. Department of Housing and Urban Development (HUD)
and
‘Organization B’
January 29, 2021
Revisions Record
Version Number |
Date |
Description of Revision |
Section/Pages Affected |
1.0 |
1/22/2021 |
Draft of the ISA between HUD and Organization B, which is required to participate in testing that involves a system interconnection |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table of Contents
1. Interconnection Statement of Requirements 1
2. System Security Considerations 1
3. Points of Contact 3
4. Topological Drawing 4
5. Signatory Authority 6
The requirements for interconnection between the U.S. Department of Housing and Urban Development (HUD) and “Organization B” are for the express purpose of exchanging data between the MTW Expansion Application, owned by HUD, and "System B,” owned by Organization B. This ISA covers the Test environment; user acceptance testing (UAT) will be conducted in the Test environment. Organization B requires the use of HUD’s MTW Expansion Application data and Organization A requires the use of Organization B's "ABC database," as approved. This Agreement is between U.S Department of Housing and Urban Development (HUD), with its principal place of business at 451 7th Street S.W., Washington, DC 20410 and Organization B, with its principal place of business at <insert location, if applicable>.
General Information/Data Description. The interconnection between the MTW Expansion Application, owned by HUD, and System B, owned by Organization B, is a two-way path. The purpose of the interconnection is to exchange data between HUD’s MTW application and Organization B's System B for testing purposes.
Services Offered. This connection exchanges data between HUD's MTW Expansion application and Organization B's System B via a dedicated system to system connection. Organization B may also have users accessing the MTW Expansion application via user ID and password, which will be provisioned by HUD through the MTW Expansion application.
Security Measures. Each party must (i) implement and maintain all reasonable security measures appropriate including without limitation, technical, physical, administrative and organizational controls; (ii) implement and maintain industry standard systems and procedures for detecting, preventing and responding to attacks, intrusions, or other systems failures and regularly test or otherwise monitor the effectiveness of the safeguards’ key controls, systems, and procedures; (iii) designate an employee or employees to coordinate implementation and maintenance of its security measures; and (iv) identify reasonably foreseeable internal and external risks to the security, confidentiality and integrity data that could result in the unauthorized disclosure, misuse, alteration, destruction or other compromise of such data, and assess the sufficiency of any safeguards in place to control these risks. HUD systems are assessed and authorized in accordance with guidance from the National Institute of Standards and Technology (NIST), the Federal Information Security Modernization Act of 2014 (FISMA), and other federal standards. Organization B must self-certify that the security posture of the information system(s) covered by this ISA will also follow NIST, FISMA, and other federal guidance, including Federal Risk and Authorization Management (FedRAMP) requirements as applicable.
Data Sensitivity. In the Test environment, only dummy data / non-production data is allowed to be exchanged between HUD and Organization B.
User Community. All HUD users with access to the data received from Organization B are U.S. citizens with a valid and current HUD background investigation. All Organization B users with access to the data received from HUD are U.S. citizens with a valid and current Organization B background investigation.
Information Exchange Security. The security of the information being passed on this two-way connection is protected through the use of FIPS 140-2 validated encryption, which protects the data in-transit and at rest. The MTW Expansion application is hosted in the Salesforce Government Cloud (Gov Cloud), which has a FedRAMP Moderate Authority to Operate (ATO) and Department of Defense Impact Level 4 Provisional Authorization (PA). These authorizations enable organizations to transmit, process, and store sensitive information such as personally identifiable information (PII).
Gov Cloud also provides the following:
U.S. Data Centers: Customer Data is processed and stored solely within the continental U.S
U.S. Citizens: Operated and supported by screened U.S. citizens as applicable.
Salesforce’s approach to information security governance is structured around the ISO 27001/27002 framework and consistent with the requirements identified in NIST SP 800-53. All users are granted Role Based Access Control (RBAC) and the concept of least privilege is applied to support control and access to data elements within the system. The default user authentication mechanism for the Salesforce Government Cloud requests that a user provide a username and password (credentials) to establish a connection. The Salesforce Government Cloud does not use cookies to store confidential user and session information [AC-2, IA-2].
