Joint Services Support (JSS) System
Joint Services Support (JSS) System
JSS - collection instruments - updated Nov 10 2014 by ns.DOCX
Joint Services Support (JSS) System
OMB: 0704-0537
Joint
Services Support (JSS) System
PII Collection Instruments
Table of Contents
3 Volunteer Activity Hours Form 6
4 Civilian Employer Information (CEI) Form 7
5.1.3 Acceptable Use Policy 13
5.2 Civilian Employer Information (CEI) Form 16
5.2.1 Privacy Act Statement 16
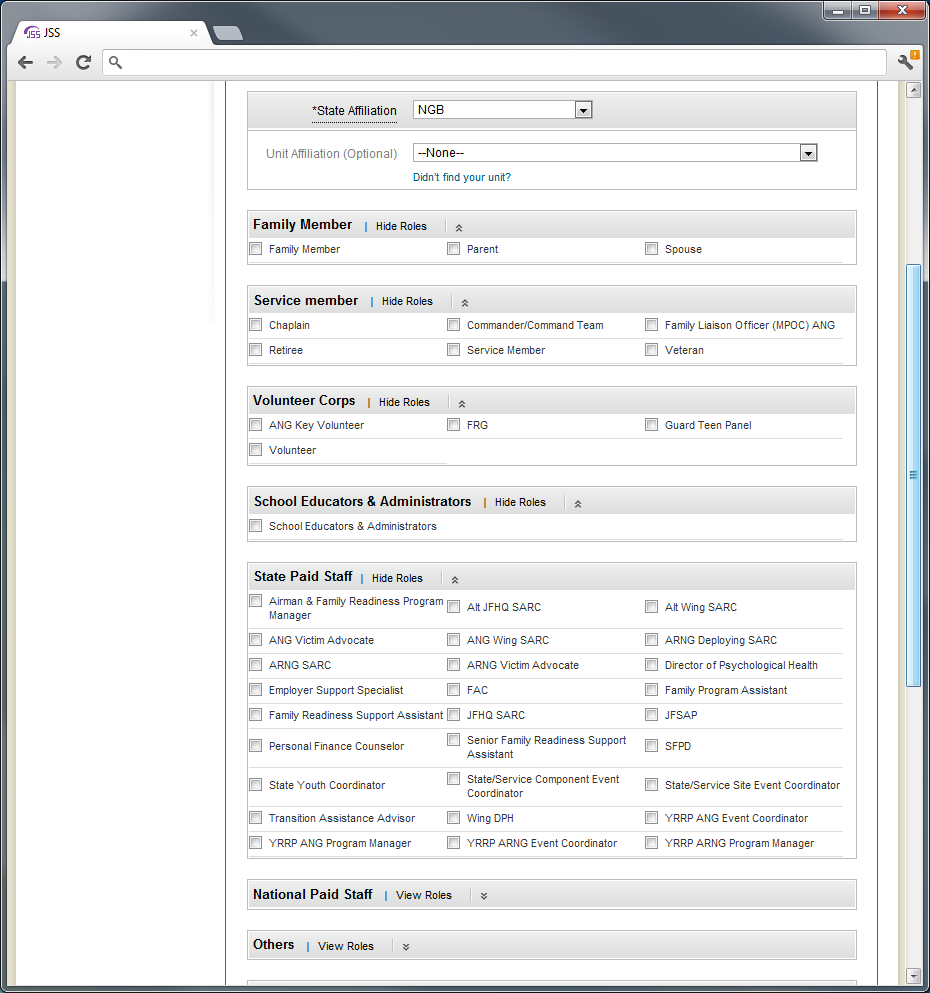
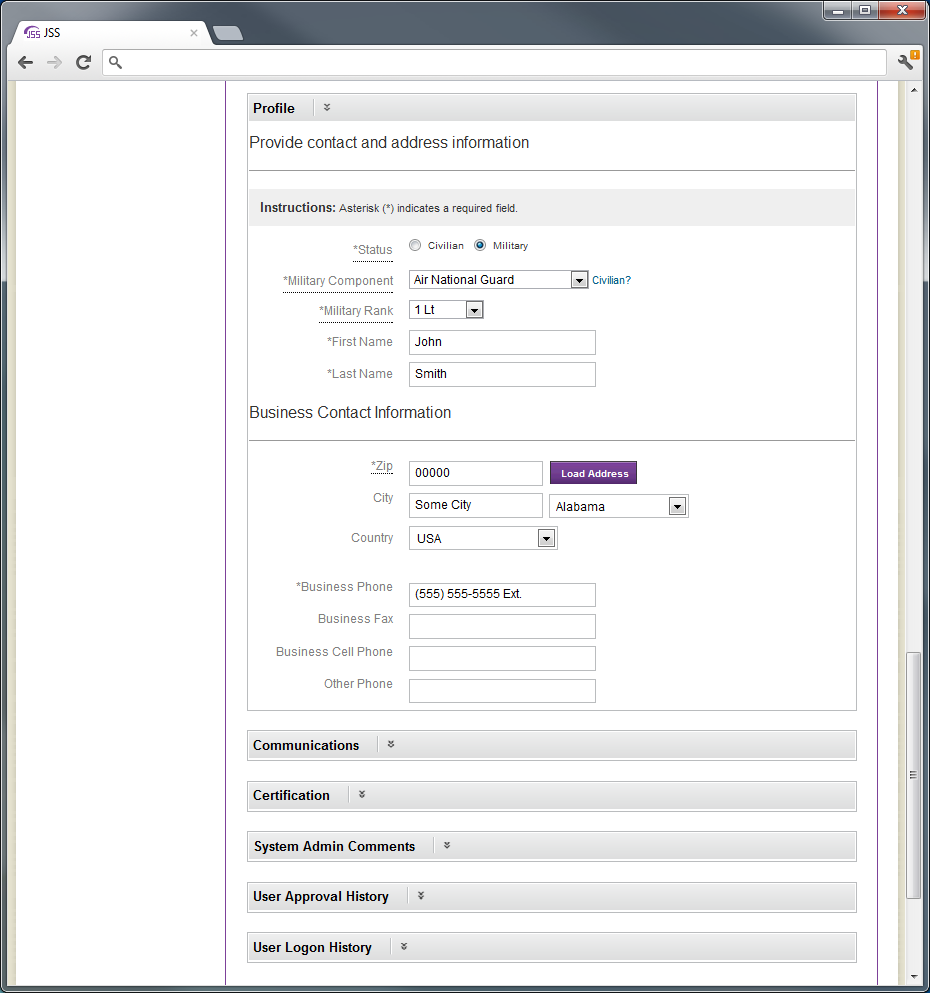
The user profile form collects: state (affiliated with), unit, system-role, component, salutation/rank, name, and contact information (zip, city, state, country, phone, fax and email). If the registering user selects family member or volunteer system-role, home contact information is collected. Otherwise business contact information is collected. Not all fields are mandatory.
Note, OMB Control Number and Expiration Date: TBD

Refer to the appendix for Privacy Policy, Terms of Use, and Acceptable Use Policy.
The event registration form collects information from users interested in attending events hosted by NGB J1 programs, across all Guard and Reserve components. The registration form collects component, salutation/rank, name, state (affiliated with), contact email, system-role and category (Attendee, VIP, Support Staff). The form may be customized by event staff to include additional data fields.
YRRP event registration form collects information in support of the Yellow Ribbon Reintegration Program mandate of Congress.
