National Institute of Standards and Technology In-depth Interview: Perceptions of Online Security
Generic Clearance for Usability Data Collections
0693-0043 - NIST In-depth Interview - Perceptions of Online Security Questionnaire
National Institute of Standards and Technology In-depth Interview: Perceptions of Online Security
OMB: 0693-0043
NIST In-depth Interview: Perceptions of Online Security
Interview Questionnaire
Have you ever received any type of computer security training or education?
If Yes:
How often
What type (online, classroom)
Who provided the training?
Was it beneficial and were you able to understand the content?
Did you change your behavior after the training?
IF YES – What information accounted for that change?
Self-assessment of security knowledge and awareness.
Please provide an assessment of your knowledge of security from 1-10. The following scale will be used:
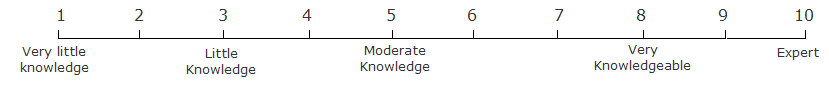
Definition of Security
Please describe what you think about or how you define or describe online security.
In general, what do you think you are protecting and who/what are you protecting that from?
If you are using your computer at home – what do you think you are protecting and who/what are you protecting it from?
If you are using your work computer – what do you think you are protecting and who/what are you protecting it from?
More specifically:
If I said – What do you think about security with regards to:
Your email(s) account(s)
What is it that you are protecting?
Who do you think wants the information and what would they do with it?
Online shopping
What is it that you are protecting?
Who do you think wants the information and what would they do with it?
Online banking or bill paying
What is it that you are protecting?
Who do you think wants the information and what would they do with it?
Social websites
What is it that you are protecting?
Who do you think wants the information and what would they do with it?
Administration and configuration
What security related issues can happen and how?
Security Icons
Have you ever seen these security icons/trust marks before (please circle icons you have seen before)?

For the following security terms, please tell me how familiar you are with the term (1 Not familiar at all 2 Somewhat Familiar 3 Very familiar).
Authenticate
Bots
Browser Cookies
Cybercrime
Card skimmers
Denial of service
DNS Spoofing
Firewall
Keylogger
HTTP/HTTPS
Phishing
Spyware/ant-spyware
Spoofing
SSL
Virus
Worm
NOTE: This questionnaire contains collection of information requirements subject to the Paperwork Reduction Act (PRA). Notwithstanding any other provision of the law, no person is required to respond to, nor shall any person be subject to a penalty for failure to comply with, a collection of information subject to the requirements of the PRA, unless that collection of information displays a currently valid OMB Control Number. The estimated response time for this questionnaire is 60 minutes. The response time includes the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information." Send comments regarding this estimate or any other aspects of this collection of information, including suggestions for reducing the length of this questionnaire, to the National Institute of Standards and Technology, Attn., Mary Theofanos, [email protected] , 301-975-5889. The OMB Control No. is 0693-0043, which expires on 10/31/2012.
| File Type | application/msword |
| Author | dyonder |
| Last Modified By | dyonder |
| File Modified | 2010-08-11 |
| File Created | 2010-08-11 |
© 2026 OMB.report | Privacy Policy