Rg 5.62, Physical Security Event Notifications, Reports, And Records
RG 5.62, PHYSICAL SECURITY EVENT NOTIFICATIONS, REPORTS, AND RECORDS.docx
Information Collections Contained in 10 CFR Part 73, Enhanced Weapons, Firearms Background Checks, and Security Event Notifications Final Rule
RG 5.62, PHYSICAL SECURITY EVENT NOTIFICATIONS, REPORTS, AND RECORDS
OMB: 3150-0253
U.S. NUCLEAR REGULATORY COMMISSION |
||
|
REGULATORY GUIDE 5.62, REVISION 2 |
|
Issue Date: April 2022 Technical Lead: P. Brochman
|
||
PHYSICAL SECURITY EVENT NOTIFICATIONS,
REPORTS, AND RECORDS
A. INTRODUCTION
Purpose
This regulatory guide (RG) describes methods and procedures that the staff of the U.S. Nuclear Regulatory Commission (NRC) considers acceptable for use by licensees to comply with NRC regulations for implementing the provisions of Title 10 of the Code of Federal Regulations (10 CFR) Part 73, “Physical Protection of Plants and Materials” (Ref. 1).
Applicability
This RG applies to NRC licensees and Agreement State licensees who are subject to the provisions of 10 CFR 73.1200, “Notification of physical security events,” 10 CFR 73.1205, “Written follow-up reports of physical security events,” and 10 CFR 73.1210, “Recordkeeping of physical security events.” This includes licensees of facilities licensed under both 10 CFR Part 50, “Domestic Licensing of Production and Utilization Facilities,” (Ref. 2) and 10 CFR Part 52, “Licenses, Certifications, and Approvals for Nuclear Power Plants” (Ref. 3). This RG also applies to licensees possessing special nuclear material licensed under 10 CFR Part 70, “Domestic Licensing of Special Nuclear Material,” (Ref. 4) and licensees of radioactive waste storage facilities licensed under 10 CFR Part 72, “Licensing Requirements for the Independent Storage of Spent Nuclear Fuel and High-Level Radioactive Waste, and Reactor-Related Greater Than Class C Waste” (Ref. 5). Moreover, this RG also applies to licensees transporting certain types of special nuclear material and radioactive waste. A detailed discussion of the applicability of the specific provisions of 10 CFR 73.1200, 10 CFR 73.1205, and 10 CFR 73.1210 to licensees who are subject to 10 CFR Part 50, Part 52, Part 70, or Part 72 is found in this RG’s section B, “Discussion,” under the subsection “Applicability to Specific Facilities, Materials, and Shipping Activities” and the subsection “Applicability to Agreement State Facilities, Materials, and Shipping Activities.”
Applicable Regulations
10 CFR Part 73 requires licensees to establish and maintain a physical protection system which will have capabilities for the protection of special nuclear material (SNM) at fixed sites and in transit and of the plants or facilities in which SNM is used. This includes production and utilization facilities, including both operating and decommissioning production rectors, power reactors, non-power reactors, and other non-power production and utilization facilities. It also includes facilities possessing or transportation activities involving strategic special nuclear material (SSNM), SNM, spent nuclear fuel (SNF), and high-level radioactive waste (HLW).
10 CFR 73.15, “Authorization for use of enhanced weapons and preemption of firearms laws,” designates the classes of facilities, radioactive materials undergoing transport, and other property to which either stand-alone preemption authority or combined preemption and enhanced weapons authority,1 and contains the requirements for obtaining, possessing, and terminating either authority. These requirements apply only to licensees who voluntarily apply for such authority under Section 161A of the Atomic Energy Act of 1954 (AEA), as amended (Ref. 6).
10 CFR 73.21, “Protection of Safeguards Information: Performance Requirements,” requires licensees to ensure protection against the unauthorized disclosure of safeguards information (SGI).
10 CFR 73.22, “Protection of Safeguards Information: Specific Requirements,” requires licensees to create, store, handle, and transmit SGI in accordance with specific requirements.
10 CFR 73.67, “Licensee fixed site and in-transit requirements for the physical protection of special nuclear material of moderate and low strategic significance,” requires licensees to establish and maintain a physical protection system to minimize the unauthorized removal of SNM.
10 CFR 73.1200 requires licensees to notify the NRC Headquarters Operations Center (HOC) of involving imminent or actual hostile actions, significant security events, security challenges, and security program failures.
10 CFR 73.1205 requires licensees who have made a notification to the NRC (for most, but not all, of the security events listed under 10 CFR 73.1200) to also submit a written follow-up report on the event to the NRC within 60 days of the initial notification.
10 CFR 73.1210 requires licensees to document certain less significant security events or conditions adverse to security in a written log or corrective action program within 24 hours of their occurrence.
10 CFR Part 95, “Facility Security Clearance and Safeguarding of National Security Information and Restricted Data,” establishes procedures for obtaining facility security clearances and for safeguarding Secret and Confidential National Security Information (NSI) and Restricted Data (RD) received or developed in conjunction with activities licensed, certified, or regulated by the Commission (Ref. 7).
10 CFR 95.39, “External transmission of documents and material,” requires licensees to transmit classified information in accordance with specific requirements.
10 CFR 95.57, “Reports,” requires in part, that licensees report any alleged or suspected violation of the RD provisions of the AEA (Ref. 8); Espionage Act (Ref. 9); or other Federal statutes related to protection of classified information (e.g., the loss, theft, or deliberate disclosure of classified NSI or RD to unauthorized persons).
10 CFR Part 150, “Exemptions and Continued Regulatory Authority in Agreement States and In Offshore Waters Under Section 274,” provides certain exemptions to persons in Agreement States from the licensing requirements contained in Chapters 6, 7, and 8 of the AEA and from the regulations of the Commission imposing requirements upon persons who receive, possess, use or transfer byproduct material, source, or special nuclear material in quantities not sufficient to form a critical mass; and to define activities in Agreement States and in offshore waters over which the regulatory authority of the Commission continues (Ref. 10).
10 CFR 150.11, “Critical mass,” specifies the maximum quantity of SSNM or SNM that may be possessed by an Agreement State licensee.
10 CFR 150.14, “Commission regulatory authority for physical protection,” specifies that Agreement State licensees possessing a Category III quantity of SSNM remain subject to the NRC’s physical security requirements under 10 CFR 73.67, “Licensee fixed site and in-transit requirements for the physical protection of special nuclear material of moderate and low strategic significance.”
32 CFR Part 2001, “Classified National Security Information,” (Ref. 11) provides direction to agencies to implement Executive Order 13526, “Classified National Security Information.”
32 CFR 2001.52, “Emergency authority,” provides direction regarding special provisions for the dissemination, transmission, safeguarding, and destruction of classified information during certain emergency situations.
Related Guidance
NUREG-1304, “Physical Security Event Notifications, Reports, and Recordkeeping,” (Ref. 12) provides further guidance for licensees in making notifications, reports, and recordkeeping of physical security events required under 10 CFR 73.1200, 73.1205, and 73.1210.2
Regulatory Guide (RG) 5.69, “Guidance for the Application of Radiological Sabotage Design-Basis Threat in the Design, Development and Implementation of a Physical Security Program that Meets 10 CFR 73.55 Requirements (U),” (Ref. 13) provides guidance that the NRC staff finds acceptable for use by licensees to comply with the requirements in 10 CFR 73.1(a)(1).
RG 5.70, “Guidance for the Application of the Theft and Diversion Design-Basis Threat in the Design, Development, and Implementation of a Physical Security Program that Meets 10 CFR 73.45 and 73.46 Requirements (U),” (Ref. 14) provides guidance that the NRC staff finds acceptable for use by licensees to comply with the requirements in 10 CFR 73.1(a)(2).
RG 5.86, “Preemption Authority, Enhanced Weapons Authority, and Firearms Background Checks,” (Ref. 15) provides guidance and sets forth methods and procedures that the NRC staff finds acceptable for use by licensees to comply with the requirements in 10 CFR 73.15 and 10 CFR 73.17, “Firearms background checks for armed security personnel,” implementing the authority provided to the Commission under Section 161A of the AEA.
Purpose of Regulatory Guides
The NRC issues regulatory guides to describe to the public methods that the staff considers acceptable for use in implementing specific parts of the agency’s regulations, to explain techniques that the staff uses in evaluating specific problems or postulated events, and to provide guidance to applicants. Regulatory guides are not a substitute for regulations; and compliance with regulatory guides is not required. Methods and solutions that differ from those set forth in regulatory guides will be deemed acceptable if they provide a basis for the findings required for the issuance or continuance of a permit or license by the Commission.
Paperwork Reduction Act
This RG provides voluntary guidance for implementing the mandatory information collections in 10 CFR Part 73 and NRC Form 366 that are subject to the Paperwork Reduction Act of 1995 (44 U.S.C. 3501 et. seq.). These information collections were approved by the Office of Management and Budget (OMB), approval numbers 3150-0002 and 3150-0104, respectively. Send comments regarding these information collections to the FOIA, Library, and Information Collections Branch (T6-A10M), U.S. Nuclear Regulatory Commission, Washington, DC 20555-0001, or by email to [email protected], and to the OMB reviewer at: OMB Office of Information and Regulatory Affairs (3150-0002 and 3150-0104), Attn: Desk Officer for the Nuclear Regulatory Commission, 725 17th Street, NW Washington, DC 20503; e‑ mail: [email protected].
Public Protection Notification
The NRC may not conduct or sponsor, and a person is not required to respond to, a request for information or an information collection requirement unless the requesting document displays a currently valid OMB control number.
TABLE OF CONTENTS
Page
Purpose of Regulatory Guides 4
Public Protection Notification 4
Timeliness Requirements Structure Based upon Security Significance 7
Applicability to Specific Facilities, Materials, and Activities 8
Exceptions and Exemptions to Reporting and Recordkeeping Requirements 13
NRC Licensees Not Subject to Notification, Reporting, and Recordkeeping Requirements 13
Agreement State Licensees Not Subject to Notification, Reporting, and Recordkeeping Requirements 14
Establishment of a Communications Channel With the NRC 15
Notification of Significant Supplemental Information 15
Retraction of Previous Physical Security Event Notifications 15
Reporting of an Emergency Declaration 15
Security Events Associated with or Involving Classified Information 16
Recording of Physical Security Events and Conditions Adverse to Security 18
Records Retention and Destruction 19
Consideration of International Standards 20
C. STAFF REGULATORY GUIDANCE 21
2. Malevolent Intent and Credible Bomb Threat Considerations 21
3. Exception for Event Notifications Containing Safeguards Information 21
4. Consideration of Other Notifications or Recordings 22
6. Considerations for Contraband versus Prohibited Items 22
7.1 15-Minute Facility Notifications 24
7.2 15-Minute Shipment Notifications 25
7.3 Precedence of 15-Minute Notifications 26
8.1 1-Hour Facility Notifications 27
8.2 1-Hour Shipment Notifications 28
9.1 4-Hour Facility Notifications 28
9.2 4-Hour Shipment Notifications 29
10.1 8-Hour Facility Notifications 29
10.2 8-Hour Shipment Notifications 30
11. Notifications for Enhanced Weapons 30
11.1 Immediate Notifications for Enhanced Weapons 31
11.2 1-Hour Notifications for Enhanced Weapons 31
11.3 24-Hour Notifications for Enhanced Weapons 31
11.4 48-Hour Notifications for Enhanced Weapons 31
12. Required Vehicle Barrier System 32
14. Retraction of Event Notifications 33
15. Items Relied Upon for Safety (IROFS) 33
16. Security Event Notification Process 34
16.1 Continuous Communications Channel 34
16.2 Information Security Considerations During Event Notifications 34
16.3 Significant Supplemental Information 35
17. Written Follow-Up Reports 35
18. Recordable Security Events and Conditions 36
18.1 Facility and Shipment Recordable Events and Conditions 36
18.2 Recordable Events and Conditions Regarding Decreases in Effectiveness 37
18.3 Information Security Considerations for Recordkeeping 37
B. DISCUSSION
Reason for Revision
This regulatory guide is being revised because the NRC has promulgated new and updated requirements under 10 CFR 73.1200, 10 CFR 73.1205, and 10 CFR 73.1210 on physical security event notifications, written follow-up reports, and recordkeeping of less significant security events and conditions adverse to security. These new and updated requirements are part of the NRC’s final rule, “Enhanced Weapons, Firearms Background Checks, and Security Event Notifications,” (Ref. 16).
Background
Regulatory Guide 5.62 was initially issued by the NRC in February 1981. The 1981 RG provided acceptable methods and procedures for use by licensees when notifying the NRC of a physical security event. It also provided guidance on the timeliness requirements for such notifications and suggested a format for such notifications and written follow-up reports. The 1981 version of the RG addressed only two classes of physical security events (referred to as safeguards events): “threat-related events” or “loss‑of‑physical‑security-effectiveness events.” Depending on the event, telephonic notification to the NRC HOC was required within 1-hour or 24-hours of discovery.