Note, OMB Control Number and Expiration Date: TBD
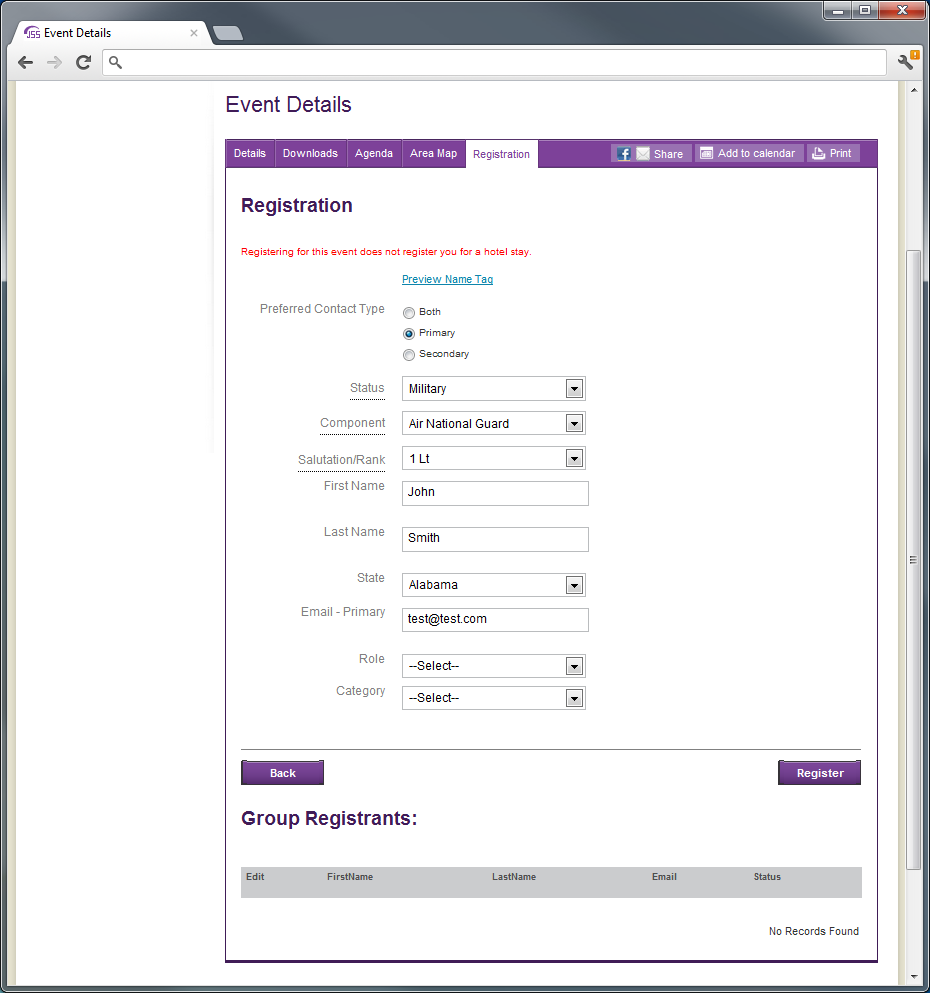
Collection of Social Security Number (SSN) and Date of Birth (DoB) from Service members (only) within event registration form is planned in the future – currently not in place. SSNs and DOBs will be required by Defense Manpower Data Center (DMDC) to validate Service member information to determine program eligibility.
Volunteer activities and associated hours are collected from volunteers.
Note, OMB Control Number and Expiration Date: TBD

This is a planned collection – currently not in place.