Trusted Behavior Expectations. HUD's system and users are expected to protect Organization B’s ABC database, and Organization B's system and users are expected to protect HUD's MTW Expansion application, in accordance with the Privacy Act and Trade Secrets Act (18 U.S. Code 1905) and the Unauthorized Access Act (18 U.S. Code 2701 and 2710).
Formal Security Policy. Policy documents that govern the protection of the data are covered by HUD OCIO's IT Security Policy Handbook and <Organization B's "YYY Policy>."
Incident Reporting. The party discovering a security incident will report it in accordance with HUD’s incident reporting procedures. In the case of <Organization B>, any security incident will be reported to the <information for Organization B>.
Audit Trail Responsibilities. Both parties are responsible for auditing application processes and user activities involving the interconnection. Activities that will be recorded include event type, date and time of event, user identification, workstation identification, success or failure of access attempts, and security actions taken by system administrators or security officers. Audit logs will be retained for one (1) year.
For all issues associated with this ISA, the established points of contact are as follows:
U.S. Department of Housing and Urban Development |
Organization B |
Authorizing Official (AO) Ashley Sheriff |
Authorizing Official (AO)
|
System Owner (SO) Matilda Chiu |
System Owner (SO)
|
Information System Security Officer (ISSO) Dallas Blair |
Information System Security Officer (ISSO) |
Project Manager (PM) Matilda Chiu |
Project Manager (PM)
|
Organization B will submit 50058 data to the MTW Expansion application either through the application, using a user ID and password created by HUD, or via a system to system connection between the Organization B’s system and HUD’s MTW Expansion application.