Revision 1 of RG 5.62 was issued by the NRC in November 1987 in conjunction with the NRC’s issuance of a final rule revising safeguards reporting requirements under 10 CFR 73.71 (52 FR 21651; June 9, 1987). These revised requirements increased the numbers and types of security events that required a 1-hour notification. Additionally, the 24‑hour notification requirement was converted into a 24‑hour recordkeeping requirement recorded in a “safeguards event log.” The licensee’s safeguards event log can be reviewed periodically by NRC inspectors during on-site inspections. The regulations for physical security event notifications and the guidance in RG 5.62 have remained essentially unchanged since 1987.
Following the terrorist attacks of 2001, the NRC issued voluntary guidance to various licensees to expeditiously notify the NRC HOC within 15 minutes of imminent or actual hostile actions. These voluntary notifications highlighted the need for new regulations to address the changing threat environment. Additionally, licensee ability to possess enhanced weapons under Section 161A of the AEA resulted in new reporting and recordkeeping requirements. For these reasons, the NRC has revised RG 5.62 to incorporate the new regulations for physical security event notifications, written follow-up reports, and recordkeeping for less significant security events or conditions adverse to security.
Timeliness Requirements Structure Based upon Security Significance
The NRC has organized the timeliness requirements for physical security event notifications under 10 CFR 73.1200 using a risk-informed approach that reflects the actual or potential security significance of the event. This structure reduces impacts on licensees (i.e., in most instances licensees are given additional time to complete notifications based on the security significance of the event). The NRC has divided these physical security event notifications into two overall categories, those impacting facilities and those impacting transportation activities. The NRC has used the following broad characterizations to reflect the security significance of these notification requirements.
15-minutes – supports the need for notification to the NRC to facilitate the NRC’s prompt notification to other licensees and DHS’ National Operations Center of the discovery of an imminent or actual hostile action against a licensee’s facility or shipment of material, the initiation of a security response in accordance with a licensee’s safeguards contingency plan or protective strategy based upon a security condition, or that a licensee has been notified of a potential hostile action or act of sabotage against a licensee’s facility or shipment of material that is anticipated within the next 12 hours;
1-hour – supports the need for notification to the NRC that an event in which there is reason to believe that a person has committed or caused, or attempted to commit or cause, or has made a threat to commit or cause a significant security event against a licensee’s facility or shipment of material, or that the licensee has been notified of a potential hostile action or act of sabotage against a licensee’s facility or shipment of material, anticipated within greater than the next 12 hours;
4-hour – supports the need for notification to the NRC that an event has caused a security impact at a licensee’s facility or involving a licensee’s shipment of material; and
8-hour – supports the need for notification to the NRC of a licensee’s discovery of a facility security program failure or a transportation security program failure.
Additionally, for licensees possessing enhanced weapons under 10 CFR 73.15, the NRC has established separate notification requirements for stolen or lost enhanced weapons and receipt of adverse inspection findings or enforcement actions from the Bureau of Alcohol, Tobacco, Firearms, and Explosives (ATF). These requirements include the following:
4-hour- supports the need for notification to the NRC of stolen or lost enhanced weapons, after the licensee’s immediate notification to the ATF of such theft or loss;
24-hour- supports the need for notification to the NRC of the licensee’s receipt of an adverse inspection finding, enforcement finding, or other adverse notice from the ATF associated with the licensee’s possession of enhanced weapons; and
48-hour- supports the need for notification to the appropriate LLEA of stolen or lost enhanced weapons.
Licensees making notifications to the NRC must use the notification process specified in 10 CFR 73.1200(o). The telephone numbers for the NRC HOC are specified in Table 1 of Appendix A to 10 CFR Part 73, “Appendix A to Part 73—U.S. Nuclear Regulatory Commission Offices and Classified Mailing Addresses.”
Applicability to Specific Facilities, Materials, and Activities
The regulations in 10 CFR 73.1200, 73.1205, and 73.1210 apply to a range of NRC‑licensed facilities, materials, and shipping activities subject to the various physical security program requirements in 10 CFR Part 73. However, not all of the provisions of 10 CFR 73.1200, 73.1205, and 73.1210 apply equally to all of these classes of facilities, materials, and shipping activities. Accordingly, the following information describes the applicability of the various provisions of 10 CFR 73.1200, 73.1205, and 73.1210 to the various classes of facilities, materials, and shipping activities subject to 10 CFR Part 73:
The 15-minute notification requirements in 10 CFR 73.1200(a) for events at facilities apply to licensees subject to 10 CFR 73.20, “General performance objective and requirements”; 10 CFR 73.45, “Performance capabilities for fixed site physical protection systems”; 10 CFR 73.46, “Fixed site physical protection systems, subsystems, components, and procedures”; 10 CFR 73.51, “Requirements for the physical protection of stored spent nuclear fuel and high-level radioactive waste,” or 10 CFR 73.55, “Requirements for physical protection of licensed activities in nuclear power reactors against radiological sabotage.” These licensees include the following:
production and utilization facilities licensed under 10 CFR 50.21 and 50.22 (including both operating and decommissioning production reactors and power reactors),
facilities authorized to possess a Category I quantity of SSNM,
independent spent fuel storage installations (ISFSIs),
monitored retrievable storage installations (MRSs), and
geologic repository operations areas (GROAs).
Note: Power reactor facilities and production facilities that are in a decommissioning status and have removed all spent nuclear fuel from the facility’s spent fuel pool (e.g., to an ISFSI, MRS or GROA) need not report events under 10 CFR 73.1200(a). However, such licensees should instead consider whether the event should be reported under 10 CFR 73.1200(c), (e), or (g).
The 15-minute notification requirements in 10 CFR 73.1200(b) for events associated with shipping activities apply to licensees who are subject to the provisions of 10 CFR 73.20; 10 CFR 73.25, “Performance capabilities for physical protection of strategic special nuclear material in transit”; 10 CFR 73.26, “Transportation physical protection systems, subsystems, components, and procedures”; or 10 CFR 73.37, “Requirements for physical protection of irradiated reactor fuel in transit.” These include licensees engaged in the following:
transportation of a Category I quantity of SSNM,
transportation of SNF, and
transportation of HLW.
The 1-hour notification requirements in 10 CFR 73.1200(c) for events at facilities apply to licensees who are subject to the provisions of 10 CFR 73.20; 10 CFR 73.45; 10 CFR 73.46; 10 CFR 73.50, “Requirements for physical protection of licensed activities”; 10 CFR 73.51, “Requirements for the physical protection of stored spent nuclear fuel and high-level radioactive waste”; 10 CFR 73.55; 10 CFR 73.60, “Additional requirements for physical protection at nonpower reactors”; or 10 CFR 73.67, “Licensee fixed site and in-transit requirements for the physical protection of special nuclear material of moderate and low strategic significance.” These licensees include the following:
production and utilization facilities licensed under 10 CFR 50.21 and 50.22 (including both operating and decommissioning production reactors, power reactors, and non-power reactors),
facilities authorized to possess a Category I, Category II, or Category III quantity of SSNM,
facilities authorized to possess a Category II or Category III quantity of SNM,
hot cell facilities (for examination of irradiated SNM and SNF and HLW);
ISFSIs,
MRSs, and
GROAs.
The 1-hour notification requirements in 10 CFR 73.1200(d) for events associated with shipping activities apply to licensees who are subject to the provisions of 10 CFR 73.20; 10 CFR 73.25; 10 CFR 73.26; 10 CFR 73.27, “Notification requirements”; 10 CFR 73.37; or 10 CFR 73.67. These include licensees engaged in the following:
transportation of a Category I, Category II, or Category III quantity of SSNM,
transportation of a Category II or Category III quantity of SNM,
transportation of SNF, and
transportation of HLW.
The 4-hour notification requirements in 10 CFR 73.1200(e) for events at facilities apply to licensees who are subject to the provisions of 10 CFR 73.20, 73.45, 73.46, 73.50, 73.51, 73.55, 73.60, or 73.67. These licensees include the following:
production and utilization facilities licensed under 10 CFR 50.21 and 50.22 (including both operating and decommissioning production reactors, power reactors, and non-power reactors),
facilities authorized to possess a Category I, Category II, or Category III quantity of SSNM,
facilities authorized to possess a Category II or Category III quantity of SNM,
hot cell facilities (for examination of irradiated SNM and SNF and HLW);
ISFSIs,
MRSs, and
GROAs.
The 4-hour notification requirements in 10 CFR 73.1200(f) for events associated with shipping activities apply to licensees who are subject to the provisions of 10 CFR 73.20, 73.25, 73.26, 73.27, 73.37, or 73.67. These include licensees engaged in the following:
transportation of a Category I, Category II, or Category III quantity of SSNM,
transportation of a Category II or Category III quantity of SNM,
transportation of SNF, and
transportation of HLW.
The 8-hour notification requirements in 10 CFR 73.1200(g) for events at facilities apply to licensees who are subject to the provisions of 10 CFR 73.20, 73.45, 73.46, 73.50, 73.51, 73.55, 73.60, or 73.67. These licensees include the following:
production and utilization facilities licensed under 10 CFR 50.21 and 50.22 (including both operating and decommissioning production reactors, power reactors, and non-power reactors),
facilities authorized to possess a Category I, Category II, or Category III quantity of SSNM,
facilities authorized to possess a Category II or Category III quantity of SNM,
hot cell facilities (for examination of irradiated SNM and SNF);
ISFSIs,
MRSs, and
GROAs.
The 8-hour notification requirements in 10 CFR 73.1200(h) for events associated with shipping activities apply to licensees who are subject to the provisions of 10 CFR 73.20, 73.25, 73.26, 73.27, 73.37, or 73.67. These include licensees engaged in the following:
transportation of a Category I, Category II, or Category III quantity of SSNM,
transportation of a Category II or Category III quantity of SNM,
transportation of SNF, and
transportation of HLW.
The 1-hour notification requirements in 10 CFR 73.1200(m) requiring notification to the NRC of stolen or lost enhanced weapons applies to those licensees possessing enhanced weapons under the provisions of 10 CFR 73.15.
The 24-hour notification requirements in 10 CFR 73.1200(n) requiring notification to the NRC of a licensee’s receipt of an adverse inspection finding, enforcement finding, or other adverse notice from the ATF applies to those licensees possessing enhanced weapons under the provisions of 10 CFR 73.15.
The 48-hour notification requirements in 10 CFR 73.1200(m) requiring notification to the appropriate LLEA of stolen or lost enhanced weapons applies to those licensees possessing enhanced weapons under the provisions of 10 CFR 73.15.
The 60-day reporting requirement in 10 CFR 73.1205(a) requiring a written follow-up report by licensees who make telephonic notifications under 10 CFR 73.1200 of security events to the NRC applies to licensees who are subject to the provisions of 10 CFR 73.20, 73.25, 73.26, 73.27, 73.37, 73.45, 73.46, 73.50, 73.51, 73.55, 73.60, or 73.67. These licensees include the following:
production and utilization facilities licensed under 10 CFR 50.21 and 50.22 (including both operating and decommissioning production reactors, power reactors, and non-power reactors),
facilities authorized to possess a Category I, Category II, or Category III quantity of SSNM,
facilities authorized to possess a Category II or Category III quantity of SNM,
hot cell facilities (for examination of irradiated SNM and SNF and HLW);
ISFSIs,
MRSs,
GROAs.
transportation of a Category I, Category II, or Category III quantity of SSNM,
transportation of a Category II or Category III quantity of SNM,
transportation of SNF, and
transportation of HLW.
The 24-hour recordkeeping requirements n 10 CFR 73.1210 requiring licensees to record less significant physical security events and conditions adverse to security at facilities or shipments applies to licensees who are subject to the provisions of 10 CFR 73.20, 73.25, 73.26, 73.27, 73.37, 73.45, 73.46, 73.50, 73.51, 73.55, 73.60, or 73.67. These licensees include the following:
production and utilization facilities licensed under 10 CFR 50.21 and 50.22 (including both operating and decommissioning production reactors, power reactors, and non-power reactors),
facilities authorized to possess a Category I or Category II quantity of SSNM,
hot cell facilities (for examination of irradiated SNM and SNF and HLW),
ISFSIs,
MRSs,
GROAs,
transportation of a Category I or Category II quantity of SSNM,
transportation of SNF, and
transportation of HLW.
Exceptions and Exemptions to Reporting and Recordkeeping Requirements
The regulations in 10 CFR 73.1205(a)(2) provide licensees with exceptions to the requirement to submit certain written follow-up reports to the NRC following a notification made under 10 CFR 73.1200. These exceptions include the following:
notifications made under 10 CFR 73.1200(e)(2) and (f)(2) regarding interactions with Federal, State, or local law enforcement agencies,
notifications made under 10 CFR 73.1200(m) regarding stolen or lost enhanced weapons (for licensees possessing enhanced weapons under 10 CFR 73.15), or
notifications made under 10 CFR 73.1200(n) regarding adverse findings issued by the ATF (for licensees possessing enhanced weapons under 10 CFR 73.15).