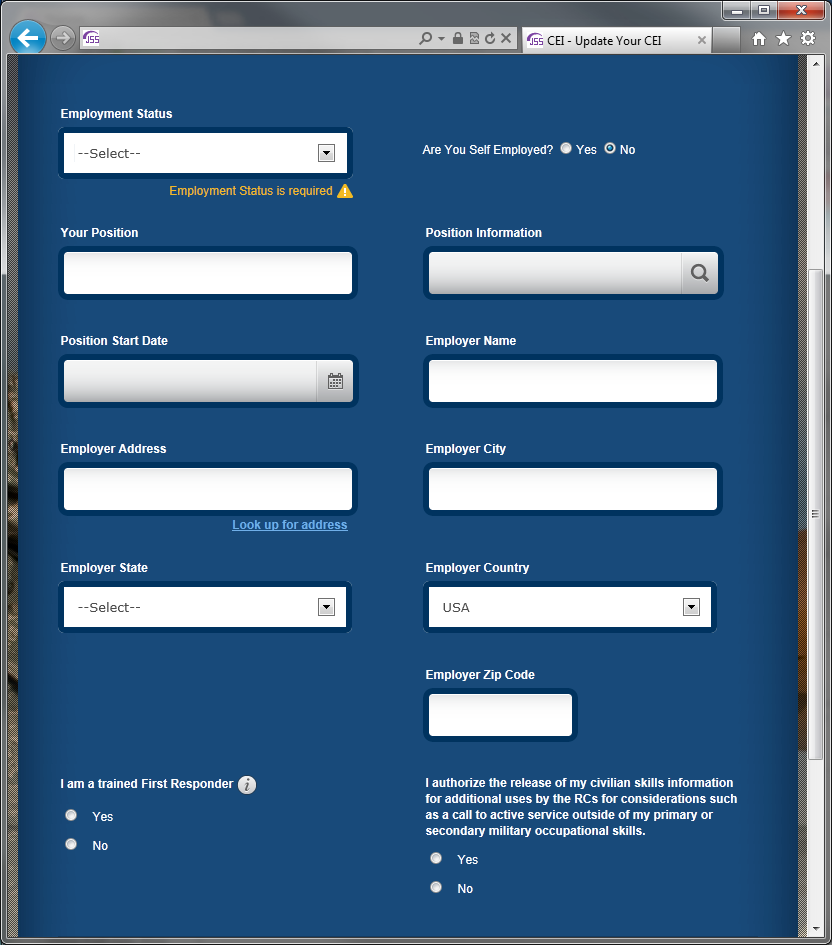
Users who will be required to submit their CEI (Air National Guard, Army National Guard and Air Force Reserve Service members) must provide their social security number (SSN) and Date of Birth (DoB) one-time only. All subsequent visits to update CEI will not require SSN and DoB, instead, JSS login information is used to authenticate user.
CEI will be collected in support of Uniformed Services Employment and Reemployment Rights Act (USERRA).
SSN and DoB will be collected to meet Defense Manpower Data Center (DMDC) requirement to report collected data to DMDC.
Note, OMB Control Number and Expiration Date: TBD
Refer to the appendix for Privacy Act Statement.
This privacy policy statement has been developed to reflect our commitment to our users' privacy.
Why We Collect Your Information
In order for us to provide you with access to the full breadth of functionality on this website, we ask that you create a user profile, which consists of your Name, location, contact information, role and other details that allow us to communicate with you effectively and provide information relevant to you. We do not sell your information to third-parties outside of the organization. In addition, as with most web servers on the World Wide Web today, our server automatically logs information about the environment of each visitor to a website. This type of data-collection is standard, and consists of information that is not personally-identifiable, such as Browser type, Operating System, page response times, and information for statistical analysis to measure visitor interest areas and to provide you with the best experience possible when browsing our website.
How We Collect Information
Below are some of the ways in which information may be collected online and how it may be used.
IP Address Collection
Our Web servers receive and temporarily record IP addresses from all users because this information is automatically reported by their browsers each time they access any JSS web page. We might use IP addresses for the following purposes:Diagnosing service or technical problems reported by our users, our technical staff, or engineers affiliated with a specific IP-range-providing web company or ISP.
Determining general geographic area (region/locality) of IP address to serve relevant content and filter out irrelevant content for our users.
Estimate number of users visiting JSS from different countries/regions/localities.
Use of Cookies
Our Web site may use cookies to keep track of the user’s session for the purposes of enhancing the user experience. Cookies are small text files that are stored on a visitor's browser and are used for keeping track of settings or data for a particular Web site. Among other things, we may use cookies to deliver content specific to our users' interests.Aggregate Information
Aggregate information about which pages visitors access or visit (for example, links within the site, courses, etc.) is only used for internal review as we continue to improve our Web site.User Profile
A user profile is created with information that you provide to us and is used for authentication when you login to the site. It can also be used for a) verifying your identity should you wish to contact us, b) marketing information useful to the user, and c) displaying information on the site that is most relevant to the user.
Information Actively Provided by Our Visitors
There are several places where users may choose to provide personally identifiable information about themselves or others. Unless we tell you otherwise, we will use the information for the purpose the information was provided.