User access, log in directly to the application: Organization B must submit a user request form for all users who will need to directly access the application with a user login/ID. The form will include the Rules of Behavior, which each requested user must agree to. Once submitted, a user account will be created for the user. The user will also need to agree to the Rules of Behavior when logging into the system, which is posted on the login screen of the application.
System to system connection: After signing this ISA, Organization B will need to work with HUD to update Organization B’s system to connect to the appropriate end point and to establish a system account/ID. Organization B will need to designate individuals that will be associated with the system account/ID and will be responsible for the use of the system account.
After the 50058 data is submitted, the MTW Expansion application will validate the data and provide the submission status and any errors back, either via the MTW Expansion application or through the system connection.
The topological diagram and business process flow are shown below.
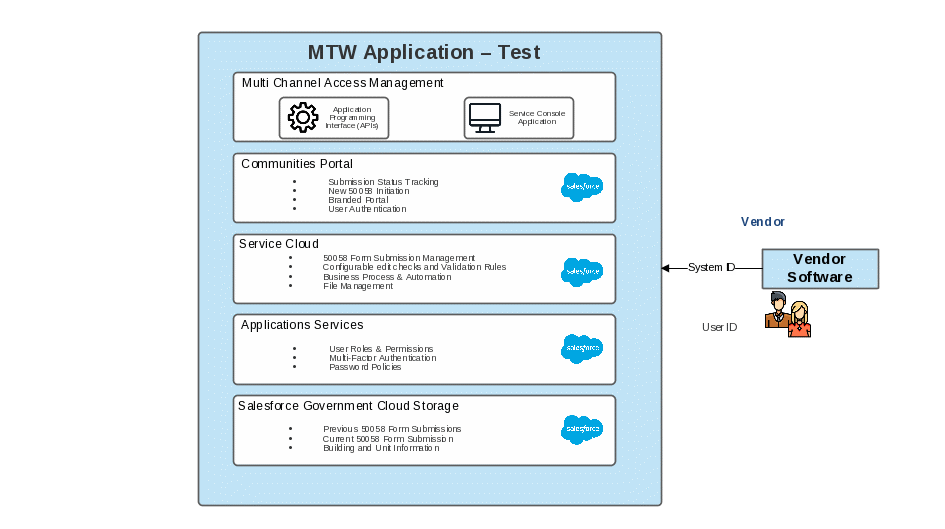
Topological Diagram: Connection to the MTW Test Environment
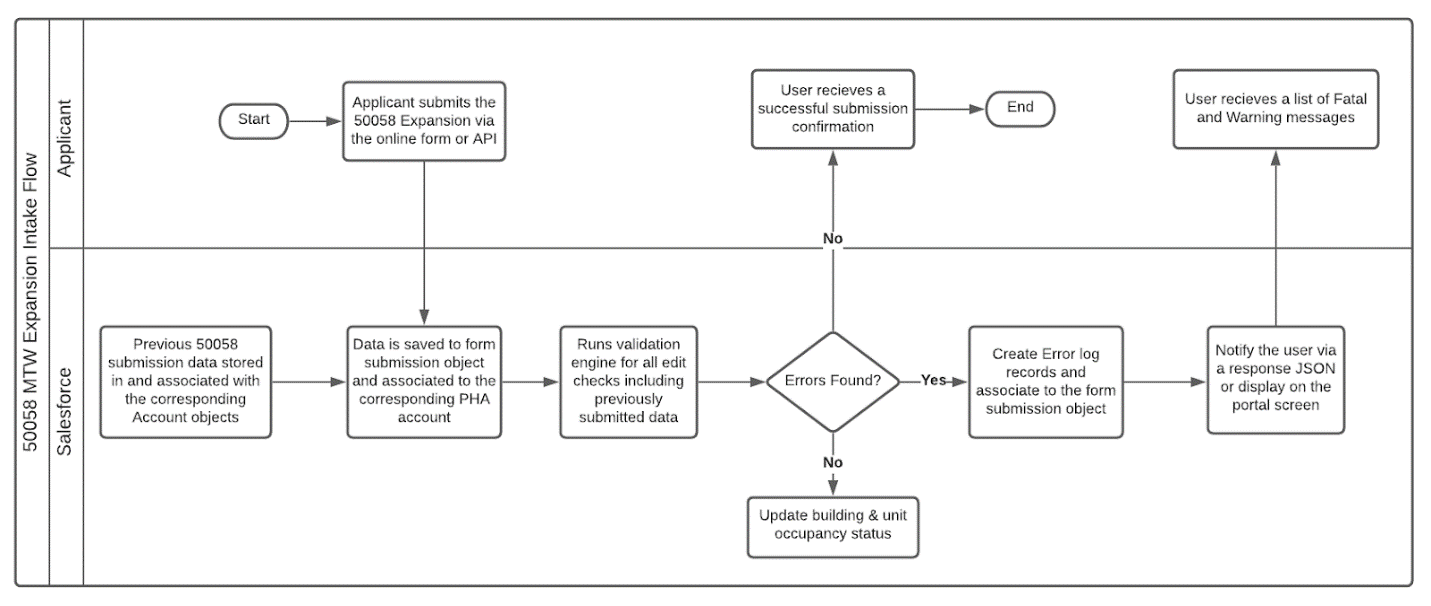
Business Process Flow
This ISA is valid for one (1) year after the last date on either signature below. At that time it will be updated, reviewed, and reauthorized. Either party may terminate this agreement upon 30 days’ advanced notice in writing or in the event of a security incident that necessitates an immediate response.
MTW Expansion Application (System B)
Matilda Chiu System Owner Name
System Owner Title
______________________________ ________________________________
(Signature Date) (Signature Date)
Hun Kim CISO Name
Chief Information Security Officer Chief Information Security Officer
______________________________ ________________________________
(Signature Date) (Signature Date)
Christopher Webber CIO Name
Chief Information Officer (Acting) Chief Information Officer
______________________________ ________________________________
(Signature Date) (Signature Date)
| File Type | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| Author | Alexander Bemish |
| File Modified | 0000-00-00 |
| File Created | 2022-08-08 |
© 2026 OMB.report | Privacy Policy