The regulations in 10 CFR 73.1205(a)(3) provide licensees with an exception to the written follow-up report requirement following a notification made under 10 CFR 73.1200 when the licensee retracts that notification. This exception only applies if the licensee has not already submitted a written follow-up report.
The regulations in 10 CFR 73.1210(h) provide licensees subject to 10 CFR 73.67, who possess or transport a Category III quantity of SSNM or a Category II or III quantity of SNM, with an exemption from the recordkeeping requirements of 10 CFR 73.1210.
NRC Licensees Not Subject to Notification, Reporting, and Recordkeeping Requirements
NRC licensees authorized to operate, possess, or conduct the following facilities, materials, and activities are not subject to the physical security program requirements of 10 CFR Part 73. Therefore, these NRC licensees are also not subject to the physical security event notification, written follow-up reporting, or recordkeeping requirements of 10 CFR 73.1200, 73.1205, and 73.1210. Consequently, this RG does not apply to the following:
facilities, materials, and activities licensed by the NRC that involve the production, use, storage, and transportation of byproduct materials subject to the requirements of 10 CFR Part 37, “Physical Protection of Category 1 and Category 2 Quantities of Radioactive Material” (Ref. 17);
facilities, materials, and activities licensed by the NRC that involve the production, use, storage, conversion, deconversion, and transportation of source materials subject to the requirements of 10 CFR Part 40, “Domestic Licensing of Source Material” (Ref. 18); and
facilities, materials, and activities licensed by the NRC that involve the production, receipt, possession, use, storage, and transportation of less than a Category III quantity of SSNM or SNM. This means less than 15.0 grams (g) of nuclear material involving: U-235 enriched to 20 percent or more, U-233, or Pu; less than 1,000 g U-235 enriched to 10 percent or more but less than 20 percent; or less than 10,000 g U-235 enriched to less than 10 percent. Additionally, certain types of nuclear materials listed under the provisions of 10 CFR 73.67(b) are exempt from the requirements of 10 CFR 73.67. Consequently, such NRC licensees, who are not subject to 10 CFR 73.67, are also not subject to the requirements of 10 CFR 73.1200, 73.1205, or 73.1210.
Agreement State Licensees Not Subject to Notification, Reporting, and Recordkeeping Requirements
Agreement State licensees are not subject to the physical security event notification, written follow-up reporting, or recordkeeping requirements of 10 CFR 73.1200, 73.1205, and 73.1210. Consequently, this RG does not apply to the following:
facilities, materials, and activities licensed by an Agreement State that involve the production, use, storage, and transportation of byproduct materials subject to the Agreement State’s requirements that are compatible with 10 CFR Part 37;
facilities, materials, and activities licensed by an Agreement State that involve the production, use, storage, conversion, deconversion, and transportation of source materials subject to the Agreement State’s requirements that are compatible with 10 CFR Part 40; and
facilities, materials, and activities licensed by the NRC that involve the production, receipt, possession, use, storage, and transportation of less than a Category III quantity of SSNM that is subject to the Agreement State’s requirements that are compatible with 10 CFR Part 70.
Based upon the definitions of Category II and III quantities of SNM involving low-enriched uranium (LEU) found under 10 CFR 73.2 and the critical mass limit of 10 CFR 150.11(a), an Agreement State licensee cannot be authorized to receive, possess, use, or transport such quantities of LEU. Instead, an NRC license is required to receive, possess, use, or transport such quantities of LEU and such a licensee would nominally be subject to 10 CFR 73.67; and therefore, to 10 CFR 73.1200.
However, under 10 CFR 150.14, an Agreement State licensee may be authorized to receive, possess, use, or transport a Category III quantity of SSNM. Such an Agreement State licensee is subject to the security requirements of 10 CFR 73.67 and remains under NRC jurisdiction with respect to security issues. This means a quantity of SSNM that is greater than 15 g of U-235 (contained in uranium enriched to 20 percent or greater in the U-235 isotope), U-233, or Pu; but is less than the critical mass limit of 10 CFR 150.11(a). The critical mass limit means a quantity of special nuclear material that is less than 350 g of U-235, less than 200 g of U-233, less than 200 g of Pu, or less than any combination of these three nuclides using the following unity formula.
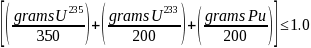
Agreement State licensees who are not subject to the requirements of 10 CFR 73.67 are also not subject to the requirements of 10 CFR 73.1200 and 10 CFR 73.1205. Additionally, under 10 CFR 73.1210(h), Agreement State licensees possessing or transporting a Category III quantity of SSNM (pursuant to 10 CFR 73.67) are exempt from the recordkeeping requirements in 10 CFR 73.1210.
Establishment of a Communications Channel With the NRC
Under 10 CFR 73.1200(o)(5) or (o)(7), a licensee making a notification to the NRC for events affecting a facility may be requested by the NRC HOC to establish and maintain an open and continuous communications channel. The communications channel must be staffed by an individual who is knowledgeable in the licensee's security, operations, or emergency response organizations. The licensee may staff the channel from a location it deems appropriate.
Under 10 CFR 73.1200(o)(6) or (o)(8), a licensee or its movement control center making a notification to the NRC for events affecting a shipment of material may be requested by the NRC HOC to establish and maintain an open and continuous communications channel. The communications channel must be staffed by an individual who is knowledgeable in the licensee's security, operations, or emergency response organizations or movement control center monitoring the shipment. The individual should be knowledgeable about the shipment and its security measures.
Notification of Significant Supplemental Information
Under 10 CFR 73.1200(p), a licensee or its movement control center who have notified the NRC of a physical security event under 10 CFR 73.1200(a)-(h) and (m)-(n) must notify the NRC of any subsequently identified significant supplemental information using the notification process specified under 10 CFR 73.1200(o).
Retraction of Previous Physical Security Event Notifications
Under 10 CFR 73.1200(q), a licensee or its movement control center may retract a physical security event notification that is subsequently determined to be invalid, not reportable under the provisions of 10 CFR 73.1200, or recharacterized as recordable under the provisions of 10 CFR 73.1210. The licensee or its movement control center must notify the NRC HOC of the retraction and the basis for the retraction in accordance with the notification procedures in 10 CFR 73.1200(o).
Reporting of an Emergency Declaration
Under 10 CFR 73.1200(r), a licensee or its movement control center who has declared an emergency related to a facility or a shipment of material must make the appropriate notifications required by 10 CFR 50.72, “Immediate notification requirements for operating nuclear power reactors”; 10 CFR 63.73, “Reports of deficiencies”; 10 CFR 70.50, “Reporting requirements”; or 10 CFR 72.75, “Reporting requirements for specific events and conditions.” The NRC staff expects that reporting of an emergency declaration should typically take precedence over any physical security event notifications required under 10 CFR 73.1200 (e.g., notification of State officials of an emergency declaration). However, under 10 CFR 73.1200(s), a licensee with multiple notification obligations (e.g., an event requiring both an emergency declaration and a physical security event notification) may make such notifications in a single communication to the NRC HOC.
Elimination of Duplication
A licensee or its movement control center must notify the appropriate State authorities and the NRC HOC when declaring an emergency in accordance with the requirements in 10 CFR 50.72, 63.73, 70.50, or 72.75. A licensee or its movement control center must notify the NRC HOC of nonemergency, safety‑based event in accordance with the requirements in 10 CFR 50.72, 63.73, 70.50, or 72.75. Such events may also include a physical security event requiring notification to the NRC in accordance with the requirements in 10 CFR 73.1200. Under 10 CFR 73.1200(s), the licensee or its movement control center may combine these multiple notifications to the NRC HOC into a single communication to eliminate duplication and reduce burden. This flexibility applies only to duplicate notifications to the NRC HOC and does not affect a licensee’s or its movement control center’s responsibility to make required notifications to appropriate State authorities.
Security Events Associated with or Involving Classified Information
The unauthorized disclosure, theft, loss, compromise, or possible compromise of classified information or RD must be reported to the NRC HOC in accordance with 10 CFR 95.57. However, a single event may involve both a notification of unauthorized disclosure of classified information or RD under 10 CFR 95.57 and also a physical security event requiring notification under 10 CFR 73.1200. Licensees and movement control centers must communicate such classified details regarding physical security event notifications in accordance with 10 CFR 73.1200(o) and Section III of Appendix A to 10 CFR Part 73. Consistent with the elimination of duplication guidance discussed above, the licensee or its movement control center may communicate both events in a single classified notification to the NRC HOC.
Written Follow-Up Reports
Following a physical security event notification made either by a licensee or its movement control center, a licensee must submit a written follow-up report within 60 days in accordance with 10 CFR 73.1205. The classes of licensed facilities, material, and transportation activities subject to this regulation are discussed above.
Licensees must comply with the submission criteria of 10 CFR 73.1205(b) when submitting written follow-up reports. The licensee must submit such reports to the NRC via the processes specified in 10 CFR 73.4, “Communications.” These submission criteria include the following:
Licensees subject to 10 CFR 50.73, “License event report system,” must submit a written follow-up report using NRC Form 366, “Licensee Event Report (LER)” (Ref. 19).
Licensees who are not subject to 10 CFR 50.73 must submit a written follow-up report using a letter format.
The written follow-up report must contain sufficient information to enable the NRC to analyze and evaluate the event to determine if follow-up action is needed.
If significant supplemental information becomes available after the licensee’s submission of an initial written follow-up report, then the licensee must submit a revised report. The revised report must indicate the revisions and replace the initial report in its entirety (i.e., the revision must be complete and not limited to only the supplementary or revised information).
If the licensee identifies errors in a written follow-up report, then the licensee must submit a revised report correcting the errors and indicating the revisions.
Licensees must comply with the content requirements of 10 CFR 73.1205(c) for written follow‑up reports. The report must include, at a minimum, the following information:
a brief abstract describing the major occurrences during the event or condition, including all component or system failures that contributed to the event or condition, and significant corrective actions taken or planned to prevent recurrence;
a clear, specific narrative description of what occurred so that a knowledgeable reader conversant with security program requirements can understand the event or condition, including, at a minimum, the following information, as applicable:
the date and time the event or condition was discovered;
the date and time the event or condition occurred;
the affected structures, systems, components (SSCs), equipment, or procedures;
the environmental conditions at the time of the event or occurrence, if relevant;
the root cause of the event or condition;
whether any human performance errors were the cause or were a contributing factor (e.g., personnel errors, inadequate procedures, or inadequate training);
whether previous events or conditions are relevant to the current event or condition and whether corrective actions to prevent recurrence were ineffective or insufficient;
whether this event or condition is a recurring failure of an SSC or procedure important to security;
what compensatory measures, if any, were implemented in response to the event or condition; and
when corrective actions to prevent recurrence, if any, were taken or will be completed.
Licensees are required to comply with the transmission criteria requirements of 10 CFR 73.1205(d) for written follow-up reports. These include the following:
The licensee must provide written follow-up reports to: 1) an addressee specified in 10 CFR 73.4 and 2) the NRC’s Director, Office of Nuclear Security and Incident Response.
The licensee must transmit written follow-up reports containing classified information to the NRC’s Headquarters via a transmission system authorized for the use of classified information under 10 CFR Part 95. This involves secure transmission to either the NRC Headquarters’ classified mailing address specified in Table 2 of Appendix A to 10 CFR Part 73 or to the NRC Headquarters’ secure email address specified in Table 1 of Appendix A to 10 CFR Part 73. Additionally, reports containing classified information must be created, used, destroyed, stored, marked, labeled, handled, and transmitted in accordance with the requirements of the licensee’s NRC-approved Standard Practices Procedures Plan under 10 CFR Part 95.
The licensee must transmit written follow-up reports containing SGI to the NRC Headquarters’ mailing address specified in 10 CFR 73.4, in accordance with the requirements of 10 CFR 73.21 and 10 CFR 73.22. Reports containing SGI must be created, used, destroyed, stored, marked, labeled, handled, and transmitted in accordance with the requirements of 10 CFR 73.21 and 10 CFR 73.22 and the licensee’s NRC-approved physical security plan.
Licensees are required to comply with the records retention requirements of 10 CFR 73.1205(e). Licensees must maintain a copy of a written follow-up report as a record for a period of 3 years from the date of the report or until termination of the license, whichever is later. (See also the Records Destruction Considerations below.)
Recording of Physical Security Events and Conditions Adverse to Security
Licensees are required to record physical security events and conditions adverse to security in accordance with the recordkeeping requirements of 10 CFR 73.1210. Such events and conditions do not require a notification to the NRC. However, the licensee must record such events and conditions with sufficient information to facilitate licensee monitoring of the effectiveness of their quality assurance programs. Such records are also intended to facilitate the licensees’ effective tracking, trending, and performance monitoring of physical security events, conditions adverse to security, and implementation of corrective actions to prevent recurrence.