How You Can Access or Correct Your Information
You may review your profile online, have it deleted, and/or withdraw permission for its continued use by contacting us (see Contact Us section)
To protect your privacy and security, we will also take reasonable steps to verify your identity before granting access or making corrections.
Links
Our site contains links to other sites. We are not responsible for the privacy practices or the content of other such sites. We make best efforts to screen all sites accessible from us to ensure that they comply with the standards set by us.
Discussion Forums
We host discussion forums which are available for your use. You should NEVER disclose any personal information. You should not enter any forum on the Internet that requires you to disclose any personal information prior to entering. The forums are monitored by our staff regularly.
Online Surveys
Our occasional online surveys are voluntary and anonymous; they are used to improve our site and better serve our clients. When demographic information is collected, we do not ask for any personally identifying information.
Security
This site has security measures in place to protect the loss, misuse, and alteration of the information under our control.
Children’s Guidelines
We caution children that they should not divulge their personal information on the Web. Our forums are moderated, and while our moderators cannot prevent children from divulging personal information, they use their best efforts to ensure that personal information is not divulged. In compliance with CHILDREN’S ONLINE PRIVACY PROTECTION ACT (COPPA), we not allow children of age 12 and under to register online. If during routine audits, such an account is found, appropriate measures are taken to remove from the system immediately.
Acceptance of policy
By visiting our site, you accept the terms and conditions of this Privacy Policy, and consent to our collection, storage and use of your information, as described in this Privacy Policy and elsewhere in our Site. We reserve the right to modify this Privacy Policy at any time and from time to time. Your continued use of the site after we either personally notify you or generally post such changes will constitute your acceptance of those changes.
Contacting Us
If you have any questions about this privacy statement, the practices of this site, or your dealings with National Guard Bureau J-1's Joint Services Support (JSS) sites, you can contact us by sending an email to [email protected] or by regular mail at the following address:
NGB J-1 Office
111 S. George
Mason Drive, Bldg 2,
Arlington, Virginia 22204
We provide this Web site (the “Site”) subject to the following terms and conditions (the “Terms”). By accessing this Site, you agree to these Terms. We reserve the right to change the Terms at any time by updating this posting, and use of this Site following any such changes shall constitute acceptance of such changes.
Copyright & Trademarks:
This Site and all the Contents are the exclusive property of National Guard Bureau J-1 or its licensors, and the trademarks, service marks, designs, logos and other intellectual property displayed on this Site (collectively, the “Trademarks”) are the registered and unregistered Trademarks of National Guard Bureau J-1 or its licensors. The Site, the Contents and the Trademarks are protected pursuant to U.S. and international copyright and trademark laws. The content of this site, including but not limited to the text and images herein and their arrangements, unless otherwise noted, are Copyright © 2006. All Rights Reserved. All trademarks referred to are the property of their respective owners.
Grant of License:
National Guard Bureau J-1 grants you a non-exclusive, non-transferable limited license to access, download, display and print copies of the content displayed on the Site (the “Content”) on any computer for business use only, subject to the provisions of this Agreement, and provided that you retain all copyright and other proprietary notices displayed on the Content. You may not otherwise reproduce, modify, distribute, republish, download, upload, disclose or commercially exploit the Content without the prior written consent of National Guard Bureau J-1.
Forums and Public Communication:
You agree that you will not post or publish on this Site any materials that:
are threatening, libelous, defamatory, obscene, pornographic and/or profane;
constitute or encourage conduct that would constitute a criminal offence or give rise to civil liability or otherwise violate any law;
infringe the intellectual property, privacy or other rights of any third party;
contain advertising or false or misleading statements; or
contain a computer virus or other disruptive or destructive components.
National Guard Bureau J-1 does not regularly review information posted to the Site and is not responsible for such information. National Guard Bureau J-1 reserves the right to refuse to post and the right to remove any information from this Site, in whole or in part, at its sole discretion, at any time, without notice. Except as may be otherwise provided in written agreements between National Guard Bureau J-1 and the users of the Site specified therein, you acknowledge and agree that National Guard Bureau J-1 shall own and have the unrestricted right to use, publish and otherwise exploit any and all information that you post or otherwise publish on the Site, and you hereby waive any claims against National Guard Bureau J-1 for any alleged or actual infringements of any rights of privacy or publicity, moral rights, or rights of attribution in connection with the use and publication by National Guard Bureau J-1 of such submissions.
Notices of Infringement:
If you believe that any portion of your intellectual property right has been infringed by any submissions posted on the Site, please contact us, giving a written statement that identifies the right or rights claimed to have been infringed and the infringing materials, explains why you believe, in good faith, that the exercise of the intellectual property right is unauthorized, confirms that you believe your statement to be accurate, contains the signature of the intellectual property right owner, and provides your name and contact information. Subject to an opportunity to review such statement, National Guard Bureau J-1 will remove any posted submission that infringes the copyright or other intellectual property right of any person under U.S. or other applicable law. National Guard Bureau J-1 reserves the right to prohibit persons who repeatedly submit infringing or unlawful material from posting further submissions.
Termination of Site and Site Access:
We reserve the right to change the contents of this site or to discontinue it at any time, as well as the right to deny access to the site to any person whom we have reasonable grounds to believe may be using the site for an unlawful or unauthorized purpose or in a manner that may harm us.
Disclaimers:
THIS SITE AND THE CONTENT ARE PROVIDED "AS IS" WITH NO REPRESENTATIONS OR WARRANTIES OF ANY KIND, WHETHER EXPRESS OR IMPLIED, INCLUDING WITHOUT LIMITATION IMPLIED WARRANTIES OF MERCHANTABILITY, TITLE, NON-INFRINGEMENT, AND FITNESS FOR A PARTICULAR PURPOSE. National Guard Bureau J-1 IS NOT HEREIN ENGAGED IN RENDERING PROFESSIONAL ADVICE AND SERVICES TO YOU. National Guard Bureau J-1 SHALL HAVE NO RESPONSIBILITY OR LIABILITY WITH RESPECT TO ANY INFORMATION PUBLISHED ON LINKED WEB SITES, CONTAINED IN ANY USER SUBMISSIONS PUBLISHED ON THE SITE, OR PROVIDED BY THIRD PARTIES. National Guard Bureau J-1 MAKES NO REPRESENTATIONS OR WARRANTIES WHATSOEVER AS TO THE OWNERSHIP, ACCURACY OR COMPLETENESS OF THE CONTENT OR THAT THIS SITE WILL OPERATE WITHOUT INTERRUPTION.
Liability:
TO THE FULLEST EXTENT PERMITTED BY APPLICABLE LAWS, IN NO EVENT SHALL National Guard Bureau J-1 OR ITS THIRD-PARTY CONTENT PROVIDERS BE LIABLE FOR ANY DAMAGES OR ANY KIND, INCLUDING WITHOUT LIMITATION ANY DIRECT, INDIRECT, COMPENSATORY, INCIDENTAL, CONSEQUENTIAL, SPECIAL, EXEMPLARY, PUNITIVE OR OTHER DAMAGES, OR FOR LOST REVENUES OR PROFITS, EVEN IF National Guard Bureau J-1 HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES OR LOSSES, ARISING OUT OF OR RELATING IN ANY WAY TO THIS SITE, THE CONTENT, OR THE USE OF THIS SITE.
By accepting this document, you acknowledge and consent that when you access Department of Defense (DoD) information systems:
You are accessing a U.S. Government (USG) information system (IS) (which includes any device attached to this information system) that is provided for U.S. Government authorized use only.
You consent to the following conditions:
The U.S. Government routinely intercepts and monitors communications on this information system for purposes including, but not limited to, penetration testing, communications security (COMSEC) monitoring, network operations and defense, personnel misconduct (PM), law enforcement (LE), and counterintelligence (CI) investigations.
At any time, the U.S. Government may inspect and seize data stored on this information system.
Communications using, or data stored on, this information system are not private, are subject to routine monitoring, interception, and search, and may be disclosed or used for any U.S. Government-authorized purpose.
This information system includes security measures (e.g., authentication and access controls) to protect U.S. Government interests--not for your personal benefit or privacy.