Under 10 CFR 73.1210(a)(1), licensees must record the physical security events and conditions adverse to security specified in 10 CFR 73.1210(c) – (f). Under 10 CFR 73.1210(a)(3), these physical security events and conditions adverse to security include, but are not limited to, the following broad categories:
human performance security errors,
licensee or contractor personnel failing to comply with security procedures,
insufficient or inadequate security procedures,
security equipment failures and malfunctions,
design deficiencies in security SSCs,
inadequate or insufficient security SSCs, and
events or conditions in which the licensee has implemented compensatory security measures within the required timeframe specified in its physical security plan.
For events or conditions for which a licensee has not implemented compensatory security measures within the required timeframe specified in its physical security plan, they require a notification under 10 CFR 73.1200. Accordingly, the licensee should refer to the applicable provisions for physical security event notifications under 10 CFR 73.1200(g) and (h).
Licensees are required to comply with the general requirements of 10 CFR 73.1210(b) when recording physical security events and conditions adverse to security. These requirements include the following:
Under 10 CFR 73.1210(b)(1), licensees must record these events or conditions within 24 hours of the time of discovery.
Under 10 CFR 73.1210(b)(3), licensees must record such events and conditions in either a standalone safeguards event log, in a corrective action program which is part of the licensees’ overall quality assurance program, or both. Licensees must ensure that any SGI or classified information contained in such reports is created, stored, and handled in accordance with the requirements of 10 CFR 73.21 and 10 CFR 73.22 or 10 CFR Part 95, as applicable.
Under 10 CFR 73.1210(b)(4), these records must include, but are not limited to, the following data elements, as applicable.
The date and time the event or condition was discovered;
The date and time the event or condition occurred;
The affected structures, systems, components, equipment, or procedures;
A description of the event or condition;
Any relevant environmental conditions at the time of the event or occurrence;
The root cause of the event or condition;
Whether any human performance errors were the cause or were a contributing factor of the event or condition, including: personnel errors, inadequate procedures, or inadequate training;
Whether previous events or conditions are relevant to the current event or condition and whether corrective actions were ineffective or insufficient;
Whether this event or condition is a recurring failure of a structure, system, component, or procedure;
What compensatory measures, if any, were implemented in response to the event or condition;
What corrective actions, if any, were taken in response to the event or condition; and
When corrective actions, if any, were taken or will be completed.
Under 10 CFR 73.1210(b)(5) and 10 CFR 73.1210(b)(7), licensees are not required to record physical security events and conditions adverse to security for which a physical security event notification was made under 10 CFR 73.1200.
Under 10 CFR 73.1210(b)(6) licensees are not required to record physical security events and conditions adverse to security for which a suspicious activity report was made under 10 CFR 73.1215, “Suspicious Activity Reports Under 10 CFR Part 73.”
Records Retention and Destruction
Under 10 CFR 73.1205(e), licensees must retain a copy of a written follow-up report submitted to the NRC for 3 years or until the license is terminated, whichever comes later.
Under 10 CFR 73.1210(b)(2), licensees must retain records of physical security events and conditions adverse to security that were recorded in a safeguards event log or in a corrective action program log for 3 years or until the license is terminated, whichever comes later.
Licensees destroying reports or records that are no longer required to be retained and that contain classified or SGI information must destroy such reports or records in accordance with the appropriate destruction procedures for the applicable class of information, as specified in 10 CFR Part 95 or 10 CFR 73.21 and 10 CFR 73.22, respectively.
Consideration of International Standards
The International Atomic Energy Agency (IAEA) works with member states and other partners to promote the safe, secure, and peaceful use of nuclear technologies. The IAEA develops Safety Requirements and Safety Guides for protecting people and the environment from harmful effects of ionizing radiation. This system of safety fundamentals, safety requirements, safety guides, and other relevant reports, reflects an international perspective on what constitutes a high level of safety. To inform its development of this RG, the NRC considered IAEA Safety Requirements and Safety Guides pursuant to the Commission’s International Policy Statement (Ref. 20), and Management Directive and Handbook 6.6, “Regulatory Guides” (Ref. 21). The NRC staff did not identify any IAEA Safety Requirements or Guides with information related to the topic of this RG.
C. STAFF REGULATORY GUIDANCE
This section provides detailed descriptions and examples of the methods and procedures that the NRC staff considers acceptable for use by a licensee or its designated movement control center in meeting the physical security event notification, written follow-up reporting, and recordkeeping requirements in 10 CFR 73.1200, 73.1205, and 73.1210.
1. Time of Discovery
In 10 CFR 73.2, the NRC has defined the term “time of discovery” as follows:
Time of discovery means the time at which a cognizant individual observes, identifies, or is notified of a security-significant event or condition. A cognizant individual is considered anyone who, by position, experience, and/or training, is expected to understand that a particular condition or event adversely impacts security.
The time of discovery serves as the starting point for licensee compliance in meeting the timeliness requirements for physical security event notifications under 10 CFR 73.1200 and recordkeeping under 10 CFR 73.1210.
Licensees should use sufficient time and their best judgment to promptly assess whether a physical security event requires a notification to the NRC under 10 CFR 73.1200. For some events an analysis and evaluation may be necessary for a licensee to determine that an event is reportable. The NRC does not expect licensees to spend an excessive amount of time conducting an exhaustive and definitive analysis to determine if a physical security event is reportable.
Any licensee analysis and evaluation should promptly reach a conclusion in a time frame commensurate with the security significance of the event or condition. If uncertain whether an event requires a notification, licensees should default to notifying the NRC within the appropriate timeliness requirements. If the results of a subsequent evaluation indicate that the event did not need to be reported to the NRC, then the licensee may retract the notification or reclassify the event as recordable under 10 CFR 73.1210. The NRC prioritizes the prompt reporting of such notifications; therefore, licensees will face no penalty for subsequently withdrawing an invalid notification.
2. Malevolent Intent and Credible Bomb Threat Considerations
The regulations in 10 CFR Part 73 do not require licensees to possess the personnel resources and technical qualifications necessary to assess whether a physical security event or threat was motivated by malevolent intent or is credible. Consequently, it is the NRC’s position that only government officials have the necessary resources and qualifications to determine whether malevolent intent was present in a security event. Such government officials include, but are not limited to, the NRC’s Office of Investigations (OI); the intelligence community; or a Federal, State, or local law enforcement agency. Accordingly, a licensee may rely on a government agency’s determination that malevolent intent was not present in a security event or that a bomb threat was not credible as a basis for considering a security event as invalid and retract the notification under the provisions of 10 CFR 73.1200(q).
3. Exception for Event Notifications Containing Safeguards Information
Under 10 CFR 73.1200(o)(3), notifications that contain SGI may be made to the NRC HOC without using secure communications systems under the exception in 10 CFR 73.22(f)(3), as such communications are considered communications of extraordinary conditions. If a licensee has ready access to secure telecommunications equipment, the NRC recommends using that equipment to communicate the notification containing SGI to the NRC. Secure communications equipment that is appropriate for transmitting classified information is also considered appropriate for transmitting SGI. However, consistent with 10 CFR 73.22(f)(3), the licensee should not exceed the timeliness requirement for the event notification in an effort to obtain access to secure telecommunications equipment to communicate the notification. The licensee should follow the procedure in Section III of Appendix A to 10 CFR Part 73 to make a notification using secure telecommunications equipment.
This exception applies only to notifications associated with actual events. Consequently, this exception does not apply to simulated event notifications associated with security drills, emergency response exercises, or security evaluations. These types of notifications are not considered emergency or extraordinary conditions. Therefore, any notification containing SGI related to a security drill, response exercise, or security evaluation must be made via secure telecommunications equipment.
4. Consideration of Other Notifications or Recordings
Licensees should evaluate an event using all of the applicable notification requirements under 10 CFR 73.1200 and the regulatory positions in this guide. A licensee’s evaluation should proceed from the applicable guidance in order of priority—that is, from the most urgent notification (quickest timeliness requirement) to the least urgent notification (longest timeliness requirement). If an event is reportable under multiple notification requirements with varying time limits, the licensee should make the notification using the quickest applicable timeliness requirement. Finally, if a licensee concludes that a security event does not require a notification to the NRC under 10 CFR 73.1200, the licensee should also evaluate whether the event is instead recordable under 10 CFR 73.1210. Staff Regulatory Guidance position 18.2 provides guidance on recordable events.
5. Movement Control Center
For transportation-related activities discussed in this guide, a licensee may use a designated movement control center to meet the requirements of 10 CFR 73.1200 and 73.1205. Accordingly, a movement control center, acting on behalf of the licensee, may monitor a shipment’s position and status, request assistance from LLEA, receive threat information from government agencies, make any required notifications to the NRC, and staff a continuous communications channel (if the channel is requested by the NRC under 10 CFR 73.1200(o)). A movement control center, acting on behalf of the licensee, may prepare the written follow-up reports required under 10 CFR 73.1205 following a notification made under 10 CFR 73.1200. The NRC recommends that the licensee review and approve these written follow-up reports and any corrective actions before the report’s submission to the NRC.
6. Considerations for Contraband versus Prohibited Items
In 10 CFR 73.2 the term “contraband” is defined to mean unauthorized firearms, explosives, incendiaries, or other dangerous materials (e.g., disease-causing agents) that can cause acts of sabotage against a licensee’s facility. NRC regulations prohibit the introduction of contraband items into a licensee’s PA, VA, or MAA.
The definition of contraband in 10 CFR 73.2 is broader for licensees who possess or conduct activities involving classified information or RD. For those licensees, contraband also includes unauthorized electronic devices or unauthorized electronic media that can be used in acts of espionage involving NSI or the unauthorized communication, transmission, receipt, tampering or disclosure of RD.
Items possessed by authorized persons for authorized purposes inside the facility should not be considered contraband. For example, licensees should not consider as contraband: weapons possessed by the facility’s security personnel as part of their official duties; weapons possessed by local, state, or Federal law enforcement personnel visiting the facility for official purposes; explosive squib valves used in certain types of reactors; and explosives or incendiaries intended for authorized and controlled activities at the facility. This list of examples is not meant to be exhaustive.
Items possessed by authorized persons for authorized purposes associated with a transportation activity outside the facility should not be considered contraband. For example, licensees should not consider as contraband: weapons possessed by local, state, or Federal law enforcement personnel performing escort duties; explosives possessed by law enforcement personnel performing escort duties; weapons possessed by authorized licensee escort personnel, or weapons possessed by vehicle operators under applicable state law (e.g., the vehicle operator has a concealed carry permit).
Under 10 CFR 73.67, licensees possessing Category II and III quantities of SSNM, or Category II and III quantities of SNM, are not required to conduct searches of personnel, packages, or vehicles prior to their entry into the CAA. However, the NRC staff recommends as a good practice that licensees voluntarily notify the NRC of the discovery of items inside the CAA that would normally be considered contraband. These voluntary notifications should be made consistent with the timeliness requirements of the applicable contraband event notification provisions specified in 10 CFR 73.1200(e).
The term “prohibited items” is not defined in NRC regulations. Consequently, licensees can determine what they consider to be prohibited items. Licensees can also determine where on their site these items are prohibited. The NRC staff recommends as a good practice that licensees clearly specify what are prohibited items and where on the licensee’s site these items are prohibited. These determinations should be clearly communicated to licensee personnel and contactor personnel as well as visitors.
7. 15-Minute Notifications
The NRC recognizes that the 15-minute notification requirement imposes a burden upon a licensee or a movement control center. Accordingly, the NRC has adopted a graded approach that limits the requirements in 10 CFR 73.1200(a) and (b) to a defined group of licensees and only for events involving imminent or actual hostile actions or potential hostile actions or acts of sabotage against the licensee’s facility, material, or shipment activities.
Such actions or acts of sabotage against an individual licensee may be a precursor to a more general (widespread) attack upon the Nation’s other critical infrastructure sectors. A licensee’s prompt notification of such actions or acts permits the NRC’s HOC to promptly communicate such hostile actions to the U.S. Department of Homeland Security’s (DHS’) National Operations Center, other appropriate Federal agencies, and other potentially affected NRC licensees. Such communications are a vital component of the U.S. Government’s overall efforts to respond to threats against the Nation’s critical infrastructure. The NRC’s rapid dissemination of these notifications permits other NRC licensees, Federal facilities, military installations, and critical infrastructure facilities to immediately increase their defensive posture in advance of potential coordinated multiple-target, or multiple-sector, terrorist attacks.
7.1 15-Minute Facility Notifications
The 15-minute notification requirement applies to imminent or actual hostile actions or attempted acts of sabotage against an applicable licensee’s facility or material. Under 10 CFR 73.1200(a)(3), a licensee must provide certain specified information when making a 15-minute notification. Given the urgency associated with 15-minute notifications, the information in these notifications is an abbreviated set of the information required under 10 CFR 73.1200(o).