Notwithstanding the above, using an information system does not constitute consent to personnel misconduct, law enforcement, or counterintelligence investigative searching or monitoring of the content of privileged communications or data (including work product) that are related to personal representation or services by attorneys, psychotherapists, or clergy, and their assistants. Under these circumstances, such communications and work product are private and confidential, as further explained below:
Nothing in this User Agreement shall be interpreted to limit the user's consent to, or in any other way restrict or affect, any U.S. Government actions for purposes of network administration, operation, protection, or defense, or for communications security. This includes all communications and data on an information system, regardless of any applicable privilege or confidentiality.
The user consents to interception/capture and seizure of ALL communications and data for any authorized purpose (including personnel misconduct, law enforcement, or counterintelligence investigation). However, consent to interception/capture or seizure of communications and data is not consent to the use of privileged communications or data for personnel misconduct, law enforcement, or counterintelligence investigation against any party and does not negate any applicable privilege or confidentiality that otherwise applies.
Whether any particular communication or data qualifies for the protection of a privilege, or is covered by a duty of confidentiality, is determined in accordance with established legal standards and DoD policy. Users are strongly encouraged to seek personal legal counsel on such matters prior to using an information system if the user intends to rely on the protections of a privilege or confidentiality.
Users should take reasonable steps to identify such communications or data that the user asserts are protected by any such privilege or confidentiality. However, the user's identification or assertion of a privilege or confidentiality is not sufficient to create such protection where none exists under established legal standards and DoD policy.
A user's failure to take reasonable steps to identify such communications or data as privileged or confidential does not waive the privilege or confidentiality if such protections otherwise exist under established legal standards and DoD policy. However, in such cases the U.S. Government is authorized to take reasonable actions to identify such communication or data as being subject to a privilege or confidentiality, and such actions do not negate any applicable privilege or confidentiality.
These conditions preserve the confidentiality of the communication or data, and the legal protections regarding the use and disclosure of privileged information, and thus such communications and data are private and confidential. Further, the U.S. Government shall take all reasonable measures to protect the content of captured/seized privileged communications and data to ensure they are appropriately protected.
In cases when the user has consented to content searching or monitoring of communications or data for personnel misconduct, law enforcement, or counterintelligence investigative searching, (i.e., for all communications and data other than privileged communications or data that are related to personal representation or services by attorneys, psychotherapists, or clergy, and their assistants), the U.S. Government may, solely at its discretion and in accordance with DoD policy, elect to apply a privilege or other restriction on the U.S. Government's otherwise-authorized use or disclosure of such information.
All of the above conditions apply regardless of whether the access or use of an information system includes the display of a Notice and Consent Banner ("banner"). When a banner is used, the banner functions to remind the user of the conditions that are set forth in this User Agreement, regardless of whether the banner describes these conditions in full detail or provides a summary of such conditions, and regardless of whether the banner expressly references this User Agreement.
As a user of an information system, I will adhere to the following security rules
I will use Army information systems (computers, systems, and networks) only for authorized purposes.
I will not try to access data or use operating systems or programs, except as specifically authorized.
I know I will be issued a user identifier (user ID) and a password to authenticate my JSS account. After receiving them—
I will not allow anyone else to have or use my password. If I know that my password is compromised, I will report to my JSS Webmaster for a new one.
I will not run “sniffers” (utilities used to monitor network traffic, commonly used to Spy on other network users and attempt to collect their passwords) or any hacker-related software on my GC, Government IT system, or network.
If I observe anything on the system I am using that indicates inadequate security, I will immediately notify the site Webmaster. I know what constitutes a security incident and know that I must immediately report such incidents to the Webmaster
I will comply with security guidance issued by my SA and IASO.
I know that my actions as a user can greatly affect the security of the system and that my signature on this agreement indicates that I understand my responsibility as a user requires that I adhere to regulatory guidance.
I know I am subject to disciplinary action if I violate DOD computer policy. For U.S. personnel, this means that if I fail to comply with this policy, I may be subject to adverse administrative action or punishment under Article 92 of the Uniform Code of Military Justice (UCMJ). If I am not subject to the UCMJ, I may be subject to adverse action under the United States Code or Code of Federal Regulations.