Examples of imminent or actual hostile actions or attempted acts of sabotage against a licensee’s facility or material that warrant notification under 10 CFR 73.1200(a) include, but are not limited to, the following:
The licensee initiates a security response in accordance with its safeguards contingency plan or protective strategy based on an imminent or actual hostile action or act of sabotage against the licensee’s facility or material.
The licensee receives a notification from law enforcement, the intelligence community, or other government agency officials of a credible threat of a potential hostile action or an act of sabotage against the licensee’s facility and the threat is expected to occur within the next 12 hours. If the timing of the threat is indeterminate, then the licensee should notify the NRC under the 1‑hour notification provisions (see Staff Regulatory Guidance position 8.1). Notification is not required if the NRC is the government agency that informs the licensee of the threat of a potential hostile action or act of sabotage.
The detonation of bulk explosives or of an explosive device at the licensee’s facility or within close proximity to the facility. This includes the use of explosives by ground assault force personnel, unmanned aerial systems, or the use of a vehicle-borne improvised explosive device (VBIED), including either land-based or waterborne VBIEDs.
The discovery of unauthorized explosive materials, incendiary materials, or an improvised explosive device within the licensee’s site boundary.
Unauthorized weapons are fired within the licensee’s PA, VA, MAA, or CAA.
Unauthorized weapons are fired from outside of the licensee’s facility and the projectiles hit the facility, causing an immediate threat to the facility, to security personnel, or to other personnel.
Unauthorized personnel or vehicles succeed in violently or forcibly penetrating a PA, VA, MAA, or CAA.
Hostages are taken inside the licensee’s facility.
Offsite hostage-taking is reasonably determined to be related to facility operations or security functions (e.g., the kidnapping of facility personnel’s family members to coerce employees into violating laws, NRC regulations, or the facility’s license).
Explosives or incendiary devices are used to cause, or attempt to cause, radiological sabotage or the theft or diversion of SSNM, SNM, SNF, or HLW.
A vehicle is used to cause an actual or attempted breach or disablement of the licensee’s required vehicle barrier system (VBS), for example by attempting to circumvent the VBS or by striking it violently at a high rate of speed. See also Staff Regulatory Guidance position 12.
7.2 15-Minute Shipment Notifications
The 15-minute notification requirement applies to imminent or actual hostile actions or attempted acts of sabotage against an applicable licensee’s shipment activities. Under 10 CFR 73.1200(b)(3), the licensee or the movement control center must provide certain specified information when making a 15‑minute notification. Given the urgency associated with 15-minute notifications, the information in these notifications is an abbreviated set of the information required under 10 CFR 73.1200(o).
Examples of imminent or actual hostile actions or attempted acts of sabotage against a licensee’s shipment activities that warrant notification under 10 CFR 73.1200(b) include, but are not limited to, the following:
The licensee initiates a security response in accordance with its safeguards contingency plan or protective strategy based on an imminent or actual hostile action or act of sabotage against a shipment conducted by the licensee.
The licensee receives a notification from law enforcement, the intelligence community, or other government agency officials of a credible threat of a potential hostile action or an act of sabotage against a shipment conducted by the licensee and the threat is expected to occur within the next 12‑hours. If the timing of the threat is indeterminate, then the licensee should notify the NRC under the 1-hour notification provisions (see Staff Regulatory Guidance position 8.2). Notification is not required if the NRC is the government agency that informs the licensee of the threat of a potential hostile action or act of sabotage.
The detonation of bulk explosives or an explosive device at or near a transport vehicle. This includes the use of explosives by ground assault force personnel or the use of a VBIED.
The ignition of an incendiary device against the transport vehicle or the transport package.
There is actual or believed theft or sabotage of a shipment.
Adversaries fire weapons at the transport vehicle(s), and projectiles hit the transport vehicle(s), which causes an immediate threat to the shipment.
Adversaries fire weapons at the transport vehicle(s), and projectiles hit the transport vehicle(s) or escort vehicles, which causes an immediate threat or injury to the shipment’s security escorts or the vehicle operators.
Unauthorized personnel succeed in forcibly penetrating a transport vehicle.
Unauthorized personnel succeed in forcibly penetrating a transport package.
Hostages are taken on site (e.g., at the shipping facility, receiving facility, or movement control center) or off site, and the hostage-taking is related to the shipment’s operations or security.
Offsite hostage-taking is reasonably determined to be related to shipment operations or security functions (e.g., the kidnapping of family members to coerce employees into violating laws, NRC regulations, U.S. Department of Transportation regulations, or the shipping or receiving facility’s license or certificate of compliance).
7.3 Precedence of 15-Minute Notifications
Under 10 CFR 73.1200(a) and (b), a licensee or its designated movement control center must complete a 15‑minute notification to the NRC as soon as possible, but within 15 minutes of the time of discovery of an event triggering these notification requirements. In making a 15-minute notification, a licensee’s or movement control center’s request for immediate LLEA assistance, initiation of a contingency response, or notification of State officials required under the licensee’s Emergency Response Plan should take precedence over its physical security event notification to the NRC. Under 10 CFR 73.1200(a)(5)(ii) or (b)(5)(ii), this notification to the NRC HOC must occur as soon as possible after the LLEA and State notifications are completed, and the contingency response is initiated, even if this exceeds the 15-minute timeliness requirement.
Under 10 CFR 73.1200(o)(5), the NRC has clarified the requirement for a licensee to staff a continuous communications channel following an initial 15‑minute notification for facilities and materials. If requested to do so by the NRC HOC, a licensee should establish a continuous communications channel as soon as possible after the NRC’s request. The continuous communications channel must be staffed by a knowledgeable individual in the licensee's security, operations, or emergency response organizations.
Under 10 CFR 73.1200(o)(6), the NRC has clarified the requirement for a licensee or its designated movement control center to staff a continuous communications channel following an initial 15‑minute notification for shipping activities. If requested to do so by the NRC HOC, a licensee or a movement control center should establish a continuous communications channel as soon as possible after the NRC’s request. The continuous communications channel must be staffed by a knowledgeable individual in the licensee's security, operations, or emergency response organizations or by a knowledgeable individual in the movement control center that is monitoring a licensee’s shipment. Licensees should also refer to Staff Regulatory Guidance position 16 for further guidance on communicating event notifications to the NRC HOC.
8. 1-Hour Notifications
Under 10 CFR 73.1200(c) and (d), a licensee or its designated movement control center must notify the NRC HOC as soon as possible but not later than 1 hour after the time of discovery of certain significant physical security events affecting licensee facilities and shipping activities. The 1-hour notification requirement is applicable to those events that pose the greatest risk to the physical security of the facility or shipping activity. The NRC has taken risk into account when determining what constitutes a significant physical security event. This approach reduces the number of notifications that must be made to the NRC within 1 hour. Many of the notifications that were previously required to be reported within 1 hour must now be reported within 4 or 8 hours, as applicable.
8.1 1-Hour Facility Notifications
The significant physical security events affecting facilities that must be reported within 1 hour are set forth in 10 CFR 73.1200(c)(1)(i)–(iii). Examples and clarifications of significant physical security events include, but are not limited to, the following:
Under 10 CFR 73.1200(c)(1)(iii) licensees are required to notify the NRC HOC when informed by law enforcement, the intelligence community, or other government officials of a potential hostile action or act of sabotage, and the threat or action is not expected to occur within the next 12‑hours or the time of occurrence is indeterminate. A licensee is not required to notify the NRC HOC if the NRC was the government agency that informed the licensee of a potential hostile action or act of sabotage.
Implementation of the licensee’s contingency response plan following receipt of a potential hostile action or act of sabotage, and the threat or action is not expected to occur within the next 12-hours or the time of occurrence is indeterminate. A licensee is not required to notify the NRC HOC if the NRC was the government agency that informed the licensee of a potential hostile action or act of sabotage that led to the contingency response plan’s implementation.
Licensees who are subject to 10 CFR 73.50, 73.60, and 73.67 must meet the 1-hour notification requirement in 10 CFR 73.1200(c), but are not subject to the 15-minute notification requirement in 10 CFR 73.1200(a). Accordingly, these licensees must notify the NRC HOC within 1 hour of the discovery of unauthorized explosive materials, incendiary materials, or an improvised explosive device within the licensee’s site boundary.
A vehicle strikes a component of a required VBS in a manner that is more than a minor accident (i.e., the impact degrades the ability of the VBS to perform its intended functions). See also Staff Regulatory Guidance position 12.
The loss of all offsite communications capabilities if these capabilities are necessary to meet regulatory requirements (e.g., they are specified in the licensee’s security plans or emergency response or preparedness plans).
The loss of all normal and alternate security radio-communications frequencies necessary to implement the facility’s protective strategy.
The loss of all alternating current and direct current power to security systems (e.g., powering detection and assessment systems, alarm sensors, electronic locks and keypads, or security communications) that affects the licensee’s ability to successfully implement its protective strategy.
For notifications required under 10 CFR 73.1200(c)(1)(i)(C) or (D), licensees should report unauthorized operation, manipulation, or tampering events involving safety related SSCs at reactors or events involving items relied upon for safety at Category I SSNM facilities, respectively.
For notifications required under 10 CFR 73.1200(c)(1)(ii), licensees should refer to RG 5.69 or RG 5.70, as applicable, for applicable guidance on the quantity of unauthorized explosives that meets or exceeds the relevant facility’s adversary characteristics’ limits.
The NRC staff recommends as a good practice that a licensee for a production facility should report events involving unauthorized operation, manipulation, or tampering activities that interrupt the normal operations of the facility. Such events may include, but are not limited to, the interruption of the production of SSNM, electricity, and/or process steam
The NRC staff should be aware that an event reported under 10 CFR 73.1200(c)(1)(i)(C) or (D) involving an unauthorized operation, manipulation, or tampering activity that results in interruption of normal operations at a production or utilization facility or results in an accidental criticality at a facility possessing a Category I quantity of SSNM could potentially constitute an allegation, including an allegation of criminal activity, requiring the convening of an Allegation Review Board.
8.2 1-Hour Shipment Notifications
The significant physical security events affecting shipment activities that must be reported within 1 hour are set forth in 10 CFR 73.1200(d)(1)(i)–(iv). Examples and clarifications of significant physical security events include, but are not limited to, the following:
The licensee receives a notification from law enforcement, the intelligence community, or other government officials of a credible threat of a potential hostile action or act of sabotage (including bomb threats) where the threat is not expected to occur within the next 12-hours or the time of occurrence is indeterminate. A licensee is not required to notify the NRC HOC if the NRC was the government agency that informed the licensee of the threat of a potential hostile action or act of sabotage.
Implementation of the licensee’s contingency response plan following receipt of a potential hostile action or act of sabotage, and the threat or action is not expected to occur within the next 12-hours or the time of occurrence is indeterminate. A licensee is not required to notify the NRC HOC if the NRC was the government agency that informed the licensee of a potential hostile action or act of sabotage that led to the contingency response plan’s implementation.
Licensees who are subject to 10 CFR 73.67 must meet the 1-hour notification requirement in 10 CFR 73.1200(d), but are not subject to the 15-minute notification requirement in 10 CFR 73.1200(b). Accordingly, these licensees must notify the NRC HOC within 1 hour of the discovery of an actual or suspected explosive or incendiary device or the detonation or ignition of such a device relating to a shipment activity.
9. 4-Hour Notifications
Under 10 CFR 73.1200(e) and (f), applicable licensees must notify the NRC HOC within 4 hours after the time of discovery of certain physical security events affecting licensee facilities and shipping activities. These 4-hour notifications are for those events that are less significant than the events subject to the 1‑hour notification requirement. The NRC’s development of a 4-hour notification requirement reflects the adoption of a risk-informed graded approach to reporting facility or shipping activity physical security events that reduces unnecessary burden.
9.1 4-Hour Facility Notifications
The physical security events affecting facilities that must be reported within 4 hours are set forth in 10 CFR 73.1200(e)(1)-(4). Examples and clarifications of such physical security events include, but are not limited to, the following:
The discovery of falsified identification badges, key cards, or other access-control devices that could allow unauthorized personnel entry into a PA, VA, MAA, or CAA.
The security force stages a strike or work slowdown.
The NRC staff should be aware that an event reported under 10 CFR 73.1200(e)(1)(iii) involving the willful, actual introduction of contraband into a PA that involves unauthorized firearms, explosives, incendiaries, or other dangerous materials could potentially constitute an allegation, including an allegation of criminal activity under 42 U.S.C. 2278a, requiring the convening of an Allegation Review Board.
For notifications under 10 CFR 73.1200(e)(1)(v)(A), authorized weapons are those that are specified in the licensee’s physical security plan.
Note: Weapons in the possession of on-duty law enforcement personnel during the course of their presence at the licensee’s facility are not considered to be uncontrolled authorized weapons.
For notifications required under 10 CFR 73.1200(e)(1)(vi), licensees should report unauthorized operation, manipulation, or tampering events involving security-related SSCs at reactors or security-related systems at Category I SSNM facilities that could prevent the licensee’s implementation of its protective strategy.
For notifications required under 10 CFR 73.1200(e)(3)(i), licensees need not report law enforcement responses to the licensee’s facility for minor incidents, such as traffic accidents.
9.2 4-Hour Shipment Notifications
The physical security events affecting shipments that must be reported within 4 hours are set forth in 10 CFR 73.1200(f)(1)-(2). Clarifications of such physical security events include, but are not limited to, the following.
Under 10 CFR 73.1200(f)(2), licensees must notify the NRC of an event involving “implementation of their security program for which a notification was made to local, State, or Federal law enforcement officials.” NRC staff does not view routine shipment-related notifications made to local, State, or Tribal officials in accordance with the requirements of 10 CFR Part 73 or NRC Orders as requiring an event notification under the requirement in paragraph (f)(2). Examples of such communications may include, but are not limited to, coordination of escort coverage, advance notification of shipments, shipment delay notifications, shipment departure notifications, and shipment arrival notifications.
NRC staff also does not view a licensee’s reporting of suspicious activities to local, State, or Federal law enforcement agencies in accordance with 10 CFR 73.1215 as requiring an event notification under the requirement in paragraph (f)(2).
10. 8-Hour Notifications
Under 10 CFR 73.1200(g) and (h), applicable licensees must notify the NRC HOC within 8 hours after the time of discovery of certain security program failure events at facilities and shipment activities, respectively. The NRC staff has determined that these security events are not likely to have a significant effect or potential effect on the physical security of a facility or shipment activity.
10.1 8-Hour Facility Notifications
The physical security events affecting facilities that must be reported within 8 hours are set forth in 10 CFR 73.1200(g)(1)(i)-(iii). Examples and clarifications of such physical security events include, but are not limited to:
A previously undiscovered design flaw in such systems, for example the failure of a required VBS to reposition to its secure configuration on a loss of power.
The loss of an alarm capability or locking mechanism at a SNM access control point or transfer portal that is not compensated for in accordance with the facility’s NRC-approved security plan.
An uncompensated event involving the failure of all PA lighting in combination with an outage of a PA perimeter intrusion detection, assessment, or delay system.
A strike or work stoppage by the security force that is imminent within the next 24 to 48 hours.
Discovery of improper or inadequate supervision over access-control equipment (e.g., badge fabrication, access‑control computers, keys, key cards, passwords, or cipher codes), but the event did not result in actual or attempted use of the equipment or media by an unauthorized individual to gain access into a PA, VA, MAA, or CAA.
For notifications required under 10 CFR 73.1200(g)(1)(i) or (ii), licensees should report unauthorized operation, manipulation, or tampering events involving safety related SSCs at reactors or events involving items relied upon for safety at Category I SSNM facilities, respectively.
The NRC staff recommends as a good practice that licensees should report under 10 CFR 73.1200(g)(1)(ii) unauthorized operation, manipulation, or tampering events that do not interrupt the normal operations of a production reactor facility (i.e., events that affects the normal production of SSNM, electricity, or process steam).
Licensees should not report events under 10 CFR 73.1200(g)(1)(ii) or (iii) where an otherwise trained and qualified individual conducts authorized operations or maintenance activities and the licensee subsequently determines that the individual’s qualifications permitting the activity had lapsed prior to his or her conducting the activity.
10.2 8-Hour Shipment Notifications
The physical security events affecting shipments that must be reported within 8 hours are set forth in 10 CFR 73.1200(h)(1)(i)-(ii).
11. Notifications for Enhanced Weapons
Under 10 CFR 73.1200(m), applicable licensees who have obtained enhanced weapons under 10 CFR 73.15 must notify the ATF, the NRC HOC, and the applicable LLEA in the event that any of these enhanced weapons are stolen or lost.
Under 10 CFR 73.1200(n), applicable licensees who have obtained enhanced weapons under 10 CFR 73.15 must notify the NRC HOC as soon as possible, but within 24 hours of receipt of an adverse action by the ATF regarding the licensee’s possession, receipt, transfer, transportation, or storage of enhanced weapons.
11.1 Immediate Notifications for Enhanced Weapons
Under 10 CFR 73.1200(m)(1)(i), licensees possessing enhanced weapons under 10 CFR 73.15 must immediately notify the ATF of any stolen or lost enhanced weapons. At the time of this RG’s issuance, the ATF requirement for immediate notification was located in ATF’s regulations under 27 CFR 479.141, “Stolen or Lost Firearms.” It is a licensee’s responsibility to understand and comply with all applicable ATF regulations associated with their possession of enhanced weapons. Consequently, NRC licensees are encouraged to discuss any questions on these notification requirements with ATF’s NFA Division staff in Martinsburg, West Virginia. Contact information for the NFA Division may be found on the ATF web site: https://www.atf.gov/contact/licensing-and-other-services.
11.2 1-Hour Notifications for Enhanced Weapons
Under 10 CFR 73.1200(m)(1)(ii), licensees possessing enhanced weapons under 10 CFR 73.15 must notify the NRC HOC as soon as possible, but not later than 1 hour, after a notification to the ATF of the discovery of any stolen or lost enhanced weapons possessed by the licensee.
11.3 24-Hour Notifications for Enhanced Weapons
Under 10 CFR 73.1200(n)(1), licensees possessing enhanced weapons under 10 CFR 73.15 must notify the NRC HOC, as soon as possible, but not later than 24 hours of the receipt of an adverse action by the ATF regarding the licensee’s possession, receipt, transfer, transportation, or storage of enhanced weapons.
Licensees should report adverse ATF actions that include, but are not limited to, the following:
Adverse inspection findings (e.g., notices of violation, nonconformance, or deficiency);
Enforcement actions (e.g., escalated enforcement, civil penalties, or orders); or
Other adverse notices (specific to the licensee) that would impact the licensee’s ability to possess or receive enhanced weapons.
Licensees who have voluntarily obtained a federal firearms license (FFL) from the ATF (in conjunction with obtaining enhanced weapons under Section 161A of the AEA) must also notify the NRC HOC as soon as possible, but within 24 hours, of the receipt of an adverse ATF action regarding the licensee’s FFL.
11.4 48-Hour Notifications for Enhanced Weapons
Under 10 CFR 73.1200(m)(1)(iii), licensees possessing enhanced weapons under 10 CFR 73.15 must notify the applicable LLEA as soon as possible, but not later than 48 hours of the time of discovery that any enhanced weapons have been stolen or lost. Licensees must notify LLEA officials via telephone or in person. This approach will permit LLEA officials to ask follow-up questions to assist in mitigating the public safety implications from the stolen or lost enhanced weapons.
When deciding which LLEA should receive this notification, the licensee should consider where the weapons were stolen or lost. The following two examples provide clarification on which LLEA to notify.
If the enhanced weapons are stolen or lost from a training range’s storage facility located away from the facility, then the licensee should notify the LLEA with jurisdiction over the training facility.
If the enhanced weapons are stolen or lost during the escorting of a shipment a significant distance from the facility (e.g., 1,600 kilometers (994 miles) away) or during the security team’s return to its home base via commercial aircraft, then the licensee should notify the LLEA with jurisdiction over the location where the theft or loss occurred, or is believed to have occurred.
12. Required Vehicle Barrier System
The notifications requirements in 10 CFR 73.1200(c)(1)(ii) and (e)(1)(viii) refer to a required vehicle barrier system (VBS). A VBS is considered required if its use at the licensee’s facility is necessary to implement the licensee’s protective strategy in accordance with the regulatory requirements in 10 CFR Part 73 or NRC orders. Some licensees may establish a VBS in the owner controlled area as part of an early warning system (OCA-EWS). If the licensee relies on and takes credit for this VBS in its physical security plan to implement its protective strategy, then such an OCA-EWS VBS is also considered a required VBS.
13. Unauthorized Personnel
Under 10 CFR 73.1200(e)(1)(i)-(ii), a licensee must notify the NRC HOC of an actual or attempted access to a facility’s PA, VA, MAA, or CAA by unauthorized personnel. Licensees should also notify the NRC of actual entries of unauthorized persons that are the result of the failure of the facility’s security barrier or control systems to prevent an unauthorized person from accessing the licensee’s PA, VA, MAA, or CAA. A licensee does not need to submit a notification in those cases where an individual was improperly granted unescorted access to a facility’s PA, VA, MAA, or CAA, based upon the individual providing inaccurate or false background information or by omitting derogatory information.
An individual who has been improperly approved for unescorted access is not considered an unauthorized person. Instead, the NRC staff recommends that the licensee should record the event under 10 CFR 73.1210(f) as a decrease in effectiveness of the security access control program (see Staff Regulatory Guidance position 18.2). The NRC staff also recommends that events involving an authorized person tailgating into a facility’s PA, VA, MAA, or CAA (in noncompliance with a licensee’s access control procedures) be recorded under 10 CFR 73.1210(f) as a decrease in effectiveness of the security access control program.
Under 10 CFR 73.1200(e), a licensee is not required to notify the NRC of actual or attempted entry of unauthorized persons into the licensee’s OCA. However, if a licensee determines that the unauthorized person’s actual or attempted entry into the OCA constitutes a suspicious activity then under 10 CFR 73.1215 the licensee must report this suspicious activity. Under 10 CFR 73.1215(c), licensees reporting a suspicious activity must notify the applicable LLEA, the FBI, and the NRC HOC of such activities. Separately, under 10 CFR 73.1200(e)(2), licensees must notify the NRC of events involving the “implementation of their security program for which a notification was made to local, State, or Federal law enforcement officials.” Since suspicious activity reports under 10 CFR 73.1215(c) already include a notification to the NRC HOC, the NRC staff views a separate notification to the NRC under 10 CFR 73.1200(e)(2) (regarding a notification to law enforcement officials) as duplicative; and therefore, unnecessary.
Under 10 CFR 73.1200(f)(1)(i)-(iv), a licensee must notify the NRC HOC of unauthorized personnel actually or attempting to gain access to a transport vehicle or to the material being transported. A licensee does not need to submit a notification in those cases where an individual was improperly granted unescorted access to a transport vehicle or to the material being transported, based upon the individual providing inaccurate or false background information or by omitting derogatory information. An individual who has been improperly approved for unescorted access is not considered an unauthorized person. Instead, the NRC staff recommends that the licensee should record such instances of improper granting of access under 10 CFR 73.1210(f) as a decrease in effectiveness of the security access control program (see Staff Regulatory Guidance position 18.2).
14. Retraction of Event Notifications
Under 10 CFR 73.1200(q), a licensee may retract an event notification made under 10 CFR 73.1200(a)-(h), (m), or (n) that it has determined to be invalid. A licensee may discuss the applicability of a particular notification or recording requirement in 10 CFR 73.1200 or 10 CFR 73.1210 to a specific security event with NRC staff, if time permits, before making the respective notification or record. Contacting the applicable NRC regional office is preferred.
Under 10 CFR 73.1200(q), a movement control center that is monitoring a shipment for a licensee may retract an event notification it has made under 10 CFR 73.1200(b), (d), (f), or (h) that it has determined to be invalid.
A licensee or its movement control center may base such a determination upon new information or relevant information received from an external entity subsequent to its initial notification. Examples of such a determination include, but are not limited to:
An event where the initial information is subsequently determined to be incorrect.
An event where the NRC’s Office of Investigations, a law enforcement agency, or the intelligence community determines that the event is innocent or innocuous (i.e., no malevolent intent was present). A licensee may rely on conclusions from such government or law enforcement agencies that malevolent intent was not present to serve as the basis for concluding an event notification is invalid. The NRC does not expect a licensee or its movement control center to have the necessary resources or technical capabilities to themselves assess whether a particular event was motivated by malevolent intent.
15. Items Relied Upon for Safety (IROFS)
Several of the notification requirements in 10 CFR 73.1200 refer to events involving unauthorized operation, manipulation, or tampering with any structures, systems, or components (SSCs). These events apply to facilities licensed under 10 CFR Part 70 that use the term “items relied upon for safety” (IROFS). Notification requirements referring to “any SSC” would include IROFS, but these notifications are not limited to IROFS.
The staff’s intent was not to give the term SSC any new meaning in the final rule. The intent was to require notification of unauthorized operation, manipulation, or tampering of any SSCs, not just “safety-related SSCs” as that term is defined in 10 CFR Part 50 or “items relied on for safety” as that term is defined in 10 CFR 70.4.
16. Security Event Notification Process
Under 10 CFR 73.1200(o), licensees must make the notifications required under 10 CFR 73.1200(a)-(h), (m), and (n) by telephone, within the specified timeliness limits. The timeliness requirement begins at the time of discovery of the event, as this term is defined in 10 CFR 73.2, “Definitions.” See Staff Regulatory Guidance position 1 for additional guidance regarding the term “time of discovery.”