Acknowledgement: I have read the above requirements regarding use of JSS access systems. I understand my responsibilities regarding these systems and the information contained in them.
Data Collected
AUTHORITY: 38 U.S.C. 4333; 10 U.S.C. 10149, 12302; EO 9397
PRINCIPAL PURPOSE: To facilitate the interaction and communication between civilian employers and the Department of Defense (DoD) for purposes of informing employers of members of the Ready Reserve of their rights, benefits, and obligations under the Uniformed Services Employment and Reemployment Rights Act (USERRA) codified as Chapter 43 of 38 U.S.C., as well as provide the Department of Defense with information necessary to promulgate policies that enhance employer support to the Guard and Reserve under (Section 4333 of 38 U.S.C.). To ensure that members having critical civilian skills are not retained in the Ready Reserve in numbers beyond what the Department needs for those skills (Section 10149 of 10 U.S.C.). To assist the Department in effectively giving consideration to civilian employment necessary to maintain national health, safety and interest when considering members for recall (Section 12302 of 10 U.S.C.). Your social security number (SSN) and birth date will be used solely for the purpose of verifying your identity. To ensure that appropriate consideration is given to current employment-related information when pre-mobilization planning is conducted.
ROUTINE USES: To civilian employers of Ready Reservists for purposes of informing such employers of the rights, benefits, and obligations under the Uniformed Services Employment and Reemployment Rights Act. To ensure that members having critical civilian skills are not retained in the Ready Reserve in numbers beyond what the Department needs for those skills (Section 10149 of 10 U.S.C.). And to assist the Department to effectively give consideration to civilian employment necessary to maintain national health, safety and interest when considering members for recall (Section 12302 of 10 U.S.C.).
DISCLOSURE: Mandatory. In order to verify the requested information required, personnel are required to also provide their social security number and date of birth. Failure or refusal to provide employment-related information or providing false employment-related information may result in administrative action or punishment under Article 92 (dereliction of duty) and/or Article 107(false official statement), Uniform Code of Military Justice (SSN and birth date only: Voluntary).
Active Guard Reserve Information
AGR personnel are not required to provide Military employment information. However, if you currently have a Part Time Position, a Specified Volunteer Position or you are a student - please provide the relevant information.
Warning Notice and Consent to Monitor
YOU ARE ACCESSING A U.S. GOVERNMENT (USG) INFORMATION SYSTEM (IS) THAT IS PROVIDED FOR USG-AUTHORIZED USE ONLY. By using this IS (which includes any device attached to this IS), you consent to the following conditions: The USG routinely intercepts and monitors communications on this IS for purposes including, but not limited to, penetration testing, COMSEC monitoring, network operations and defense, personnel misconduct (PM), law enforcement (LE), and counterintelligence (CI) investigations. At any time, the USG may inspect and seize data stored on this IS. Communications using, or data stored on, this IS are not private, are subject to routine monitoring, interception, and search, and may be disclosed or used for any USG-authorized purpose. This IS includes security measures (e.g., authentication and access controls) to protect USG interests--not for your personal benefit or privacy. Notwithstanding the above, using this IS does not constitute consent to PM, LE, or CI investigative searching or monitoring of the content of privileged communications, or work product, related to personal representation or services by attorneys, psychotherapists, or clergy, and their assistants. Such communications and work product are private and confidential. See Terms of Use, and Privacy Policy for details.
Use of this DoD computer system, authorized or unauthorized, constitutes consent to monitoring of this system. Unauthorized use may subject you to criminal prosecution. Evidence of unauthorized use collected during monitoring may be used for administrative, criminal, or other adverse action. Use of this system constitutes consent to monitoring for these purposes.
AUTHORIZED USER
This CEI web site is for the sole use of the individual Service member.
IF YOU ARE NOT AN AUTHORIZED USER, PLEASE EXIT IMMEDIATELY.
| File Type | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| Author | Nawed Shaikh |
| File Modified | 0000-00-00 |
| File Created | 2021-01-25 |
© 2026 OMB.report | Privacy Policy