Under 10 CFR 73.1200(o)(1) and (2), licensees may use any available communication system to telephonically contact the NRC HOC to make the notifications required under 10 CFR 73.1200 within the applicable timeliness requirement. Additionally, under 10 CFR 73.1200(p) and (q), licensees must notify the NRC of significant supplemental information and retraction of previous notifications using any available communication system.
16.1 Continuous Communications Channel
In response to a licensee’s event notification under 10 CFR 73.1200(a)-(h) and (m), the NRC may request that the licensee or its movement control center (MCC) establish a continuous communications channel. The NRC’s objective is to rapidly obtain accurate and current information on the security status of an event, especially in the cases of deteriorating facility or security conditions, high-significance events, or high-consequence events. A licensee or its movement control center may establish a requested communications channel via any available communications system. A licensee may locate the individual staffing the communications channel at a location it deems appropriate (e.g., an alarm station, technical support center, or emergency operations facility) and may relocate the individual to another appropriate location, if necessary.
Under 10 CFR 73.1200(o), a licensee must staff the communications channel with an individual from the licensee’s operations, security, or emergency response organizations. The individual should be knowledgeable of the facility or of the shipment and the licensee’s facility or transportation security procedures, as applicable. An MCC must staff the communications channel with an individual from the MCC. The individual should be knowledgeable of the shipment and the transportation security procedures.
16.2 Information Security Considerations During Event Notifications
Consistent with 10 CFR 73.22(f)(3), licensees making notifications of actual events under 10 CFR 73.1200 that contain SGI are exempted from the requirement to use secure communications technology. However, if a secure communications technology is readily available to the licensee, then the licensee should consider using this secure capability when notifying the NRC on a not to delay basis. For further guidance see Section B above, under “Event Notification Process,” and also Staff Regulatory Guidance position 3.
Separately, as also discussed under “Event Notification Process” in Section B above, licensees making notifications under 10 CFR 73.1200 that contain classified information must communicate such events to the NRC HOC using secure telecommunications equipment appropriate to the classification level of the notification. This includes both classified national security information (NSI) and classified Restricted Data (RD). Such secure communications equipment must meet the requirements of 10 CFR 95.39. The regulations in 10 CFR Part 95 do not contain provisions for emergency or exigent circumstance exceptions similar to those in 10 CFR 73.22(f)(3). Therefore, licensees must use secure telecommunications equipment to notify the NRC of a physical security event when the event notification contains classified information.
However, under 10 CFR 73.1200(o)(4)(ii) and (iii), if the licensee’s secure communications equipment is unavailable or inoperable (e.g., because of the nature of the security event), then the licensee must provide as much information as possible about the security event to the NRC HOC without disclosing classified information, so as to meet the licensee’s timely notification responsibilities under 10 CFR 73.1200. In addition, the licensee must indicate to the NRC that its secure communications capability is not available or operational. In such circumstances, licensees using a non-secure communications capability may be directed by the NRC emergency response management, in accordance with 32 CFR 2001.52(a), to provide classified NSI to the NRC over a non‑secure system, due to the significance of the ongoing security event. Under 10 CFR 73.1200(o)(4)(iii), a licensee submitting a written follow-up report for such an event must document this NRC direction and any classified NSI that was communicated non-securely. Under 10 CFR 73.1205(d)(2)-(3), a licensee must prepare and submit such a report as a classified document. However, licensees must only communicate classified RD using a secure communications capability (i.e., no exceptions exist).
16.3 Significant Supplemental Information
Under 10 CFR 73.1200(p), a licensee or a movement control center must notify the NRC of significant supplemental information. The length of time required to identify any supplemental information, assess its significance, and conclude that it is significant enough to warrant notification may vary greatly from event to event. Consequently, the NRC staff recommends as a good practice that once a licensee or a movement control center has determined that supplemental information is significant, then they should notify the NRC HOC of such information within a timeframe consistent with the timeliness requirement of the original notification.
The NRC staff recommends as a good practice that a licensee should notify the NRC of the negative results of bomb searches conducted either by the licensee or LLEA search teams as significant supplemental information.
17. Written Follow-Up Reports
Under 10 CFR 73.1205(a)(1), licensees must submit written follow-up reports within 60 calendar days after the licensee has made an event notification under 10 CFR 73.1200(a)-(h). However, the regulations in 10 CFR 73.1205(a)(2) identify several exceptions to this requirement. See “Written Follow-Up Reports” in Section B of this guide for details of these exceptions.
Additionally, 10 CFR 73.1205(a)(3) requires that a licensee need not submit a written follow-up report when the licensee has made a notification under 10 CFR 73.1200 and subsequently retracts the notification in accordance with 10 CFR 73.1200(q). However, if a licensee has already submitted a written follow-up report prior to retraction of the notification, then the licensee is required to submit a revised written follow-up report documenting the retraction and the basis for the retraction. Licensees should refer to Staff Regulatory Guidance position 14 for further direction. This revised report is necessary to ensure the completeness of the agency’s docketed history of the licensee’s communications with the NRC.
The following two examples further clarify for licensees and the NRC staff the timing considerations associated with this distinction:
On day 0, Licensee A makes an event notification to the NRC under 10 CFR 73.1200(c). On day 35 the licensee notifies the NRC under 10 CFR 73.1200(q) that it is retracting the event notification. Therefore, under 10 CFR 73.1205(a)(3)(i), Licensee A is not required to submit a written follow-up report for this event.
On day 0, Licensee B makes the same event notification to the NRC under 10 CFR 73.1200(c) and on day 59 submits a written follow-up report to the NRC. On day 85, the licensee notifies the NRC under 10 CFR 73.1200(q) that it is retracting this event notification. Consequently, under 10 CFR 73.1205(a)(3)(ii), Licensee B is required to submit a supplemental written follow-up report to the NRC to indicate that the original event notification was retracted and to document the basis for the retraction.
Under 10 CFR 73.1205(b)(2), licensees subject to 10 CFR 50.73 must submit written follow-up reports using NRC Form 366. Licensees not subject to 10 CFR 50.73 (e.g., those specific licensees subject to 10 CFR Parts 70 or 72) must submit written follow-up reports using a letter format instead of NRC Form 366.
A security event requiring a notification under 10 CFR 73.1200 may affect both a reactor facility and a co-located ISFSI facility. Rather than submitting a separate written follow-up report for both types of facilities, the licensees may submit a single written follow-up report using NRC Form 366. In such circumstances, the licensee should include all applicable docket numbers for the affected facilities.
18. Recordable Security Events and Conditions
Under 10 CFR 73.1210, an applicable licensee must record physical security events or conditions adverse to security within 24 hours of the time of discovery of such events and conditions. Licensees should refer to Staff Regulatory Guidance position 1 for further guidance regarding the time of discovery. The specific classes of licensees subject to this recordkeeping requirement are set forth in 10 CFR 73.1210(a)(1). However, certain licensees subject to 10 CFR 73.67 are exempted under 10 CFR 73.1210(h) from the recordkeeping requirements of 10 CFR 73.1210. Additionally, 10 CFR 73.1210(b)(5)-(7) also provides several exceptions to the recordkeeping requirements of 10 CFR 73.1210. Accordingly, certain licensees within the specific classes of licensees subject to 10 CFR 73.1210(a)(1) are exempt from this recordkeeping requirement.
18.1 Facility and Shipment Recordable Events and Conditions
Under 10 CFR 73.1210(c)(1)-(3) and (d)(1)-(2), a licensee must record within 24 hours certain identified physical security events or conditions at facilities. Under 10 CFR 73.1210(c)(4)-(7), a licensee must record within 24 hours certain identified physical security events or conditions during shipment activities.
For authorized live ammunition events under 10 CFR 73.1210(d)(1), licensees should consider a small quantity of ammunition to be 10 rounds or less.
For unauthorized live ammunition events under 10 CFR 73.1210(d)(2)(i), the regulations in 10 CFR 73.1210(d)(2)(ii)-(iv) provide direction on what is meant by the terms “a small quantity of live ammunition” (i.e., 5 rounds or less), “uncontrolled authorized ammunition,” and “unauthorized ammunition.”
Additionally, 10 CFR 73.1210(d)(3)(i) and (ii) provide exemptions to the ammunition recordkeeping requirements in 10 CFR 73.1210(d) for ammunition that is in the possession of law enforcement personnel performing official duties or for blank ammunition used by the licensee for training or security exercise or drill purposes.
18.2 Recordable Events and Conditions Regarding Decreases in Effectiveness
Under 10 CFR 73.1210(f), a licensee must record within 24 hours physical security events or conditions at facilities and during shipment activities regarding decreases in effectiveness of the physical security program. Examples and clarifications of such physical security events and conditions include, but are not limited to:
An event in which an individual was improperly granted unescorted access based upon the individual providing inaccurate or false background information or by omitting derogatory information. An individual who has been improperly approved for unescorted access is not considered an unauthorized person. This event applies when an individual gains entry into a PA, VA, MAA, or CAA; gains access to a vehicle transporting a Category I or Category II quantity of SSNM, a Category II quantity of SNM, SNF, or HLW; gains access to SSNM or SNM; or gains access to SGI. If indications of tampering, attempted sabotage, or theft or diversion are evident, the licensee should evaluate reportability under the 1-hr or 4-hr event notifications (see examples in Staff Regulatory Guidance positions 8 and 9).
NOTE: For this example, consistent with the guidance in RG 5.66, “Access Authorization Program for Nuclear Power Plants,” the time of discovery begins when the licensee completes an assessment of the intent of the inconsistencies; rather than the time of discovery direction contained in Staff Regulatory Guidance position 1.
A programmatic breakdown of the licensee’s processes or procedures for reviewing criminal history records checks and background information, involving multiple failures to seek or review relevant information that would have yielded an adverse decision on access to a facility, access to a transport vehicle, access to SSNM or SNM, or access to SGI.
Any other threatened, attempted, or committed act, not otherwise defined in 10 CFR 73.1210, that has resulted in or has the potential for decreasing the effectiveness of the facility’s or transport system’s physical security program below the level committed to in the licensee’s NRC‑approved physical security plans.
An event involving unauthorized or undetected access to the licensee’s “owner controlled area” surrounding the facility (e.g., a hunter during hunting season) is not required to be recorded under 10 CFR 73.1210. However, licensees should assess under RG 5.87 whether this access is a suspicious activity that is required to be reported under 10 CFR 73.1215.
18.3 Information Security Considerations for Recordkeeping
Under 10 CFR 73.1210(b)(3), a licensee may record physical security events or conditions adverse to security in either a standalone safeguards event log or in the licensee’s corrective action program. Some of these recorded events or conditions may contain SGI or classified information. Consequently, under 10 CFR 73.1210(b)(3)(ii), a licensee choosing to maintain records of physical security events and conditions adverse to security in an uncontrolled corrective action program database must ensure that the records contain sufficient detail and information to permit the licensee to effectively track, trend, and monitor these events or conditions and implement corrective actions to prevent recurrence without revealing SGI or classified information.
Under 10 CFR 73.1210(b)(3(iii)-(iv), a licensee may choose to divide such records between an uncontrolled corrective action program database and a (controlled) safeguards event log to maximize tracking, trending, and performance monitoring capabilities associated with their corrective action program without revealing SGI or classified information. Additionally, a licensee must ensure that any SGI or classified information contained in such records is created, stored, and handled in accordance with the requirements of 10 CFR 73.21 and 10 CFR 73.22 or 10 CFR Part 95, as applicable. Furthermore, a licensee must ensure that only personnel with a valid need to know are permitted access to any SGI or classified information contained in such records.
19. Events Involving Classified Information
Under 10 CFR 73.1200(t), a licensee must notify the NRC HOC of events associated with the deliberate disclosure, theft, loss, compromise, or possible compromise of classified documents, information, or material in accordance with 10 CFR 95.57, “Reports.” However, a single event may require both a physical security event notification and a classified information event notification. For example, the loss or theft of SSNM that has physical characteristics which are considered to be classified information. The loss or theft of this SSNM is a physical security event requiring notification under 10 CFR 73.1200. However, since the physical characteristics of the SSNM are also classified, the loss or theft of this material is also a loss of classified information requiring reporting under 10 CFR 95.57. If the report of such an event contains classified information, then the licensee should report the event to the NRC HOC in accordance with the communication procedure specified in Section III of Appendix A to Part 73.
As a good practice under the elimination of duplication provision in 10 CFR 73.1200(s), a licensee may make a single communication to the NRC HOC of an event that requires notifications under both 10 CFR 73.1200 and 10 CFR 95.57. When communicating with the NRC HOC, a licensee must identify each regulation under which the licensee is making the notification.
20. Superseded Guidance
The guidance contained in this RG supersedes the following previous NRC guidance documents regarding physical security event notifications. In particular, with respect to emergency response notifications for security-based events and hostile actions.
Bulletin 2005-02, “Emergency Preparedness and Response Actions for Security-Based Events,” (Ref. 22).
Regulatory Issue Summary 2006-12, “Endorsement of Nuclear Energy Institute Guidance ‘Enhancements to Emergency Preparedness Program for Hostile Action,’” (Ref. 23).
Generic Letter 1991-03, “Reporting of Safeguards Events,” (Ref. 24).
D. IMPLEMENTATION
The NRC staff may use this regulatory guide as a reference in its regulatory processes, such as licensing, inspection, or enforcement. The NRC staff does not expect or plan to require the use of this regulatory guide. However, should the NRC determine to require the use of this regulatory guide, such an imposition would not constitute backfitting, as that term is defined in 10 CFR 50.109, “Backfitting,” 10 CFR 70.76, “Backfitting,” or 10 CFR 72.62, “Backfitting”; affect the issue finality of an approval issued under 10 CFR Part 52, “Licenses, Certifications, and Approvals for Nuclear Power Plants”; or constitute forward fitting, as that term is defined in NRC Management Directive 8.4, “Management of Backfitting, Forward Fitting, Issue Finality, and Information Requests” (Ref.25), because reporting requirements are not included within the scope of the NRC’s backfitting or issue finality rules or forward fitting policy.
GLOSSARY
authorized weapon |
Weapons specified under the licensee’s physical security plan in the possession of licensee security personnel or stored in armories or ready-service lockers.
A service weapon in the possession of federal, state, or local law enforcement personnel. |
contraband |
Unauthorized firearms, explosives, incendiaries, or other dangerous materials (e.g., disease‑causing agents), which are capable of causing acts of sabotage against a licensed facility or licensed radioactive material, as specified under 42 U.S.C. 2284. Contraband items are banned from a licensee’s protected area, vital area, or materials access area.
For licensees that possess or conduct activities involving classified national security information or classified Restricted Data (RD), as defined in 10 CFR 95.5, contraband also means unauthorized electronic devices or unauthorized electronic media that are capable of facilitating acts of espionage; unauthorized communication, transmission, disclosure, or receipt of RD; or tampering with RD, pursuant to 18 U.S.C. 793 or 42 U.S.C. 2274-2276, respectively. |
classified national security information (NSI) |
Has the same meaning as the term defined in 10 CFR 95.5. |
classified Restricted Data (RD) |
Has the same meaning as the term defined in 10 CFR 95.5. |
enhanced weapon |
Any short-barreled shotgun, short-barreled rifle, or machine gun authorized under 10 CFR 73.15. Enhanced weapons do not include destructive devices as defined in 18 U.S.C. 921(a) (Ref. 26). |
greater than Class C waste (GTCC) |
Has the same meaning as the term defined in 10 CFR 72.3. |
high-level radioactive waste (HLW) |
Has the same meaning as the term defined in 10 CFR 72.3. |
hostile action |
An act directed at a licensee’s facility, shipment, or its personnel that includes the use of force to damage or destroy the facility or shipment, divert or steal special nuclear or radioactive material, take hostages, and/or intimidate the licensee to violate its NRC license or NRC regulations. This includes attacks using guns, explosives. projectiles, vehicles, or other devices used to deliver destructive force.
A hostile action should not be construed to include protests or other acts of civil disobedience. |
hostile force |
One or more individuals who are engaged in an assault directed at a licensee’s facility, shipment, or its personnel. |
imminent |
An event or condition should be considered imminent if it is likely to occur within the time periods specified in 10 CFR 73.1200(a), (b), (c), and (d). |
independent spent fuel storage installation (ISFSI) |
Has the same meaning as the term defined in 10 CFR 72.3. |
movement control center (MCC) |
Has the same meaning as the term defined in 10 CFR 73.2. |
production facility |
Has the same meaning as the term defined in 10 CFR 50.2. |
prohibited items |
Devices, items, and materials that the licensee has determined are not permitted in a licensee’s PA, VA, or MAA. Prohibited items do not include contraband. The licensee may specify any prohibited items in its physical security plan. |
security condition |
Any Security Event listed in the approved security contingency plan that constitutes a threat or compromise to facility security or transportation security, a threat to facility personnel or transportation personnel, or a potential degradation to the level of safety of the facility or transportation system. |
security event |
Any occurrence which represents an attempted, threatened, or actual breach of the security system; or a reduction in the physical protection program for the facility or transportation system. Security Events may be Security Incidents, Security Conditions or Hostile Actions. |
security incident |
Any Security Event listed in the approved security contingency plan that may result in communication with an LLEA or draw media attention. |
spent nuclear fuel (SNF) or spent fuel |
Has the same meaning as the term defined in 10 CFR 73.2. |
vehicle barrier system (VBS) |
A continuous barrier, which may include buildings, natural barriers, commercially available barriers, and any combination of these items, utilized to stop a land vehicle used as transportation to gain proximity to vital areas or used to transport a bomb (i.e., a vehicle borne improvised explosive device - VBIED). |
uncontrolled authorized weapon |
An authorized weapon per the licensee’s security plan that is not in the possession of authorized personnel or is not in an authorized weapons storage location.
|
Notes:
For additional security terms, users may wish to consult NUREG-2203, “Glossary of Security Terms for Nuclear Power Reactors,” (Ref. 27).
The terms “ammunition,” “handgun,” “rifle,” “machine gun,” “large‑capacity ammunition feeding device,” “semiautomatic assault weapon,” “short-barreled shotgun,” “short‑barreled rifle,” and “shotgun” have the same meaning as provided in the ATF’s regulations under 27 CFR 478.11, “Meaning of terms,” (Ref. 28).
REFERENCES3
U.S. Code of Federal Regulations (CFR), “Physical Protection of Plants and Materials,” Part 73, Chapter I, Title 10, “Energy”
CFR, “Domestic Licensing of Production and Utilization Facilities,” Part 50, Chapter I, Title 10, “Energy”
CFR, “Licenses, Certifications, and Approvals for Nuclear Power Plants,” Part 52, Chapter I, Title 10, “Energy”
CFR, “Domestic Licensing of Special Nuclear Material,” Part 70, Chapter I, Title 10, “Energy”
CFR, “Licensing Requirements for the Independent Storage of Spent Nuclear Fuel, High-Level Radioactive Waste, and Reactor-Related Greater Than Class C Waste,” Part 72, Chapter I, Title 10, “Energy”
Atomic Energy Act of 1954 (AEA), as amended, Section 161A, “Use of firearms by security personnel,” Title 42, United States Code (42 U.S.C.), Chapter 23, Division A, Subchapter XIII, § 2201a.
CFR, “Facility Security Clearance and Safeguarding of National Security Information and Restricted Data,” Part 95, Chapter I, Title 10, “Energy”
AEA, Section 224, “Communication of Restricted Data”; Section 225, “Receipt of Restricted Data”; and Section 226, “Tampering with Restricted Data”; 42 U.S.C., Chapter 23, Division A, Subchapter XVII, “Enforcement of Chapter”; §§ 2274-2276.
18 U.S.C. Section 793, “Gathering, transmitting or losing defense information”; Part I, Chapter 37; “Espionage and Censorship”; § 793.
CFR, “Exemptions and Continued Regulatory Authority In Agreement States and In Offshore Waters Under Section 274,” Part 150, Chapter I, Title 10, “Energy”
CFR, “Classified National Security Information,” Part 2001, Chapter XX, Subtitle B, Title 32, “National Defense.”
U.S. Nuclear Regulatory Commission (NRC), NUREG-1304, “Physical Security Event Notifications, Reports, and Recordkeeping,” Washington, DC.4 (ML16012A188)
NRC, Regulatory Guide (RG) 5.69, “Guidance for the Application of Radiological Sabotage Design-Basis Threat in the Design, Development and Implementation of a Physical Security Program that Meets 10 CFR 73.55 Requirements (U),” Washington, DC. (Non-Publicly available)5
NRC, RG 5.70, “Guidance for the Application of the Theft and Diversion Design-Basis Threat in the Design, Development, and Implementation of a Physical Security Program that Meets 10 CFR 73.45 and 73.46 Requirements (U),” Washington, DC. (Non-Publicly available)5
NRC, RG 5.86, “Preemption Authority, Enhanced Weapons Authority, and Firearms Background Checks,” Washington, DC.
NRC, “Enhanced Weapons, Firearms Background Checks, and Security Event Notifications Rule,” Federal Register, Vol. 8x, No. xxx: pp. xxxxx (xx FR xxxxx), Washington, DC, month day, 2022
CFR, “Physical Protection of Category 1 and Category 2 Quantities of Radioactive Material,” Part 37, Chapter I, Title 10, “Energy”
CFR, “Domestic Licensing of Source Material,” Part 40, Chapter I, Title 10, “Energy”
NRC, Form 366, “Licensee Event Reports (LER),” Washington, DC.
NRC, “Nuclear Regulatory Commission International Policy Statement,” Federal Register, Vol. 79, No. 132: pp. 39415-39418 (79 FR 39415), Washington, DC, July 10, 2014.
NRC, Management Directive (MD) 6.6, “Regulatory Guides,” Washington, DC, May 2, 2016 (ML18073A170).
NRC, Bulletin 2005-02, “Emergency Preparedness and Response Actions for Security-Based Events,” Washington, DC, July 18, 2005. (ML051740058)
NRC, Regulatory Issue Summary 2006-12, “Endorsement of Nuclear Energy Institute Guidance ‘Enhancements to Emergency Preparedness Program for Hostile Action,’” Washington, DC, July 19, 2006. (ML061530290)
NRC, Generic Letter 1991-03, “Reporting of Safeguards Events,” Washington, DC, March 6, 1991. (ML031140131)
NRC, MD 8.4, “Management of Backfitting, Forward Fitting, Issue Finality and Information Requests,” Washington, DC, September 20, 2019. (ML18093B087)
18 U.S.C. Section 921, “Definitions,” Part I, Chapter 44, “Firearms,” § 921.
NRC, NUREG-2203, “Glossary of Security Terms for Nuclear Power Reactors,” Washington, DC, February 2017. (ML17047A669)
CFR, “Commerce in Firearms and Ammunition,” Part 478, Chapter II, Title 27, “Alcohol, Tobacco Products and Firearms.”
1 The NRC created the terms “stand-alone preemption authority” and “combined preemption authority and enhanced weapons authority” in 10 CFR 73.15 to clarify the differences and interrelationship between these two authorities under Section 161A of the AEA. Refer to RG 5.86, “Preemption Authority, Enhanced Weapons Authority, and Firearms Background Checks,” for further information.
2 The NRC staff has temporarily withdrawn NUREG-1304. The NRC staff intends to hold a question and answer workshop with the public and interested stakeholders following implementation of 10 CFR 73.1200, 73.1205, and 73.1210. This workshop and the development of a revised NUREG 1304 will occur subsequent to the 300-day compliance period for licensees to implement these new physical security event notification regulations.
3Publicly available NRC published documents are available electronically through the NRC Library on the NRC’s public Web site at http://www.nrc.gov/reading-rm/doc-collections/ and through the NRC’s Agencywide Documents Access and Management System (ADAMS) at http://www.nrc.gov/reading-rm/adams.html. The documents can also be viewed online or printed for a fee in the NRC’s Public Document Room (PDR) at 11555 Rockville Pike, Rockville, MD. For problems with ADAMS, contact the PDR staff at 301-415-4737 or (800) 397-4209; fax (301) 415-3548; or email [email protected].
4The NRC withdrew NUREG-1304, Revision 0, issued February 1988 (ML16012A188) upon the publication of the agency’s final rule on “Enhanced Weapons, Firearms Background Checks, and Security Event Notifications.” Revision 1 of NUREG-1304 will be issued following a public Q&A workshop, which will be held after the extended compliance (implementation) period for the final rule.
5 Licensees with a need to know may request non-publicly available documents listed herein via their cognizant NRC licensing project manager.
Written suggestions regarding this guide or development of new guides may be submitted through the NRC’s public Web site in the NRC Library at http://www.nrc.gov/reading-rm/doc-collections/, under Document Collections, in Regulatory Guides, at http://www.nrc.gov/reading-rm/doc-collections/reg-guides/contactus.html,
Electronic copies of this RG, previous versions of this guide, and other recently issued guides are also available through the NRC’s public Web site in the NRC Library at http://www.nrc.gov/reading-rm/doc-collections/, under Document Collections, in Regulatory Guides. This RG is also available through the NRC’s Agencywide Documents Access and Management System (ADAMS) at http://www.nrc.gov/reading-rm/adams.html, under ADAMS Accession Number (No.) ML17131A285. The regulatory analysis may be found under ML19045A003. The associated draft Guide DG-5019, Rev. 1 may be found under ML100839413 and the staff responses to the public comments on DG-5019, Rev. 1 may be found under ML17123A319. |
| File Type | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| Author | Wase, Alana |
| File Modified | 0000-00-00 |
| File Created | 2023-08-24 |
© 2026 OMB.report | Privacy Policy
